First B593 s-22 exploit: Setup FTP to get /var/sshusers.cfg
Monday, February 23. 2015
I have a new version of B593_exploit.pl published. See this article about previous info.
This version has s-22 FTP hack added to it. u-12 has the classic FTP USB-share flaw where it is possible to create a FTP share of the /. Unfortunately in this box Huawei guys made the web GUI a bit smarter, you cannot do such a nice share anymore. The fortunate part is, that the guys don't check for that at the save. ![]() If you manage to lure the ../.. past the GUI, you can do it. That's what the exploit is about.
If you manage to lure the ../.. past the GUI, you can do it. That's what the exploit is about.
Example run:
./B593_exploit.pl 192.168.1.1 admin --ftp-setup \ ftpuser ftppassword
That command will share the first USB-device found at the filesystem root of the box. You have to have a physical USB-storage attached. It doesn't have to have anything on it and it won't be affected during the process. But setting a path will fail, if there is no USB-storage.
I had problems with the FTP-client, it kept complaining about FTP passive mode. I switched the client into NcFTP and that solved my problem.
When in the box the SSH passwords are at the classic /var/sshusers.cfg. If configuration is of interest to you, it can be found from /app/curcfg.xml. When the admin user's password is known, it is only a trivial task to SSH into the box and gain a shell access.
While looking around the box, I got carried away with the lteat-command. I managed to brick the box. ![]() But that's an another story.)
But that's an another story.)
iPhone (cell) Field Test mode
Saturday, February 21. 2015
A reader of this blog contacted me and wanted me to take a look at his Huawei E5186. During the meeting he showed the Field Test mode of his iPhone. I haven't done any iPhone hacks, and had never heard of such thing. In this mode you can see details of the cellular connection. It is completely limited to that, there is no "root"-mode, nor details about Wi-Fi connection, nor details of the phone itself. But if any of the SIM, GSM, UMTS or LTE details are of interest, this one is for you.
Every iPhone has this. Really! There are details of this Field Test mode in The Net from year 2009 (iPhone 3GS), maybe earlier if you'd really want to look close. My iPhone 6 has this, so I'm pretty sure your (whatever model) has it too.
How to get there? Easy. Dial *3001 # 12345#*. Like this:
As a result you will see either the 2G/3G (GSM/UMTS) or 4G (LTE) Field Test menu:
As you can see, the 2G/3G menu has more stuff in it. It is because this is the really old stuff back from the 90s. LTE menu is light, as it is the 2010s spec. Please remember, that it is a snapshot of the situation when menu was opened.
Also notice how there is no more bars on top of the screen, there is a number in dBm. The number will indicate RSSI (in 2G) or RSCP (in 3G) or RSRP (in 4G). See article Some GSM, UMTS and LTE Measurement Units for clarification of the units.
RSSI translation:
- -40 dBm - theorethical max., you won't get this even if you'd be right next to the cell tower
- -50 to -75 dBm - High
- -76 to -90 dBm - Medium
- -91 to -100 dBm - Low
- -101 to -120 dBm - Poor
RSRP translation:
- theorethical max. ? dBm
- -75 and -88 dBm - Very High
- -89 and -96 dBm - High
- -97 and -105 dBm - Medium
- -106 and -112 dBm - Low
- -113 and -125 dBm - Poor
As I didn't find much information about the actual contents of these menus, I'll try to gather here a comprehensive list. Not all of the items have a value in my phone, if there is a value recorded, but I don't know what it is for, there is a ?.
