Goodbye CAcert.org - Welcome Let's Encrypt!
Sunday, March 11. 2018
A brief history of CAcert.org
For almost two decades, my primary source for non-public facing X.509 certificates has been CAcert.org. They were one of the first ever orgs handing out free-of-charge certificates to anybody who wanted one. Naturally, you had to pass a simple verification to prove that you actually could control the domain you were applying a certificate for. When you did that, you could issue certificates with multiple hostnames or even wildcard certificates. And all that costing nothing!
The obvious problem with CAcert.org always was, that they were not included in any of the major web browsers. Their inclusion list at https://wiki.cacert.org/InclusionStatus is a sad read. It doesn't even have Google Chrome, the most popular browser of current time in the list. The list simply hasn't been updated during the lifetime of Chrome! On a second thought looking it bit closer, the browser inclusion status -list is an accurate statement how CAcert.org is doing today. Not so good.
Wikipedia page https://en.wikipedia.org/wiki/CAcert.org has a brief history. Their root certificate was included in initial versions of Mozilla Firefox. When CA/Browser Forum was formed back in 2005 by some of the certificate business vendors of that time to have a set of rules and policies in place regarding web site certificates and the issuence policies, they kicked pretty much everybody out by default. Commerical vendors made the cut back in, but CAcert.org simply couldn't (or wouldn't) comply with those and withdrew their application for membership. The reson for CAcert.org not being able to act on anything is that the entire org is (and has been for a long time) pretty much dead. All the key persons are simply busy doing something else.
Today, the current status of CAcert.org is, that their certs are not trusted and signed by non-accepted hash algorithms. Over an year ago, there was a blip of activity and they managed to re-sign their root certificate with SHA-256, but to me it looks like they exhausted all the energy on the actual signing and newly signed root certs were never published. I wrote a post about how to actually get your hands on the new root certificate and install that to your machines.
Today, when CA/Browser Forum is mostly controlled by Google and Mozilla, a stalled CAcert.org would not be accepted as a member and at the same time there is huge pressure to start using properly signed and hashed certificates on all web traffic, I've run out of road with CAcert.org. So, for me, it's time to move on!
A brief history of Let's Encrypt
Two years ago, the certificate business had been hit hard. I collected a number of failures in my blog post about What's wrong with HTTPS. Roughly at the same time also Electronic Frontier Foundation (EFF) saw the situation as not acceptable. Businesses wanted serious money for their certs, but were not doing an especially good job about trustworthy business practices. With help of some major players (including Mozilla Foundation, Akamai Technologies, Cisco Systems, etc.) they created a non-profit organization for the sole purpose of issuing free-of-charge certificates to anybody who wanted one called Let's Encrypt.
They managed to pull that off, in a very short period of time, they become the most prominent certificate authority in the Internet. At least their product price is right, €0 for a cert. And you can request and get as many as you want to. There are some rate limits, so you cannot denial-of-service them, but for any practical uses, you can get all your certs from them. For free!
The practical benefit for Let's Encrypt operation is, that number of web server in The Net having HTTPS enabled has been rising. Both EFF and CA/Browser Forum is strongly suggesting, that all HTTP-traffic should be encrypted, aka. HTTPS. But the obvious hurdle in achieving that, is that everybody needs to have a certificate in their web server to enable encryption. Given Let's Encrypt, now everybody can do that! EFF has stated for long time, that having secure communications shouldn't be about money, it should be about your simply wanting to do that. The obvious next move is, that in coming years CAB Forum will announce, that all web traffic MUST be encrypted. However, we're not quite yet there.
Breifly on Let's Encrypt tech
Since they wanted to disrupt the certificate business, they abandoned current operation procedures. Their target is to run the entire request/issue-process fully automated and do that in a secure manner. To achieve that, they created a completely new protocol for Automatic Certificate Management Environment, or ACME. The RFC draft can be seen at https://datatracker.ietf.org/doc/draft-ietf-acme-acme/.
