Replacing MacBook Air SSD
Saturday, February 10. 2018
I've never disassembled an Apple laptop. A while back I got a chance to peek into one, as I was summoned to add more SSD-capacity into an Air. As you can see from the spec, it is a rather early model of Air. But hey, Apple hardware is quite robust and the value you get for your money is huge. So, after 7 years of usage, it is still worth replacing the SSD with a bigger one.
The instructions for this can be found from EveryMac.com, but I'll describe my experiences here. Also having video instructions only is not something I'd like to see. A high quality picture has its value too.
Prepare job
- Make sure there is a restorable Time Machine backup of the laptop.
- If you don't care for the data on the machine, this is not necessary.
- Make sure you can boot the device from an USB-stick:
- You can restore entire SSD content from Time Machine.
- You can do a fresh install to the new SSD
Part job
A new SSD is needed. Given the availability and low price, a Transcend 240GB JetDrive 500 SATAIII 6Gb/s Solid State Drive Upgrade Kit for Select MacBook Air Models (TS240GJDM500) was selected.
Getting one from Amazon.de was a painless and fast operation. Initially, I was wondering why would be selling an "external" replacement part, because the SSD I wanted to replace is surely inside the Mac. It surely has to do something with making an Apple spare part available. Normally parts are not available for general public.
To pop open an MacBook Air, you will need a pentalobe TS4 screwdriver, and to disconnect the SSD from the motherboard, a Torx T5 screwdriver is needed. Both of which are known to hardware hackers, but not commonly owned by general public. Luckily somebody knows this, and in the box with the new SSD both are there:
Replacement job
Popping the hood of a mac is almost a no-operation. There are 10 pentalobes there, remove them and the lid will open easily. After all the years of usage, there was some dust in the CPU-fan, so I carefully removed all that before proceeding.
When the guts are seen, first task is to remove the battery connector. This ensures, that the motherboard and SSD are shut down during the operation. The connector can be disconnected quite easily without any tools:
Target-of-the-day, SSD, can be located right next to CPU:
The arrow points to the Torx T5. That is the only screw holding the SSD in place. Since I had a cool aluminium external case for the SSD, of course I placed the old SSD there:
The new Transcent SSD looks like this. Exactly what the original Samsung:
After that it's just to flip the lid back on and tighten 10 pentalobes.
Entire hardware job was completed in 15 minutes. That part was designed to be replaced!
macOS job
Now we have a laptop with a completely blank SSD in it. Of course I had to test it, but it really doesn't do much on boot. The only real option was to insert an USB-stick and press the Option-key to get the boot menu, select the USB-stick and then get to the Install/Upgrade -menu. Select Disk Utility from that:
As expected, the new drive is unitialized and you cannot select a device with that status as macOS install destination.
Since Apple engineers are quite smart, to convert an uninitialized drive to an intialized one, the operation needed is to erase it. WHAT! Yes. To repeat, the operation is to erase the drive. ![]() The drive is completely empty, it does not have a partition table, file system or data in it, but in their infinite wisdom Apple engineers have decided, the only way I can initialize the new SSD is by making double-sure there is nothing on it.
The drive is completely empty, it does not have a partition table, file system or data in it, but in their infinite wisdom Apple engineers have decided, the only way I can initialize the new SSD is by making double-sure there is nothing on it.
The erase will take a lot of time. Most if it, the installer tries to do something erase-related to it, but keeps failing miserably mainly due to lack of partition table. After the erase completes, there is a file system and regular macOS install can proceed. I chose to restore the machine from a TM-backup:
That really took couple hours and I didn't want to eyeball that through.
Job well done!
First boot from newly installed SSD, from restored machine image was success. First login indicated no changes at all. It was just like this machine was running as-is.
Ultimately a great success (like Borat would say)!
Arch Linux failing to update man-db
Friday, January 26. 2018
This week seems to be especially hard on my Linuxes. Doing a regular pacman -Syu started spitting crap on me:
error: failed to commit transaction (conflicting files)
man-db: /usr/bin/accessdb exists in filesystem
man-db: /usr/bin/apropos exists in filesystem
man-db: /usr/bin/catman exists in filesystem
man-db: /usr/bin/convert-mans exists in filesystem
man-db: /usr/bin/lexgrog exists in filesystem
man-db: /usr/bin/man exists in filesystem
man-db: /usr/bin/mandb exists in filesystem
man-db: /usr/bin/manpath exists in filesystem
man-db: /usr/bin/whatis exists in filesystem
man-db: /usr/lib/man-db/globbing exists in filesystem
man-db: /usr/lib/man-db/libman-2.7.6.1.so exists in filesystem
man-db: /usr/lib/man-db/libman.so exists in filesystem
man-db: /usr/lib/man-db/libmandb-2.7.6.1.so exists in filesystem
...
