Passwords - Part 3 of 2 - Follow up
Thursday, June 17. 2021
This is part three of my two-part post. My thoughts on passwords in general are here and about leaked passworeds here.
I'm writing this to follow-up on multiple issues covered in previous parts. Some of this information was available at the time of writing but I just had not found it in time, some info was published afterwards but was closely related.
Troy Hunt's thoughts on RockYou2021
His tweet https://twitter.com/troyhunt/status/1402358364445679621 says:
Unlike the original 2009 RockYou data breach and consequent word list, these are not “pwned passwords”; it’s not a list of real world passwords compromised in data breaches, it’s just a list of words and the vast majority have never been passwords
Mr. Hunt is the leading expert on leaked passwords, so I'm inclined to take his word about it. Especially when he points the RockYou2021 "leak" to contain CrackStation's Password Cracking Dictionary. Emphasis: dictionary. The word-list will contain lists of words (1,493,677,782 words, 15GB) in all known languages available. That list has been public for couple of years.
IBM Security survey
Press release Pandemic-Induced Digital Reliance Creates Lingering Security Side Effects. Full report PDF.
In number of visualizations contained in the report, there is this one about password re-use:
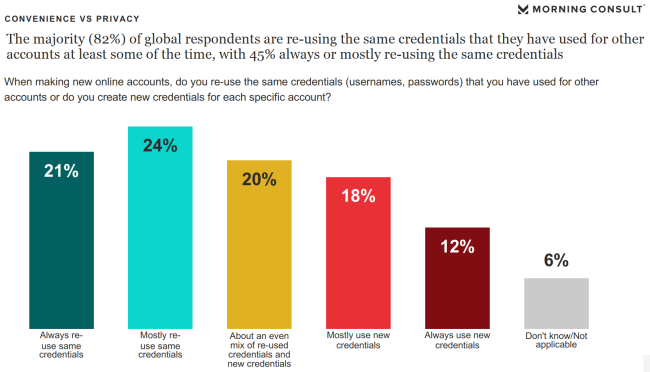
65% of participants are using same passwords always, mostly or often. That's seriously bad! ![]()
However, this is nothing new. It is in-line with other surveys, research and available data.
STOP re-using your passwords. NOW!
If you aren't, educate others about the dangers. Help them set up password managers.
Microsoft
ZDnet article Microsoft's CISO: Why we're trying to banish passwords forever descibes how Microsoft will handle passwords.
1: Employees at Microsoft don't have to change their passwords every 71 days.
Quote from Microsoft and NIST Say Password Expiration Policies Are No Longer Necessary :
Microsoft claims that password expiration requirements do more harm than good because they make users select predictable passwords, composed of sequential words and numbers, which are closely related to each other. Additionally, Microsoft claims that password expiration requirements limit containment because cybercriminals almost always use credentials as soon as they compromise them.
Nothing new there, except huge corporation actually doing it. This policy is described in NIST 800-63B section 5.1.1.2 Memorized Secret Verifiers, which states following:
Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically).
However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.
Also, multiple sources back that up. Example: Security Boulevard article The High Cost of Password Expiration Policies
2: "Nobody likes passwords"
A direct quote from Microsoft CISO Bret Arsenault:
Because nobody likes passwords.
You hate them, users hate them, IT departments hate them.
The only people who like passwords are criminals – they love them
I could not agree more.
3: End goal "we want to eliminate passwords"
Even I wrote, this can not be done in near future. But let's begin the transition! I'm all for it.
The idea is to use alternate means of authentication. What Microsoft is using is primarily biometrics. That's the same thing you'd be doing with your phone, but do the same with your computer.
Doing passwords correctly
When talking about computers, security, information security, passwords and so on, it is very easy to paint a gloom future and emphasize all the bad things. Let's end this with a positive note.
Auth0 blog post NIST Password Guidelines and Best Practices for 2020 has the guidelines simplified:
-
Length > Complexity: Seconding what I already wrote, make your passwords long, not necessarily complex. If you can, do both! If you have to choose, longer is better.
-
Eliminate Periodic Resets: This has already been covered, see above. Unfortunately end-users can not do anything about this, besides contact their admins and educate them.
-
Enable “Show Password While Typing”: Lot of sites have the eye-icon to display your password, it reduces typos and makes you confident to use long passwords. Again, nothing for end-user to do. The person designing and writing the software needs to handle this, but you as an end-user can voice your opinion and demand to have this feature.
-
Allow Password “Paste-In”: This is a definite must for me, my passwords are very long, I don't want to type them! Yet another, end users can not help this one, sorry.
-
Use Breached Password Protection: Passwords don't need to be complex, but they must be unique. Unique as not in the RockYou2021 8.4 billion words list. This is something you can do yourself. Use an unique password.
-
Don’t Use “Password Hints”: Huh! These are useless. If forced to use password hint, I never enter anything sane. My typical "hint" is something in fashion "the same as always".
-
Limit Password Attempts: Disable brute-force attempts. Unfortunately end-users can not do anything about this. If the system you're using has unlimited non-delayed login attempts, feel free to contact admins and educate them.
-
Use Multi-Factor Authentication: If option to use MFA is available, jump to it! Don't wait.
-
Secure Your Databases: During design and implementation every system needs to be properly hardened and locked-down. End users have very little options on determining if this is done properly or not. Sorry.
-
Hash Users’ Passwords: This is nearly the same as #9. The difference is, this is about your password, it needs to be stored in a way nobody, including the administators, have access to it.
Finally
All the evidence indicates we're finally transitioning away from passwords.
Be careful out there!