| Menu / Submenu | Description | ||||
|---|---|---|---|---|---|
| SIM Info | |||||
(sub level 1) |
EF-FPLMN | ||||
| EF-ICCID | |||||
| EF-OPLMNAcT | |||||
| EF-HPPLMN SEARCH PERIOD | |||||
| EF-MSISDN | |||||
| EF-3GPP MAIL BOX DIALING NUMBER | |||||
| EF-ACCESS CONTROL CLASS | |||||
| EF-OPERATOR PLMN LIST | |||||
| EF-ACTING HPLMN | |||||
| EF-ADMINISTRATIVE DATA | |||||
| EF-RAT MODE | |||||
| EF-LOCI | |||||
| EF-GPRS/PS-LOCI | |||||
| PDP Context Info | (List) Packet Data Protocol (PDP) Context (in GPRS), see http://developer.nokia.com/community/wiki/PDP for details of PDP | ||||
| APN | Access Point Name: Connection setting | ||||
| IPv4 | IPv4 address of the access point to connect to | ||||
| GSM Cell Environment | [UMTS only] 2G/2.5G information | ||||
| GSM RR Info | |||||
| DTX Used | ? | ||||
| RR State | |||||
| Rx Quality Sub | |||||
| RR Mode | |||||
| RR Sub State | |||||
| Serving Rx Level | |||||
| DRX used | |||||
| RR Status | |||||
| Rx Quality Full | |||||
| GSM Cell Info | |||||
| GSM Serving Cell | |||||
(sub level 3) |
C1 Value | ||||
| RSSI | |||||
| ARFCN | Absolute radio-frequency channel number | ||||
| Cell ID | http://en.wikipedia.org/wiki/Cell_ID Gather MCC, MNC, LAC and go http://opencellid.org/ to see where you are at |
||||
| Mobile Allocation | |||||
(sub level 4) |
ARFCNs | (List) | |||
| HSN | |||||
| C2 Value | |||||
| BSIC | ? bits | ||||
| MA Dedicated ARFCN | |||||
| Neighboring Cells | (List) | ||||
| GPRS Information | |||||
| Priority Access Threshold | ? | ||||
| SI13 Location | ? | ||||
| Ext Measurement Order | |||||
| Access Burst Type | ? | ||||
| DRX Timer Max | ? | ||||
| Network Operating Mode | ? | ||||
| PBCCH Present | |||||
| Count LR | |||||
| Packet PSI Status | |||||
| PFC Supported | ? | ||||
| Cell Reselect Hysteresis | |||||
| Count HR | |||||
| Packet SI Status | |||||
| Network Control Order | ? | ||||
| T3192 Timer | http://www.rfwireless-world.com/Terminology/GSM-timers.html [milliseconds] | ||||
| UMTS Cell Environment | [UMTS only] 3G information | ||||
| Neightbor Cells | |||||
| Active Set | (List) | ||||
| Detected Set | (List) | ||||
| Monitored Set | (List) | ||||
| UMTS Set | (List) The only one I have anything listed | ||||
| Scrambling Code | Your "identifier" in the cell. See UMTS Quick Reference - Scrambling Code for more info | ||||
| RSCP | Received signal code power: The number on top left of your screen. See UARFCN below. | ||||
| Energy Per Chip | EcNo: RSCP divided by RSSI. See Some GSM, UMTS and LTE Measurement Units for details about RCSP and EcNo. | ||||
| UARFCN | See UMTS RR Info below. In this set one of the cells has same scrambling code as UMTS RR Info has. That cell has the exact same RSCP what is displayed as your received signal strenght. | ||||
| Virtual Active Set | (List) | ||||
| GSM Set | (List) | ||||
| HSDPA Info | |||||
| Version | |||||
| Primary HARQ Process | |||||
| Sub Frames | |||||
| Secondary HARQ Process | |||||
| Carrier Info | |||||
| UMTS RR Info | Information of the Radio Relay (cell tower) who is serving you | ||||
| UARFCN | UTRA Absolute Radio Frequency Channel Number: The channel number you're currently at. Decimal number, see http://niviuk.free.fr/umts_band.php for listings of bands. | ||||
| BLER | Block Error Rate (my phone displays nothing here) | ||||
| Cell ID | http://en.wikipedia.org/wiki/Cell_ID Gather MCC, MNC, LAC and go http://opencellid.org/ to see where you are at |
||||
| RRC State | See UMTS RCC States (my phone displays nothing here) | ||||