A simple query for what's wrong:
# pacman -Qkk man-db
man-db: 363 total files, 0 altered files
So, nothing wrong with it. It just loves busting my balls! ![]()
Using a bigger hammer:
# pacman -S --force man-db
...
:: Processing package changes...
(1/1) upgrading man-db [######################] 100%
New optional dependencies for man-db
gzip [installed]
:: Running post-transaction hooks...
(1/2) Creating temporary files...
(2/2) Arming ConditionNeedsUpdate...
Now my pacman -Syu works. Weird case, that.
Open Management Infrastructure in Azure gone wild
Thursday, January 25. 2018
I opened my mail, and I had 730 new e-mails there! Whaat!
One of my Azure boxes has (for reason unknown to me), following crontab-entry on root's crontab:
* * * * * [ \( ! -f /etc/opt/omi/creds/omi.keytab \) -o
\( /etc/krb5.keytab -nt /etc/opt/omi/creds/omi.keytab \) ] &&
/opt/omi/bin/support/ktstrip /etc/krb5.keytab /etc/opt/omi/creds/omi.keytab
/opt/omi/bin/support/ktstrip keeps failing, because /etc/krb5.keytab is missing. And that command is run every single minute on my machine. So, every single minute I get a new information about the failure. Nice! ![]()
The sequence of events is totally unclear to me. I haven't touched anything, but this morning an influx of e-mails stated pouring in.
OMI, or Open Management Infrastructure is something Linux-images in Azure have, so it shouldn't be anything dangerous.
The obvious fix as to remove that stupid line.
Monopoly
Sunday, January 21. 2018
Since most of the revenue earned by my empolyer comes from Candy Crush, a lot of swag around the office is somehow related. Very understandable, that.
This time we all got a Monopoly-game, but not the regular one everybody has been playing. Ok, to be entirely clear on this, threre are a minimum of 37 different language editions of the game, so in which country you spent your childhood, make it depend which streets the game you used to play has. Anyway, this is the Candy Crush -edition of Monopoly:

Also very understandably we did discuss different aspects of the game, one of them being about the winning tactics.
I started thinking, if it would be possible to just go to The Net and get some source code for a Monopoly-simulator and try to program some rules to a bot, which would then play against other bots and see which approach would be more likely to win in the long run.
Quite easily, I found a Python-version of the game by Juan Manuel Contreras from GitHub. Unfortunately, the work by him is quite unfinished, so I chose to fork it and continue from that point. I didn't touch the .py-files, only the Jupyter notebook -version of the game.
As a result of some weekend coding, I have:
- Class for user game logic
- Lots of game functionality, moving around, collecting rent, buying, selling, going bankrupt
- Winning the game
The resulting notebook is quite bug-free, but there are still some game rules, that aren't properly followed. Especially the situation where a player defaults, all the assets need to go to creditor. If creditor is another player, then to that, if bank, there needs to be an auction where other players may purchase the defaulting user's properties. Doing auctions between AI-players is not that easy, so none of that is implemented.
The same AI-module would be needed in a situation where a player lands on an unowned property. According to rules, that needs to be auctioned if the player doesn't want to buy it. Not so easy to do with Python.
Also, the Chance-cards are not implemented, so it is impossible to get a Get-out-of-jail -card. Yet.
By running the game in the sim for couple hundred times, I found that with 5 players, it is very likely to get into a situation where nobody can build houses/hotels. Also, if there are not many houses/hotels, the other players are unlikely to land on those properties and the game will run forever with all players accumulating wealth indefinitely. To get around that, I'm detecting such a situction and artificially doubling rents. That rule is not in the original Monopoly-rules. How human players would solve this situation is to trade/barter properties between each other to gain building rights. A thing not so easy to implement with any programming language.
That Python Monopoly -project was just a fun thing to do. I'm not sure if I'll continue it any further. The code is out there, if you're interested.
HOWTO: Configuring a router on a Mini-PC with CentOS
Thursday, January 18. 2018
Over half an year later, I realized, that I never published my article about operating system and software setup of my Mini-PC router. This is a follow-up post about the Qotom-hardware I wrote earlier. So, its probably about time to do that! ![]()
To get the ball rolling on new CentOS installation, a good start is to download it, Rufus it into an USB-stick and install the minimal setup into router-PC. The CentOS installation is so well documented and trivial process, I won't go into any details of it. Read something like Installing Red Hat Enterprise Linux 7.4 on all architectures for details of that.
