Java 1.7 update 51 breaking Cisco ASDM login
Monday, March 10. 2014
One day I needed to drill a hole to a Cisco firewall. I went to Adaptive Security Device Manager and could not log in. Whaat?!
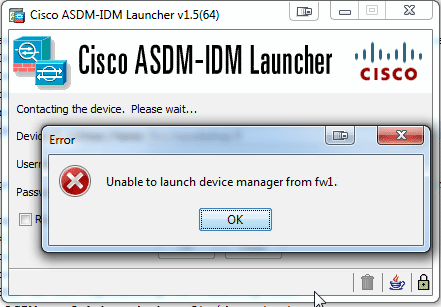
It did work before, but apparently something changed. Sneak peek with Wireshark revealed that SSL handshake failed. Java console has something like this in it:
java.lang.SecurityException: Missing required Permissions manifest attribute in main jar: https://dm-launcher.jar
at com.sun.deploy.security.DeployManifestChecker.verifyMainJar(Unknown Source)
at com.sun.deploy.security.DeployManifestChecker.verifyMainJar(Unknown Source)
at com.sun.javaws.Launcher.doLaunchApp(Unknown Source)
at com.sun.javaws.Launcher.run(Unknown Source)
at java.lang.Thread.run(Unknown Source)
and:
javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: Java couldn't trust Server
at sun.security.ssl.Alerts.getSSLException(Unknown Source)
at sun.security.ssl.SSLSocketImpl.fatal(Unknown Source)
at sun.security.ssl.Handshaker.fatalSE(Unknown Source)
at sun.security.ssl.Handshaker.fatalSE(Unknown Source)
at sun.security.ssl.ClientHandshaker.serverCertificate(Unknown Source)
at sun.security.ssl.ClientHandshaker.processMessage(Unknown Source)
Little bit of googling revealed Issues Accessing ASDM at Cisco's learning network and Cisco ASDM blocked by Java? at spiceworks.com. So I wasn't alone with the problem. Oracle's release notes for update 51 revealed a number of changes to earlier versions. Java is still piece of shit, but they're trying to fix it. Too little, too late. It is very unfortunate that I have to have Java Runtime installed and use it for a number of important applications. Now Oracle is making radical changes to JRE to improve its flaky security and these customer companies like Cisco cannot keep up with the changes.
Anyway, enough rant, here is how to fix it. The idea is to take the self-signed certificate from the Cisco firewall and import it for Java. This is yet another nice feature of a Windows-computer. There needs to be separate a separate certificate store for operating system, browser and Java.
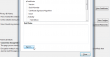
First go to web-interface of the Cisco appliance. Internet Explorer cannot export a certificate from a web site, so use a Firefox or Chrome or pretty much any other browser. Save the certificate to a file. Like this:
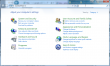
When you have the file, go to Control Panel on Windows:
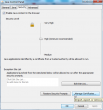
Select Java and Security-tab:
From there you can find Manage Certificates. Import the certificate-file from there:
It is very, very important that you first select Certificate Type: Secure Site. Any other certificate type won't fix the problem.
On the security-tab there is an exception list for certificates. Adding an exception won't fix this, since the problem is with the fact that the certificate is self-signed.
Now login works again.
When I first encountered this issue, I asked help from couple of guys who are very familiar with Cisco IOS (not Apple iOS). The initial response was "What is ASDM?" ![]() Apparently the GUI is not the expert's way to go.
Apparently the GUI is not the expert's way to go.


Jingyao Huang on :
Jari Turkia on :
But I share, because I care.
Monk on :
Nice explanation.
Do you permit a repost with backlink to here ?
Jari Turkia on :
Feel free to repost. All I'm asking is to properly credit me as an author. A link to the original would also be appreciated, but is not a requirement.
On weekly basis I find my articles copy/pasted to discussion forums etc. without any credits at all. Not nice.
M.Ezzat on :
Jari Turkia on :
Susanna Y on :
Jari Turkia on :
I share because I care.
Jack on :
Jari Turkia on :
If you have never attempted that, then you should. If you have blocked the HTTPS-interface of your firewall management, then your job just turned couple of notches more difficult.
Jack on :
Jari Turkia on :
And since the access to there is managed by your web browser, the only thing that can go wrong is that you blocked your access there.
In general, the idea is just to retrieve the self-signed certificate and there are a number of options for doing that. On a Linux prompt you can do that with:
openssl s_client -connect asa-ip-address:443
command, or something similar.
Jack on :
Thanks much.
Jack
Jari Turkia on :
Its nice to hear that you figured that out.
Jack on :
Thanks much - again!
Jack
Jari Turkia on :
My only advice would be something that you tried already. In Java Control Panel's General tab sheet, there is the Temporary Internet Files. Typically removing all temp files will result in better functionality. You didn't specify if you erased temp files from your browser or from Java, but that's pretty much the only thing you can do besides reinstalling the JRE.
Jack on :
Joel Cesar Zamboni on :
Jari Turkia on :
dixit on :
after i have been searching for 2days.
Jari Turkia on :
"DR" "UNK" on :
Can you give a cook book style explanation on obtaining the Certificates. I believe this is my hurdle right now.
I have inherited a freaking mess here and I been working on trying to get this right for days......
Many Many Many THANKS in advance.....
Jari Turkia on :
All the information is in the original blog post. You need to access the firewall's management console with your favorite web browser and export the cert.
Knowing the address of your firewall should be the biggest hurdle. Exporting the certs is easy, you can practice that with any site using one.
Jari Turkia on :
bw on :
raja on :
wind10 pro
java 7
gns3 2.1.8
asdm647
asa842
tftp32
Jari Turkia on :