| Downlink Frequency | (my phone displays nothing here) | ||||
| Scrambling Code | Your "identifier" in the cell. See UMTS Quick Reference - Scrambling Code for more info | ||||
| Uplink Frequency | (my phone displays nothing here) | ||||
| Ciphering | (my phone displays nothing here) | ||||
| Transmit Power | (my phone displays nothing here) | ||||
| MM Info | [UMTS only] | ||||
| Serving PLMN | Public land mobile network information | ||||
| Location Area Code | LAC (decimal): http://en.wikipedia.org/wiki/Location_area_identity | ||||
| Routing Area Code | ? | ||||
| PLMN Sel Mod | |||||
| Mobile Network Code | MNC (decimal): http://en.wikipedia.org/wiki/Mobile_country_code | ||||
| Mobile Country Code | MCC (decimal): http://en.wikipedia.org/wiki/Mobile_country_code | ||||
| Service Type | ? | ||||
| Process PS | |||||
| MM Sub State | |||||
| MM State | |||||
| MM Service State | |||||
| Attach Reject Cause | |||||
| Process CS | |||||
| MM Sub State | |||||
| MM State | |||||
| MM Service State | |||||
| LU Reject Cause | |||||
| Equivalent PLMN List | |||||
| Process CO | |||||
| MM State | |||||
| MM Service State | |||||
| Neighbor Measurements | [LTE only] | ||||
| E-ARFCN | |||||
| Version | |||||
| Neighbor Cells List | (List) | ||||
(sub level 2) |
Measured RSSI | ||||
| Ant 0 Sample Offset | |||||
| Physical Cell ID | |||||
| Ant 0 Frame Offset | |||||
| Average RSRP | |||||
| Average RSRQ | |||||
| Ant 1 Frame Offset | |||||
| Srxlev | |||||
| Ant 1 Sample Offset | |||||
| Measured RSRP | |||||
| Frequenct Offset | Typo? Frequency Offset | ||||
| Measured RSRQ | |||||
| Qrxlevmin | |||||
| Connected mode LTE Intra-frequency Measurement | [LTE only] | ||||
| Detected Cells | (List) | ||||
| Measured Neighbor Cells | (List) | ||||
| Serving Filtered RSRQ | |||||
| Serving Physical Cell ID | |||||
| Subframe Number | |||||
| Serving Filtered RSRP | |||||
| E-ARFCN | |||||
| Serving Cell Info | [LTE only] | ||||
| Download Bandwidth | |||||
| Freq Band Indicator |
The frequency band you're at. See UARFCN for exact frequency. See http://niviuk.free.fr/umts_band.php for listings of bands and frequencies. Short list:
|
||||
| Download Frequency | |||||
| Num Tx Antennas | |||||
| UARFCN | UTRA Absolute Radio Frequency Channel Number: The channel number you're currently at. Decimal number, see http://niviuk.free.fr/umts_band.php for listings of bands and frequencies. | ||||
| Tracking Area Code | TAC | ||||
| Cell Identity | LCID of the serving cell | ||||
| Physical Cell ID | http://en.wikipedia.org/wiki/Cell_ID MCC, MNC and TAC is the exact location where the serving cell is located. |
||||
| Upload Frequency | |||||
| Upload Bandwidth | |||||
| Reselection Candidates | [LTE only] | ||||
| Version | |||||
| Serving Cell ID | |||||
| Serving EARFCN | |||||
| Reselection Candidates List | (List) | ||||
| Serving Cell Measurements | [LTE only] | ||||
| Measured RSSI | |||||
| Qrxlevmin | |||||
| P_Max | |||||
| Max UE Tx Power | |||||
| Version | |||||
| S Non Intra Search | |||||
| Physical Cell ID | |||||
| Average RSRP | |||||
| Measurement Rules | |||||
| Average RSRQ | |||||
| Serving Layer Priority | |||||
| Srxlev | |||||
| Measured RSRP | |||||
| Num of Consecutive DRX Cycles of S < 0 | |||||
| Measurement Rules Updated | |||||
| Measured RSRQ | |||||
| E-ARFCN | |||||
| S Intra Search | |||||
Please help me complete this (at least all the good stuff). If you find something incorrect or missing, please drop me a comment.