Goal
Every project needs a goal. In any kind of engineering there is a specification and criteria, that the goal has been met.
The goal of this project is to create a Linux-server capable of securing a local network from the Internet and allow traffic to pass from the LAN to the wild-wild-net.
Spec:
- There is a working CentOS Linux running on the MiniPC
- ISP's cable modem is configured as bridge, no double NATting done
- MiniPC gets a public IP-address from ISP
- MiniPC can be accessed from the Net via the IP-address
- Configurations persist a reboot on the MiniPC
- MiniPC issues dynamic IP-addresses to LAN-clients
- MiniPC acts as a caching nameserver to LAN-clients
- Any requests from the Net are not served
- Wireless access point is configured not do do any routing, aka. it is in access point mode
- The setup is secure with attack surface minimized
- LAN IP-address range is 192.168.1.0/24
Definition of done:
- Internet works!
- MiniPC can connect to net
- MiniPC can be connected from net and LAN via SSH
- Wired clients can connect to net via Ethernet cable without any manual configuration
- Wireless clients can connec to the net via Wi-Fi without any manual configuration
Step 1: Packages
After minimal installation, the set of tools and packages required includes:
net-tools bind-utils screen tcpdump policycoreutils-python setools
- net-tools: mostly for netstat, using
routeorifconfigis deprecated - bind-utils: for dig and nslookup
- screen: for full-screen window manager
- tcpdump: taking a look into Ethernet and TCP/IP-packages, when something goes wrong, getting detailed view is very important
- policycoreutils-python setools: for managing SELinux
Step 2: Remove NetworkManager
Packages to install: -none needed-
Why a server would have GNOME NetworkManager installed on a server is beyond me. I simply cannot comprehend what CentOS-people are thinking, when they as default treat my server as a laptop. But the main thing is, that this piece of shit needs to go! The quicker, the better!
DANGER!
When you actually run the yum-command to remove NetworkManager, your system will lose all network connectivity. So, please, do run this at a console, not via SSH-connection.
DANGER!
Run command as root on console:
yum erase NetworkManager
Now your system's networking is royally messed up.
Step 3: Setup NICs
Packages to install: -none needed-
Check that NetworkManager created and left ifcfg-files into /etc/sysconfig/network-scripts/. If the appropriate ifcfg-files (one for each interface) are gone, you need to start learning how to write one fast. A good starting point on that would be RedHat Enterprise Linux 7 product documentation, Networking Guide, section 2.2 Editing Network Configuration Files.
LAN interface
Out of the two Ethernet-interfaces, 50/50 coin-flip ended as enp3s0 LAN and enp1s0 WAN. For any practical purposes, it really doesn't matter which one is which, but I'm describing here my setup. If you're using some other hardware, your interface names won't match those.
For any sensible use of your LAN-side, this interface should be connected to a network switch, so that your local network can be shared by your PC, Playstation, TV, Wi-Fi access point or whatever you have there running. Of course you can run it with only one host connected directly to the router.
This is critical: Your LAN-interface MUST have a static IP-address for it. It really cannot act as LAN-side of a router without one.
I chose my LAN to be private IP-range 192.168.1.0/24, so I edited /etc/sysconfig/network-scripts/ifcfg-enp3s0 to contain:
TYPE=Ethernet
BOOTPROTO=none
DEFROUTE=yes
IPV6INIT=yes
NAME=enp3s0
UUID=-don't-touch-this-
DEVICE=enp3s0
ONBOOT=yes
NETWORK=192.168.1.0
BROADCAST=193.168.1.255
USERCTL=no
IPADDR=192.168.1.1
PREFIX=24
IPV4_FAILURE_FATAL=no
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_PEERDNS=yes
IPV6_PEERROUTES=yes
IPV6_FAILURE_FATAL=no
WAN interface
For WAN, there is no need to touch enp1s0 setup (much). When your WAN-interface (enp1s0) starts, it will obtain an IP-address from your ISP. With that, it will also get your ISP's DNS-address an overwrite your precious manual changes in /etc/resolv.conf. You don't want that to happen. So, prevent that and edit /etc/sysconfig/network-scripts/ifcfg-enp1s0 and add:
PEERDNS="no"
Well, that was easy!
