Apple ID Scam: Part 2
Sunday, January 25. 2015
Asking for people's password seems to be a very lucrative business. See this clip from Jimmy Kimmel Live: What is Your Password? Of course it is a scripted show and nothing they make you believe happened for real didn't, but still: its very funny one and there is a lot of truth behind that one. People do give out their passwords way too easy.
A while back I wrote about a previous attempt to phish for Apple ID. Also this scam for Google passwords turned out to be a great success for the author of the scam.
Anyway, this time I got an email from Philippines saying:
Dear Apple Customer,
We just need to verify that this email address belongs to you. Simply click the link below and sign in using your Apple ID and password.
Verify Now >
Wondering why you got this email?
It's sent when someone adds or changes a contact email address for an Apple ID account. If you didn't do this, don't worry. Your email address cannot be used as a contact address for an Apple ID without your verification.
For more information, see our frequently asked questions.
Thanks,
Apple Customer Support
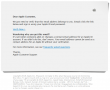
This wasn't an especially well executed scam. Scamsters had cracked some innocent (but incapable sysadmin) person's Joomla 2.5.27 installation and injected "bonus" content into it. This is how the site looked like:
Convincing, but only if you keep your eyes out of the address-bar. This is a classic: no HTTPS, quite a weird path. Personally I don't understand how anybody could fall into this trap. Still many do, and get their iPhone contents spread all over the internet.
When discussing with non-security people about these recent account hijackings, I often get a reply of "I don't have anything to hide!". Still my standard reply to that is, "Well, gimme your password, then". They never do. ![]()
Google Drive scam
Thursday, January 22. 2015
"A friend" received and e-mail with badly translated text in it. The translation into Finnish was so bad that I couldn't even read it myself. But as always, there was something to lure innocent user to click. A shortened link.
In this case, the link wasn't especially dangerous. It didn't exploit any security flaws or didn't do anything dangerous. It simply landed on some innocent victim's WordPress 3.9.3 site with some "bonus" material injected into it. At the time of writing, latest WP version is 4.1.
The users were presented a "Google Drive login" page: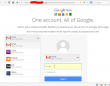
Would you enter your credentials into that one?
Well ... somebody did. That somebody didn't have 2-factor authentication in use. It resulted in similar spam sent to every single person found from address book or recent e-mails. It is yet to be determined, what else happened.
The login screen is a no-brainer: it has no HTTPS enabled, the address bar clearly states something else than Google, there is no way this site was created or endorsed in any way by Google. All the alarms should be ringing when one sees that kind of page ... but no. ![]()
And for god's sake: enable the 2FA now! Even this scam would have been prevented if one would have been in use.