Goodbye Maxthon
Thursday, February 19. 2015
I have a policy of running a lot of different browsers on my computers. The idea is to gain experience of what works and what won't. When doing web development, any run-of-the-mill developer gets a tunnel vision and starts spewing out the classic "it works for me!" -style answers, when there are issues with a site.
So, I'm fighting hard to defeat that by using a lot of different browsers. One of my tools has been Maxthon browser. It isn't anymore. Goodbye Maxthon!
I was reading an article about "Lenovo PCs ship with man-in-the-middle adware that breaks HTTPS connections" and went to https://filippo.io/Badfish/ to check my browser. Amazingly it showed YES:

Whaat!
If I download the https://badfish.filippo.io/yes.png directly, then there is a proper notification about the problem:
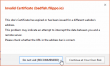
... but seeing the picture embedded nicely in a website means, that the browser won't bother checking while rendering a page. Anybody can display anything on a web page and I won't get any information about the dropped security. Not good. ![]()
There is no other way, than to uninstall. I absolutely won't recommend using anything that insecure!
Exporting a website certificate
Tuesday, February 10. 2015
This one was a tough one for me. Not technically, but mentally. I wrote about Java 1.7 update 51 breaking Cisco ASDM and how to fix it. Two separate users had the same problem, they didn't know how to get their hands on the Cisco certificate which is required.
My dilemma here is:
So, you're in charge of heavy machinery called a firewall, but you don't know how to get a certificate out of a website, huh!
This s a basic task for any security-minded admin, it's obvious that the skills required and skills available are pretty far from each other. Should I give instructions for this basic task, only to postpone the inevitable?
I guess I should.
Method 1: GnuTLS (the best option)
If you happen to have GnuTLS installed, it has an excellent command-line utility. This is mostly in Linux, but I have one running on Windows via Cygwin. Not all Linux distros have this one installed by default. It is easily available on all distros, though.
Example run (information has been omitted for brevity):
# gnutls-cli --print-cert blog.hqcodeshop.fi
Resolving 'blog.hqcodeshop.fi'...
Connecting to '81.22.252.148:443'...
- Certificate type: X.509
- Got a certificate list of 2 certificates.
- Certificate[0] info:
- subject ..., SHA-1 fingerprint `c87f57f182cd10be0d16b52c5a41c4a915593e6b'
Public Key Id:
c6a1e7cd6139f2ec8872e0a198b2a15a26fe1461
Public key's random art:
+--[ RSA 2048]----+
| |
| |
| E . |
| . . o . . |
| . . S = |
| + + B o |
|ooo+ o . = |
|*=o o .. o |
|*o.. o. . . |
+-----------------+
-----BEGIN CERTIFICATE-----
MIIEqzCCA5OgAwIBAgIDAih/MA0GCSqGSIb3DQEBCwUAMEcxCzAJBgNVBAYTAlVT
...
nklApvqYviZIwv20nMLwHjtf71ycGZumzNNWQrECBgNWYhFuNyaNe3nzO5fym6o=
-----END CERTIFICATE-----
- Certificate[1] info:
- subject ..., SHA-1 fingerprint `0e34141846e7423d37f20dc0ab06c9bbd843dc24'
-----BEGIN CERTIFICATE-----
MIIEJTCCAw2gAwIBAgIDAjp3MA0GCSqGSIb3DQEBCwUAMEIxCzAJBgNVBAYTAlVT
...
ZI3NjGFVkP46yl0lD/gdo0p0Vk8aVUBwdSWmMy66S6VdU5oNMOGNX2Esr8zvsJmh
gP8L8mJMcCaY
-----END CERTIFICATE-----
- Status: The certificate is trusted.