IP-forwarding
For routing to work, it requires Linux kernel to have IP-forwarding enabled. It will allow network packets to travel between interfaces.
Enable IP-forwarding immediately:
sysctl -w net.ipv4.ip_forward=1
Enable IP-forwarding on boot:
sysctl net.ipv4.ip_forward > /etc/sysctl.d/1_ip_forward.conf
Finalize network setup
When your network interface configurations are ok, restart everything by running following as root:
systemctl enable network
systemctl restart network
Now your system:
- has both interfaces on-line
- is reachable from a machine on your wired-LAN using a static IP-address other than 192.168.1.1.
Note: your router doesn'ht have DHCPd running yet, so you need to figure out how to configure a static IP-address to your device - still gets an IP-address from your ISP from your external interface
- can reach IP-addresses via both external and internal interfaces
If these criteria are not met, there is simply no point in proceeding. Your system won't work as a router without those prerequisites.
Finally, make sure that your IPtables-rules have effect. Your box is connected to Internet and it can be accessed/bombarded from there, so run following to secure your setup:
systemctl restart firewalld
Now your system is ready to become a router.
Step 4: Firewalld
Packages to install: -none needed-
Zones
Out-of-box CentOS has firewalld enabled. It has only one zone defined for public wild-wild-net, also TCP/22 SSH is open for the world. This needs to be run as root. First split off LAN into own zone home:
# firewall-cmd --zone home --change-interface enp3s0 --permanent
Check the zones and their assigned interfaces:
# firewall-cmd --get-active-zones
home
interfaces: enp3s0
public
interfaces: enp1s0
Setup network address translation (NAT) and allow traffic to flow from your LAN to outside world. Any relevant traffic is allowed to flow in from Internet back to your LAN. Commands to run:
# firewall-cmd --permanent --direct --add-rule ipv4 nat POSTROUTING 0 -o enp1s0 -j MASQUERADE
# firewall-cmd --permanent --direct --add-rule ipv4 filter FWDI_home_allow 0 -o enp1s0 -j ACCEPT
# firewall-cmd --permanent --direct --add-rule ipv4 filter FWDI_public_allow 0 -o enp3s0 -m state --state RELATED,ESTABLISHED -j ACCEPT
Enable the DNS-server we'll setup later, also disable any outgoing DNS-queries from your LAN (a security measure):
# firewall-cmd --permanent --zone home --add-service dns
# firewall-cmd --permanent --direct --add-rule ipv4 filter FWDI_home_deny 0 -p udp -m udp --dport 53 -j REJECT
At this point do a reload:
# firewall-cmd --reload
... and test your firewall setup from router:
- You still must be able to access Internet from your router
- Your LAN does work at this point. A client with a static IP must be able to access Internet.
Step 5: Named
Packages to install: bind-chroot
You can continue to use your ISP's nameserver, but I never do that. It makes much more sense to have a caching nameserver running at your own router. This allows your box to go directly to Internet root servers and do all the name queries for you. In many countries ISPs intentionally drop some domains out or are forced by government to do that. Running your own resolver makes sure that you get all the records as is and in case of changes you can flush caches whenever you want and don't have to wait for a record to expire.Out-of-box the BIND 9.9.4 does not server anybody else than localhost. To fix this, find following two lines in /etc/named.conf:
listen-on port 53 { 127.0.0.1; };
allow-query { localhost; };
Edit them to contain:
listen-on port 53 { 127.0.0.1; 192.168.1.1; };
allow-query { localhost; 192.168.1.0/24; };
Finally, change your system's default name resolver by editing /etc/resolv.conf to contain a single line:
nameserver 127.0.0.1
Start the server and enable it to start on boot:
systemctl start named-chroot
systemctl enable named-chroot
Now you're ready to test the setup. Just host www.google.com or your favorite site. Successful reply will include IP-address(es) for your query.
Step 6: DHCP
Packages to install: dhcp
Edit/etc/dhcp/dhcpd.conf and have it contain:
ddns-update-style interim;
ignore client-updates;
authoritative;
default-lease-time 14400;
max-lease-time 86400;
option subnet-mask 255.255.255.0;
option broadcast-address 192.168.1.255;
option routers 192.168.1.1;
option domain-name "my.own.lan";
option domain-name-servers 192.168.1.1;
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.50 192.168.1.99;
}
That piece of configuration will use your router as DNS for the clients and issue them addresses from range .50 - .99.
Start the server and enable it to start on boot:
systemctl start dhcpd
systemctl enable dhcpd
At this point, configure your client to use DHCP for IP-addressing. You must get an IP from the above range, also DNS-resolve and NAT should work, but that's the next step to do. Test it all.