Their chain of trust (taken from https://letsencrypt.org/certificates/) is bit confusing to me:
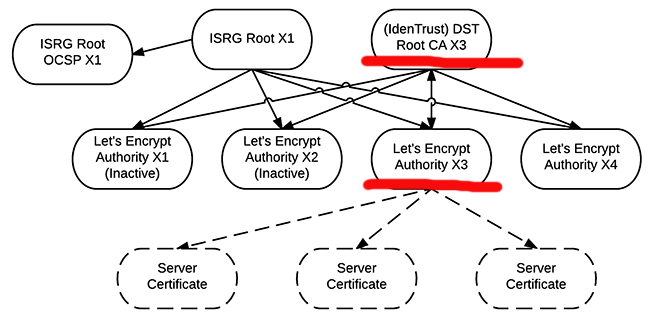
As the root certificate, they use Digital Signature Trust Co. (red line with Identrust DST Root CA X3). That's something your browser has had for years. So, ultimately they didn't have to add anything. When you request a certificate, it is issued by the intermediate authority Let's Encrypt Authority X3. And as the bottom level is your very own Server Certificate.
However, I don't undertand why there is ISRG Root X1 to double-sign all the intermediates, and signing only their OCSP-data. My computers don't have that root certificate installed. So, what's the point of that?
As a note:
This is the recommened and typical way of setting up your certificate chain, nothing funny about that. For a layman, it will strike as overly complex, but in X.509-world things are done like that for security reasons and being able to "burn" an intermediate CA in a split second and roll forward to a new one without interruptions and need to install anything to your machines.
What the actual connection between Let's Encrypt and Digital Signature Trust Co. (IdenTrust) is unclear to me. If somebody knows, please drop a comment clarifying that.
My beef with Let's Encrypt
Short version: It's run by idiots! So, Let's not. ![]()
Long version:
- Tooling is seriously bad.
- The "official" python-based software won't work on any of my machines. And I don't want to try fixing their shit. I just let those pieces of crap rot.
- To me, Acme Inc. is heavily associated with Wile E Coyote
- Mr. Coyote never managed to catch the Road Runners. Many times it was because the Acme Inc. manufactured equipment failed to function. https://en.wikipedia.org/wiki/Acme_Corporation

- Mr. Coyote never managed to catch the Road Runners. Many times it was because the Acme Inc. manufactured equipment failed to function. https://en.wikipedia.org/wiki/Acme_Corporation
- Did I mention about the bad tools?
- Every single tool I've ever laid my hands on wants to mess up my Apache and/or Nginx configuration.
- I have a very simple rule about my configurations: DON'T TOUCH THEM! If you want to touch them, ask me first (at which point I can reject the request).
- There seems to be no feasible way of running those crappy tools without them trying to break my configs first.
- Most 3rd-party written libraries are really bad

- There are libraries/tools for all imaginable programming languages implementing parts/all of ACME-protocol.
- Every single one of them are either bad or worse.
- Certificate life-span i 90 days. That's three (3) months!
- The disruptive concept behind this is, that you need to renew your certs every 60 days (or at max 90 days). For that to happen, you will need to learn automation. Noble thought, that. Not so easy to implement for all possible usages. The good thing is, that if ever achieved, you won't have to suffer from certificates expiring without you knowing about it.
- As an alternative, you can get a completely free-of-charge SSL certificate from Comodo, a member of Let's Encrypt, which is valid for 90 days, but you have to do it manually using Comodo's web GUI. See: https://ssl.comodo.com/free-ssl-certificate.php if you want one.
- I won't list those commercial CAs who can issue you a 30 day trial certificate for free here, because the list is too long. So, if you just want a short-lived cert, you have been able to that for a long time.
- They're not able to issue wildcard certificates, yet.
- This is on the works, so mentioning this is hitting them below the belt. Sorry about that.
- From their test-API, you can get a wildcard certificate, if you really, really, really need one. It won't be trusted by your browser, but it will be a real wildcard cert.
- Original release date for ACME v2 API in production was 27th Feb 2018, but for <insert explanation here> they were unable to make their own deadline. New schedule is during Q1/2018. See the Upcoming Features -page for details.
