SSH connection fails
Thursday, January 8. 2015
One day I was SSHing into my ArchLinux, but it didn't succeed. The thing didn't even attempt authentication. It said:
Key exchange failed.
No compatible cipher. The server supports these ciphers: AES-128-CTR,AES-192-CTR,AES-256-CTR,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
That was surprising. It did work earlier. Ok, Arch is one of those bleeding-edge distros. It does use newest of the new stuff in it. My client is SecureCRT and it has been serving me well for years, actually over decade. I had to confirm the connectivity with Cygwin's OpenSSH client. It worked just fine. Connection opens, no grievance from there. So, something must be wrong with my SecureCRT's settings. This is what the cipher list looked like in Session Options -> Connection -> SSH2 -> Advanced: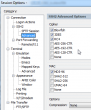
Darn! It didn't have the newest big guns enabled. I must have ran too many upgrades to it. Apparently the upgrade doesn't enable that in my settings. I manually changed it into: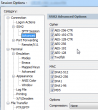
... which made the connection succeed.
I checked the server version number and it was OpenSSH_6.7p1. The sshd_config manual says:
Ciphers
The default is:
aes128-ctr,aes192-ctr,aes256-ctr,
aes128-gcm@openssh.com,aes256-gcm@openssh.com,
chacha20-poly1305@openssh.com
Also I found OpenSSH 6.7 release notes saying:
Changes since OpenSSH 6.6
=========================Potentially-incompatible changes
* sshd(8): The default set of ciphers and MACs has been altered to
remove unsafe algorithms. In particular, CBC ciphers and arcfour*
are disabled by default.
So the defaults did change in that upgrade. I checked Fedora 20 defaults and they are:
aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,
aes128-gcm@openssh.com,aes256-gcm@openssh.com,
aes128-cbc,3des-cbc,blowfish-cbc,cast128-cbc,aes192-cbc,
aes256-cbc,arcfour
That explains the change!