Step 7: Testing it
Make sure:
- A client in your LAN gets an IP-address from DHCP
- A client in your LAN can ping your router at 192.168.1.1
- A client in your LAN can ping something in the Internet, like Google's name server at 8.8.8.8
- A client in your LAN resolves names, for example:
nslookup www.google.comreturns IP-addresses - A client in your LAN can access https://www.google.com/ via a web-browser
That's it! What else would you need?
Done!
Congratulations on your new router!
What I did next was set up my own DNS-zone so that my hosts had FQDNs. But that's beyond this blog post. Read something like How To Configure BIND as a Private Network DNS Server on CentOS 7 by DigitalOcean for that.
Com Hem offering IPv6 /56 prefix to its customers
Monday, January 15. 2018
UUUJEA! ![]()
Com Hem has been rolling out a native SLAAC/DHCPv6-based IPv6 to it's entire customer base, and they took a very important step 2 in their project. They started honoring Prefix Delegation -requests! To a non-network person that means absolutely nothing, but to a network administrator that is really a game changer!
Normally I don't use much of the features my Sagemcom cable-TV -router has, it's just set to bridge:
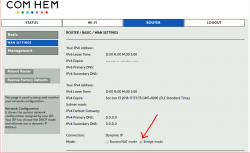
Since I failed earlier to get a prefix from my ISP, I was toying around with my router and set it to router-mode, and to my great surprise:
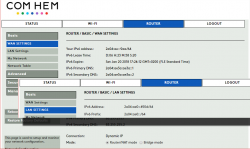
The thing issued my LAN a /64 IPv6-network! Nice.
After putting everything back and eye-balling the DHCPv6 lease file on my Linux-router:
lease6 {
interface "enp1s0";
ia-pd c4:d0:0a:85 {
starts 1515858667;
renew 302400;
rebind 483840;
iaprefix 2a04:ae00::/56 {
starts 1515858667;
preferred-life 604800;
max-life 2592000;
}
option dhcp6.status-code success;
}
}
Yes, it contains an ia-pd -section! The iaprefix from the file is mine, only mine, my precious address space! ![]()
I have no idea how long they have been honoring my PD-requests, but on December 17th they didn't.
A generally accepted IPv6-deployment principle is to follow RFC 5375 [IPv6 Unicast Address Assignment Considerations]'s suggestions and issue a minimum of /64 (18E IPv6 addresses) to customers. Since this /64 is completely useless for your own LAN, a second suggestion is to issue a /48 (1,2 million E IPv6 addresses) or /56 (4700E IPv6 addresses) prefix for consumer's own LANs.
Note: 18E is SI-prefix for exa, aka 10^18. A /64 IPv6 network has 18,446,744,073,709,551,616 unique addresses in it.
The numbers are astronomically big and it's quite easy to get confused and lose the perspective what they actually mean. A more concrete approach is, that by being issued a /56, I can now split my prefix into 256 separate /64 networks as I please. It's not like I need 256 LANs, I'm totally happy get even 1 of them to work! ![]()
Now I have my hands full to configure and test everything on my LAN. I need to make sure, that native-IPv6 works for wired and wireless toys I have here.
Intel CPU bug: Meltdown aftermath, Part 2
Sunday, January 14. 2018
When first information about a severe security flaw in Intel CPUs came out, it was immediately obvious, that this one is huge. This is in the scale of a meteorite hitting The Earth.
Here is just one example of what can happen, when fixed Linux kernels are deployed. I've been pumping data points from my weather station to Weather Underground for couple of years. Now this is how they are able to display my data:
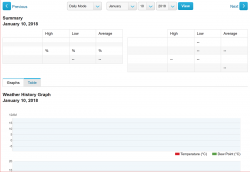
If you don't see any graphs or data points there, that's my point here! WU does not work! ![]()
Yesterday I got an e-mail from them explaining the problems they're facing:
The interruption of service was related to the hot patches applied to our servers to correct the recent Intel hardware security flaws. We can say with 100% confidence that the data you share with us is completely safe. The patches required systems to be rebooted and, as these systems came back online, many of them did not boot up cleanly.
That is most definitely not the entire truth. The quality of their service at the time of writing this blog post is simply crap! ![]() Looks like Meltdown mitigation hit them harder than they anticipated.
Looks like Meltdown mitigation hit them harder than they anticipated.