My solution
It's obvious, that I need to ditch the CAcert.org and the only viable one is Let's Encrypt (run by idiots). To make this bitter choice work for me, after evaluating a number of solutions, I found a reasonable/acceptable tool called acme.sh. This tool is written with Bash and it uses curl for the ACME access. The author publishes the entire package in Github, and I have my own fork of that, which doesn't have a line of code even thinking about touching my web server configurations. You can get that at https://github.com/HQJaTu/acme.sh
Since I love Rackspace for their cloud DNS. I even wrote a Rackspace API Cloud DNS -plugin for acme.sh to make my automated certificate renewals work seamlessly. After carefully removing all other options for domain verification, it is 100% obvious, that I will do all of my ACME domain verifications only via DNS. Actually, for wildcard certs, it is the only allowed approach. Also, some of the certificates I'm using are for appliance, which I carefully firewall out of the wild wild web. Those ridiculous web site verification wouldn't work for me anyway.
And for those, who are wondering, Why Rackspace Cloud DNS? The answer is simple: price. They charge for $0/domain. That is unlike most cloud/DNS service providers, who want actual money for their service. With Rackspace you'll get premium GUI, premium API, premium anycast DNS servers with the right price, free-of-charge. You will need to enter a valid credit card when you create the account, but as they state: they won't charge it unless you subscribe to a paid service. I've been running their DNS for years, and they never charged me once. (If they see this blog post, they probably will!)
What I'm anxiously waiting is the ACME v2 API release, which is due any day now. That will allow me to get my precious wildcard certificates using these new scripts.
Now that my chips are in, its just me converting my systems to use the Wile E Coyote stuff for getting/renewing certs. And I will need to add tons of automation with Bash, Perl, Ansible, Saltstack, ... whatever to keep the actual servers running as intened. Most probably, I will post some of my automations in this blog. Stay tuned for those!


Alex on :
Yes, there are plugins that promise to automagically deal with your Apache or Nginx config, but you can also do everything in a 100% manual mode.
Jari Turkia on :
Those changes are very likely to both not work for ACME verification and break my stuff. The naive approach will work for Joe 'the beginner' User, because he simply doesn't know any better and is happy to have somebody do the heavy lifting for him. I have no problem using DNS-verification, but that option was never offered to me.
That's why I refuse to run any shit that event thinks about touching my files. I need to KNOW that it doesn't make any changes that I didn't order for.
To get a positive approach into this, please do recommend me a good Let's Encrypt tool. I will check it out and see what it would do and reply my thoughts about your recommendation.
Hans Dampf on :
You are not happy with Let's encrypt neither; you "don't want to try fixing their shit". Knowing how much money and emplyees they have, I wouldn't neither. On the other hand, five people as you giving a hand to CAcert's software team, would speed up thing extraordinarily.
Jari Turkia on :
CAcert is a (mis)management mess. Original idea was both noble and fresh at the time. Offering free-of-charge certs to anybody who wanted one was a magnificent idea! I joined CAcert immediately after discovering its existence. It didn't take long to realize, that Mr. Groth was running the show almost by himself. Changes were made to make the organization trustworthy to pass the upcoming Mozilla CA inclusion audit. And that made everything turn into the mess CAcert is currently. Has been for a decade, to be exact. Incapable of making even a list of requirements to pass the inclusion audit.
How do you motivate 5 persons like me to volunteer when its evident, that there is no functioning management? I would like to, but unfortunately for you, I can smell a losing fight without looking into the details too hard.
Get the cert included by Mozilla, became a member of CAB and I'll help you implement ACME. Sound good?
Peter Muster on :
That said, your offer is a more politely worded no - unless you are funding the audit?
Jari Turkia on :
Unfortunately, the competition (mainly Let's E, ZeroSSL and Google Public CA) have deep pockets and can afford such expensive audits as many times needed.
This kinda proves my point. If CAcert cannot even afford / is unable to raise money for basic audits there are exactly two options: 1) call it quits, 2) come up with a plan to make the audit happen. This current stale state of doing nothing isn't in the list.
Oliver Leitner on :
the tools for searching your configs wherent even installed by grabbing certbot on the server.
im always open for better solutions, got any?
Jari Turkia on :
As I wrote: my weapon-of-choice still is acme.sh. A bash-script. I do run it from my own GitHub-repo where I do yank out the lines of code with anything to do with thinking about attempts to read my configurations. I refuse to run anything that has the potential to think my configurations.
I need a tool for the certificates, nobody else than me touches my configs!