Skype protocol hacked, part 3
Saturday, November 19. 2016
This one won't fade away, so I'm taking a third swing at the subject. Previous posts are here and here. I've been actively following the conversation in Sype community's Security, Privacy, Trust and Safety board's discussion thread "Link to "baidu" website sent to all of my contacts".
Recap, what happened so far
Tons of fake links are being sent to people via Skype as chat messages. The chat is originating from somebody you already know and who is in your Skype's contact list.
Microsoft has stated "Some Skype customers have reported their accounts being used to send spam" when asked about it. That is true, people have been their Skype-accounts hacked by automated attacks based on leaked passwords and those accounts have been used to send crap to their contacts. However, this beef isn't about that. This beef is about the fact, that people whose Skype-accounts HAVE NOT been hacked, are sending crap to their contacts.
Microsoft went the classic way: "change your password". People did that. The same people are STILL sending crap to their contacts. For that, there is no official statement besides to (this is so ridiculous, I have to quote this verbatum) "Delete UNKNOWN Entry from HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run and Delete all UNKNOWN files under %appdata%\Roaming". Link to the exact instructions is here. So, I consider myself to be well educated about finer details what's inside Windows registry or Windows user profile. Because there are thousands of entries there, I don't know all of them, it is impossible to tell which of them are unknown and which are not. How would somebody with almost no experience be able to do that! ![]() Actually the magnitude of Microsoft support blunder is so huge, they wiped off the chat log from the discussion board and Box.com.
Actually the magnitude of Microsoft support blunder is so huge, they wiped off the chat log from the discussion board and Box.com.
What people have also established, that there are two ways to login to a Skype session on any Skype-client. There is the old fashioned Skype-way and Microsoft Account. You can set a two-factor authentication into Microsoft Account, but not for Skype. Now that there are two ways to login, also please, remember that Skype can be run on multitude of mobile devices, Windows, Mac or directly from https://web.skype.com/. So, huge amount of attack surface exists there. What people have also established, that un-installing Skype from your device-of-choice doesn't make the problem go away, you'll still keep sending links to your contacts. So, reducing your personal attack-surface doesn't do it for you.
Obviously lots of people are royally pissed about this. Also Microsoft playing down their damage and offering completely useless support doesn't help.
The client devices are not compromized
When this kind of weird occurrence happens, any layman will immediately freak out and their mind there is with 100% certainity a single thought: my computer/phone has a virus!
In this case, no it does not.
People are "sending" these fake links after they un-installed Skype (two years ago). What exists, is the Skype-account. This is the hard part, which not-so-much-software-engineers don't grasp: your stuff in The Cloud can be cracked too, it doesn't have to be via your personal device. I don't know how to make this absolutely clear to a regular person.
The thing is: this issue is bothering many many people, and has been doing that since August 2016. All security flaw scenarios are possible, even cracked computers and mobile phones. However, that's not what interests me. My focus is on people whose computers have NOT been cracked, but are sending junk via Skype.
What's still happening
So, what's happened recenty is, that people are still receiving the links. Apparently (I haven't got any yet), the link has been changed from Baidu.com-based redirection to Vk.com, a Russian equivalent of Facebook. As I haven't received any of those, I cannot confirm the new link.
There are people, who have confirmed, that their Microsoft-account has been logged into from really weird geographic location. But that one can be easily fixed, change password and enable two factor auth they won't be doing that again. How the hack is actually done, we don't know. There was a theory about advertisement API, but personally I don't see that as a viable option. It would mean, that people actually would be using their Skype clients, but there are tons of people who haven't done that for couple years and are still spewing crap around.
Do something about it: Check that your account isn't cracked
There is no login-history, device list or anything that would resemble modern tools to audit your own account in the traditional Skype. This is what you can see:
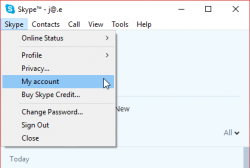
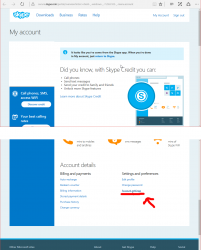
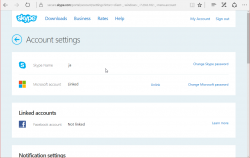
What I'd like to see is what newly created Skype-accounts have and make the original Skype-account be gone. As in merge/delete/drop. I don't need two separate logins for my Skype. Especially as there is no 2-FA, or login device history for it.
This is what you can do is make sure your Microsoft Account is secure. Login to https://account.microsoft.com/.
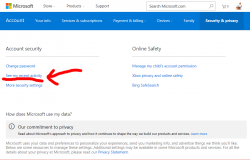
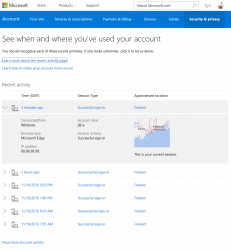
So, nothing wrong with my account. Here is an account having more-than-dubious history entry in it:
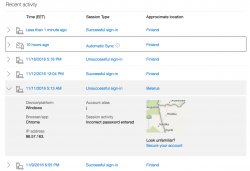
I've redacted the IP-address from Belarus. It's most likely some poor bastard's machine, which is cracked and used as a springboard forward.
What I'd like to see happen
Firstly Microsoft, the owners of Skype need to step forward and confirm that accounts with proper passwords are being used to send crap. They need to admit, that their systems are not recognizing any accepted password logins, but chat messages are still being sent by innocent people.
Secondly, they need to fix the issue. Whichever is broken there they need to address it. The worst case scenario is, that somebody can actually inject new chat messages out of thin air, without the sender being logged in.
Third, the old skype account login needs to be secured. That's the easiest one here to achieve. As newly created Skype-accounts are only via Microsoft Account, that shouldn't be much problem. Also I'd like to get rid of that login method. Update: Instructions for doing this are in my next post.
So, Microsoft, we're waiting for you.