- Description: (TLS1.2-PKIX)-(ECDHE-RSA-SECP256R1)-(AES-128-CBC)-(SHA256)
- Ephemeral EC Diffie-Hellman parameters
- Using curve: SECP256R1
- Curve size: 256 bits
- Version: TLS1.2
- Key Exchange: ECDHE-RSA
- Server Signature: RSA-SHA1
- Cipher: AES-128-CBC
- MAC: SHA256
- Compression: NULL
- Handshake was completed
- Simple Client Mode:
Just hit ctrl-d or ctrl-c when the Simple Client Mode -prompt appears. You could actually talk HTTP to the server with that, but for getting the certificate it is not needed. The cert is already out there, just copy it and save it in a file. The 2nd cert is only intermediate CA certificate and it can be downloaded from web.
If you want to see the omitted information, just run the command. A public certificate is as public as anything in the net, there is no point in trying to hide it.
Method 2: OpenSSL (the popular option)
This method will work on any Linux or Mac OS X. There are couple of OpenSSL implementations for Windows, so most boxes should be able to run this one.
Why this isn't the best option is, because OpenSSL client doesn't do proper SNI. In the example below, it returns the wrong certificate. Not the one requested. If your site isn't sharing an IP-address, this will work for you.
Example:
# openssl s_client -connect blog.hqcodeshop.fi:443
CONNECTED(00000003)
depth=2 C = US, O = GeoTrust Inc., CN = GeoTrust Global CA
verify return:1
depth=1 C = US, O = GeoTrust Inc., CN = RapidSSL SHA256 CA - G3
verify return:1
depth=0 OU = GT61328546, ..., CN = *.hqsting.net
verify return:1
---
Certificate chain
0 s:/OU=GT61328546/.../CN=*.hqsting.net
i:/C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA - G3
1 s:/C=US/O=GeoTrust, Inc./CN=RapidSSL CA
i:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIErjCCA5agAwIBAgIDAit7MA0GCSqGSIb3DQEBCwUAMEcxCzAJBgNVBAYTAlVT
...
TP3W1usGKSJ+fipYhc9ZTUFVs+g3FZ+m3Sltyfb/motM06EP6eq5heDxxPquEhaq
OsY=
-----END CERTIFICATE-----
subject=/OU=GT61328546/.../CN=*.hqsting.net
issuer=/C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA - G3
---
No client certificate CA names sent
Server Temp Key: ECDH, prime256v1, 256 bits
---
SSL handshake has read 2921 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES128-SHA256
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-SHA256
Session-ID-ctx:
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 300 (seconds)
...
Start Time: 1423326309
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
DONE
Just hit ctrl-d or ctrl-c at the prompt. Again, you're at the HTTP-mode now and could talk to the web-server. The certificate is waiting on the screen to be copied and saved to a file.
Method 3: Firefox (the easy option)
Exporting a certificate of a website is implemented in Firefox browser.
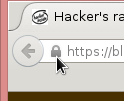
Click the lock-symbol:
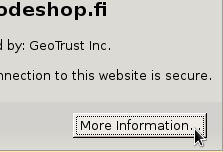
 A small dialog will open. Select More information:
A small dialog will open. Select More information:
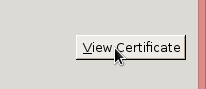
A big dialog with lot of information about the site will open up. One of the options is to View Certificate. Select it:
Step 4:
Select the bottom sertificate and export it. It will open a save as -dialog:
That's it! Now you have the certificate saved.
Blog upgrade to S9y 2.00 and HTTPS
Monday, February 9. 2015
Last weekend I went for Serendipity software version 2. This caused lot of downtime as the upgrade didn't go smoothly. I also made the entire server almost choke to a crash as my .htaccess / mod_rewrite -trickery caused looping. My Apache tried to loop itself into an exhaustion.
After I got everything back into shape, I got new toys. Especially the back office -side is vastly improved. On the public-side it seems pretty much the same.
While working on the blog I chose to go HTTPS. That seems to be the industry trend, see HTTPS as a ranking signal. While at it I verified my SHA-256 -signed certificate with Qualsys SSL Labs analysis tool. A certificate signed with less bits is considered as "insecure" nowadays as Google Chrome chooses to dislike your SHA-1 or MD5 -signed certs.