Intel CPU bug: Meltdown aftermath - Investing into popcorn for 2018
Monday, January 8. 2018
I came back from Christmas holidays on Tuesday 2nd January and quite soon that morning our corporate chat channels were buzzing about this "Intel CPU flaw". Lot of the information came from article The mysterious case of the Linux Page Table Isolation patches. At the end, the author of the post suggests "Invest in popcorn, 2018 is going to be fun". For something written on first day of the year 2018, that is pretty well said! ![]()
More and more details leaked on Wednesday 3rd. The Register article Kernel-memory-leaking Intel processor design flaw forces Linux, Windows redesign suggested said, that Linux kernel team named the flaw as Forcefully Unmap Complete Kernel With Interrupt Trampolines, aka FUCKWIT. So, they must have been mighty annoyed by this one. Urban Dictionary has a rather hilarious explanation of it.
Given the time difference between US an Europe, the information was published late on 3rd January, in form of website Meltdown and Spectre - Vulnerabilities in modern computers leak passwords and sensitive data. On Thursday 4th European time, entire Internet was full of news and speculation of these security flaws. Nobody has really confirmed this, but it looks like Intel knew about this flaw back in June 2017, for example Ubuntu-project confirms, that they received information about the flaw back in November 9th.
So, what is fuss this all about?
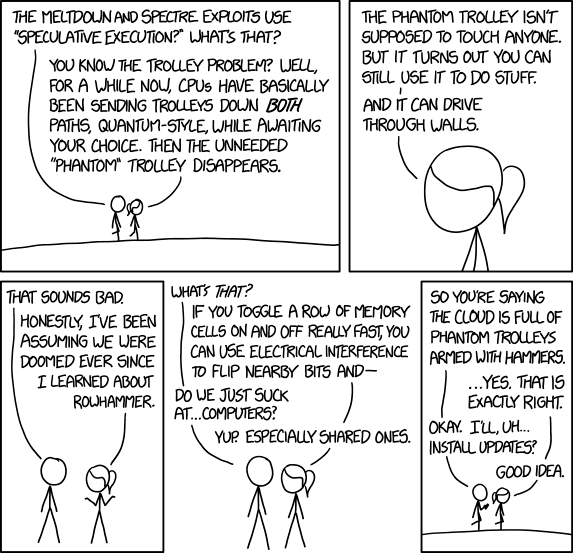
Since nobody really understands Kernel page-table isolation or Speculative execution, a much simper approach is needed to get a grasp of this problem (yes, you Super-Nerds understand it, I know!).
Xkcd #1938 has the best summary of this flaw that I've seen:
Mr. Daniel Miessler also has pretty good summary of the problem in his post A Simple Explanation of the Differences Between Meltdown and Spectre:
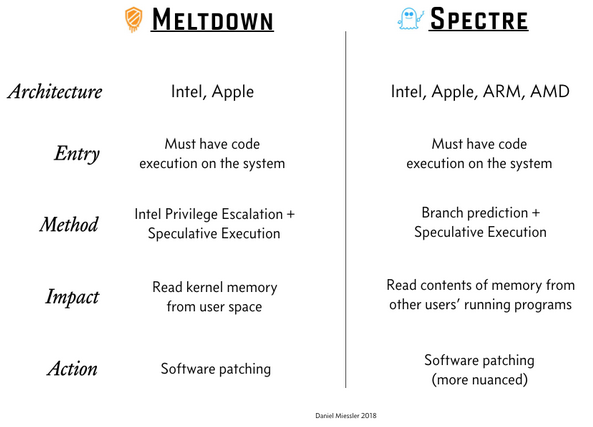
Ultimately you have two choices:
- Have a computer, which has a serious exploitable security flaw
- Lose some of your CPU-power
Most cases door #1 is chosen for you by your operating system vendor or cloud service provider.
A real measured effect of the fix
This is what Epic Games measured for their game Fortnite:
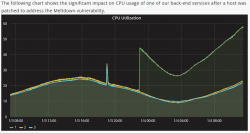
While looking at the graph, please remember, that Epic Games didn't choose to have the fix installed. This decision was made for them thanks to cloud computing.
There are number of similar reports all around the web, including Tim Gostony's tweet "Impact of the patch for the Intel bug on my AWS EC2 instances running Linux". It shows much les bump in the CPU-power than Epic Games' graph, but still it is there and it can be noticed.
What now?
Ok, everybody's every CPU is affected, but luckily for Meltdown mitigation you wouldn't normally run malware on your computer anyway. For Spectre, it gets scary. It mostly affects shared computers where somebody else is capable of stealing data from your instance.
