Exporting a website certificate
Tuesday, February 10. 2015
This one was a tough one for me. Not technically, but mentally. I wrote about Java 1.7 update 51 breaking Cisco ASDM and how to fix it. Two separate users had the same problem, they didn't know how to get their hands on the Cisco certificate which is required.
My dilemma here is:
So, you're in charge of heavy machinery called a firewall, but you don't know how to get a certificate out of a website, huh!
This s a basic task for any security-minded admin, it's obvious that the skills required and skills available are pretty far from each other. Should I give instructions for this basic task, only to postpone the inevitable?
I guess I should.
Method 1: GnuTLS (the best option)
If you happen to have GnuTLS installed, it has an excellent command-line utility. This is mostly in Linux, but I have one running on Windows via Cygwin. Not all Linux distros have this one installed by default. It is easily available on all distros, though.
Example run (information has been omitted for brevity):
# gnutls-cli --print-cert blog.hqcodeshop.fi
Resolving 'blog.hqcodeshop.fi'...
Connecting to '81.22.252.148:443'...
- Certificate type: X.509
- Got a certificate list of 2 certificates.
- Certificate[0] info:
- subject ..., SHA-1 fingerprint `c87f57f182cd10be0d16b52c5a41c4a915593e6b'
Public Key Id:
c6a1e7cd6139f2ec8872e0a198b2a15a26fe1461
Public key's random art:
+--[ RSA 2048]----+
| |
| |
| E . |
| . . o . . |
| . . S = |
| + + B o |
|ooo+ o . = |
|*=o o .. o |
|*o.. o. . . |
+-----------------+
-----BEGIN CERTIFICATE-----
MIIEqzCCA5OgAwIBAgIDAih/MA0GCSqGSIb3DQEBCwUAMEcxCzAJBgNVBAYTAlVT
...
nklApvqYviZIwv20nMLwHjtf71ycGZumzNNWQrECBgNWYhFuNyaNe3nzO5fym6o=
-----END CERTIFICATE-----
- Certificate[1] info:
- subject ..., SHA-1 fingerprint `0e34141846e7423d37f20dc0ab06c9bbd843dc24'
-----BEGIN CERTIFICATE-----
MIIEJTCCAw2gAwIBAgIDAjp3MA0GCSqGSIb3DQEBCwUAMEIxCzAJBgNVBAYTAlVT
...
ZI3NjGFVkP46yl0lD/gdo0p0Vk8aVUBwdSWmMy66S6VdU5oNMOGNX2Esr8zvsJmh
gP8L8mJMcCaY
-----END CERTIFICATE-----
- Status: The certificate is trusted.
- Description: (TLS1.2-PKIX)-(ECDHE-RSA-SECP256R1)-(AES-128-CBC)-(SHA256)
- Ephemeral EC Diffie-Hellman parameters
- Using curve: SECP256R1
- Curve size: 256 bits
- Version: TLS1.2
- Key Exchange: ECDHE-RSA
- Server Signature: RSA-SHA1
- Cipher: AES-128-CBC
- MAC: SHA256
- Compression: NULL
- Handshake was completed
- Simple Client Mode:
Just hit ctrl-d or ctrl-c when the Simple Client Mode -prompt appears. You could actually talk HTTP to the server with that, but for getting the certificate it is not needed. The cert is already out there, just copy it and save it in a file. The 2nd cert is only intermediate CA certificate and it can be downloaded from web.
If you want to see the omitted information, just run the command. A public certificate is as public as anything in the net, there is no point in trying to hide it.
Method 2: OpenSSL (the popular option)
This method will work on any Linux or Mac OS X. There are couple of OpenSSL implementations for Windows, so most boxes should be able to run this one.
Why this isn't the best option is, because OpenSSL client doesn't do proper SNI. In the example below, it returns the wrong certificate. Not the one requested. If your site isn't sharing an IP-address, this will work for you.
Example:
# openssl s_client -connect blog.hqcodeshop.fi:443
CONNECTED(00000003)
depth=2 C = US, O = GeoTrust Inc., CN = GeoTrust Global CA
verify return:1
depth=1 C = US, O = GeoTrust Inc., CN = RapidSSL SHA256 CA - G3
verify return:1
depth=0 OU = GT61328546, ..., CN = *.hqsting.net
verify return:1
---
Certificate chain
0 s:/OU=GT61328546/.../CN=*.hqsting.net
i:/C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA - G3
1 s:/C=US/O=GeoTrust, Inc./CN=RapidSSL CA
i:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIErjCCA5agAwIBAgIDAit7MA0GCSqGSIb3DQEBCwUAMEcxCzAJBgNVBAYTAlVT
...
TP3W1usGKSJ+fipYhc9ZTUFVs+g3FZ+m3Sltyfb/motM06EP6eq5heDxxPquEhaq
OsY=
-----END CERTIFICATE-----
subject=/OU=GT61328546/.../CN=*.hqsting.net
issuer=/C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA - G3
---
No client certificate CA names sent
Server Temp Key: ECDH, prime256v1, 256 bits
---
SSL handshake has read 2921 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES128-SHA256
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-SHA256
Session-ID-ctx:
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 300 (seconds)
...
Start Time: 1423326309
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
DONE
Just hit ctrl-d or ctrl-c at the prompt. Again, you're at the HTTP-mode now and could talk to the web-server. The certificate is waiting on the screen to be copied and saved to a file.
Method 3: Firefox (the easy option)
Exporting a certificate of a website is implemented in Firefox browser.
Click the lock-symbol:
 A small dialog will open. Select More information:
A small dialog will open. Select More information:
A big dialog with lot of information about the site will open up. One of the options is to View Certificate. Select it:
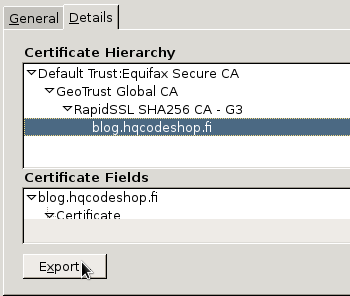
Step 4:
Select the bottom sertificate and export it. It will open a save as -dialog:
That's it! Now you have the certificate saved.