The #1 thing I'll be waiting most is a physical CPU product that can be purhcased from a store which has a fix for this. Nobody has even promised anything about that. The existing software-based fixes are horrible. For example I was running Progress Quest on a Windows 93 session on a i7 laptop. After the fix, simply starting Windows 93 on a web browser it takes almost all of the CPU instead of idling like it did before the fix.
Amazon Web Services (AWS) in their original statement they said that "This is a vulnerability that has existed for more than 20 years in modern processor architectures like Intel, AMD, and ARM across servers, desktops, and mobile devices." I'm hoping, that it will take less than a decade to get it fixed.
QNAP Stopping Maintenance of TS-419P II
Tuesday, January 2. 2018
As usual, I got an e-mail from my NAS-box stating, that it has a new firmware upgrade QTS 4.3.3.0404 build 20171213.
It had the usual release notes telling the changes. What really caught my attention was:
QTS 4.3.3 is the final available firmware update for the following models: TS-419U II
WHAAT! Just out of the blue, my model was obsoleted piece of junk! ![]()
The actual full list of models is: TS-112P, TS-212P, TS-212-E, HS-210, TS-112, TS-212, TS-121, TS-221, TS-421 TS-120, TS-220, TS-420, TS-420U, TS-421U TS-412, TS-412U, TS-419U, TS-419U+, TS-419U II, TS-119P II, TS-219P II, TS-419P II, TS-119P+, TS-219P+, TS-419P+, TS-119P, TS-219P, TS-419P, TS-119, TS-219, TS-419
So, only the recent QNAP boxes were maintained from this point on. Darn! My take on their decision to stop maintaining all the old models is, that initially they barely maintained them at all. In fact, QNAP got burned seriously on not acting: 0-day: QNAP NAS Devices suffer of heap overflow. In less than two years they managed to get that one fixed. They received information on 1st Feb 2016, stalled on the fix and after 12 months somebody else stumbled into the same flaw and after QNAP failed to receive the information about it, he released into public. QNAP managed to the fix out at 14th Feb 2017.
To me that action (read: lack of it) means, that they did not have a protocol in place for a situation where a security flaw would be found in one of (read: all of) their main products sold to general public. While spewing out unfounded allegations here, I'm pretty confident, that it wouldn't have made any difference if the security flaw was in their internal systems. Also, I'm sure, they did not act on the initial report as the author was well-behaving and extended his grace period on QNAP's request. Unfortunately to QNAP, their security reporting system wasn't maintained and it didn't work at the time of second finding, so the information leaked quite soon.
After all this commotion, they chose to create processes, assign personnel to it and start maintaining their products, they suddenly realized, that IT'S HARD WORK! ![]() Oh really! Rest of the world knows it already. But that's what you need to do when you are in device manufacturing business. World is full of non-maintained IoT-junk, as this Twitter-feed points out.
Oh really! Rest of the world knows it already. But that's what you need to do when you are in device manufacturing business. World is full of non-maintained IoT-junk, as this Twitter-feed points out.
Ok, enough rant. Now I have a decision to make. What to do with a perfectly good NAS-box. Suggestions are welcome.
Mini Arcade Machine
Saturday, December 30. 2017
Looks like I've been nice, as Santa Claus brought me a nice present. A Mini Arcade Machine!


By the looks of it, it must be some sort of Android device placed into an arcade cabinet.
There are 240 games to play, but none of them are well-known titles. Obviously, they didn't want to pay any royalties for using the names. However, all the games are classic ones which I've played couple decades ago.
What I was expecting to see is a HDMI-output, but there is none. All the gaming needs to be done on a tiny screen.
Windows 10 Fall Creators Update breaking sleep
Monday, December 18. 2017
Problem
My gaming PC got the fall update quite late and after that it wouldn't stay in sleep. Something got broken in the update and I had to shut it down every single time I didn't want to use it. Annoying!
Debugging - The Reason
The reason it popped back on wasn't big of a mystery. There is a simple command to query the wake reason:
PS C:\WINDOWS\system32> .\powercfg.exe /waketimers
Timer set by [SERVICE] \Device\HarddiskVolume4\Windows\System32\svchost.exe (SystemEventsBroker) expires at 21:46:29 on 15.12.2017.
Reason: Windows will execute 'NT TASK\Microsoft\Windows\UpdateOrchestrator\Reboot' scheduled task that requested waking the computer.
There are number of articles about How to disable wake timers?, but it doesn't fix this.
A peek into Windows Task Scheduler reveals the ugly fact:
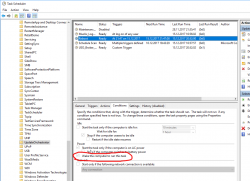
There is a hourly scheduled task, that indeed does run every hour and every goddamn hour it will wake my computer from the sleep to see if it needs to reboot it! Who having half a brain made that engineering decision at Microsoft?!
Attempt 1 - Disable the task - FAIL!
Ok, easy thing, let's disable the task. Or ... let's not. It is impossible! The permissions prevent regular human beings from doing that.
After a while, I bumped into somebody else having this same particular problem. Computer is waking up and: Can't modify task “Reboot” in win10 home. Basically, the idea is to go get Sysinternals PStools. It contains a tool called PSexec, which can do the modification for you.
Like this:
First run a cmd.exe with the PSexec 64-bit version:
PS D:\Users\Downloads> .\PsExec64.exe /s cmd.exe
Now, that permission-barrier is fixed, then:
C:\WINDOWS\system32>schtasks /change /tn "\Microsoft\Windows\UpdateOrchestrator\Reboot" /disable
SUCCESS: The parameters of scheduled task "\Microsoft\Windows\UpdateOrchestrator\Reboot" have been changed.
Now the stupid scheduled task is running hourly as expected, but NOT when your computer is sleeping. But ... guess what! Yes! There is something in Windows 10 internals, that keeps that particular task enabled. It will stay disabled for half an hour or so, but ultimately just using the computer makes the task enabled again, and the problem persists.
Attempt 2 - Remove the allow wake setting - FAIL!
By using the PsExec64.exe-trick, it is possible to get an XML-representation of the task, by running:
schtasks /tn "\Microsoft\Windows\UpdateOrchestrator\Reboot" /xml
in the XML-data there is:
<WakeToRun>true</WakeToRun>
... but I don't know how to change a task from XML-file. You can create a new one, but changing seems impossible.
So, ultimately I had to find something else
Attempt 3 - Powershell - FAIL!
Instead of spawning a new cmd.exe, going for PowerShell has benefits - it can actually edit an existing task. There is a built-in applet Get-ScheduledTask, with appropriate counterpart for setting the properties.
Spawn a nice PowerShell-session with appropriate permissions:
.\PsExec64.exe /s powershell.exe
The shell is kinda dead, for example output is garbled and input editing has issues, but if you know what to run, it will do it given the correct permissions.
As suggested in use powershell to find scheduled tasks set to wake the computer, now it is possible to get a list of Scheduled Tasks which have permission to wake the computer:
PS C:\WINDOWS\system32> Get-ScheduledTask | where {$_.settings.waketorun}
My computer will output a list like:
TaskPath TaskName
-------- --------
\Microsoft\Windows\.NET Framework\ .NET Framework NGEN v4.0.3031...
\Microsoft\Windows\.NET Framework\ .NET Framework NGEN v4.0.3031...
\Microsoft\Windows\SharedPC\ Account Cleanup
\Microsoft\Windows\UpdateOrchestrator\ Reboot
A simple(?) one-liner will edit the task (backtick is the word-wrap operator):
Get-ScheduledTask `
-TaskPath \Microsoft\Windows\UpdateOrchestrator\ `
-TaskName Reboot |
%{ $_.Settings.WakeToRun = $false ; `
Set-ScheduledTask -TaskName $_.TaskName -TaskPath $_.TaskPath -Settings $_.Settings }
Yes, now the task is enabled, but has the appropriate condition setting for allow wake the computer from sleep disabled.
... aaaand it doesn't work. The same thing altering the enabled-state also resets this setting. ![]() Darn!
Darn!
Attempt 4 - Revoke permissions - Success!
This was driving me mad!
It worked perfectly before the stupid update!
![]()
Finally, I found an article from Reddit: Is there ANY way to stop UpdateOrchestrator for turning 'wake the computer to run this task' back on after every cumulative update?
That guy suggested to revoke all permissions from the file. Now the automator which keeps resetting the settings fails to touch the file.
The command I ran in PowerShell is:
icacls $env:windir"\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Reboot" `
/inheritance:r `
/deny "Everyone:F" `
/deny "SYSTEM:F" `
/deny "Local Service:F" `
/deny "Administrators:F"
That simply puts everybody and everything into deny-list for the file-access. AND IT WORKS!
So, looks like ultimately whatever the mechanism is restoring the setting, somebody loves writing to the file, but it doesn't know how to reset the permissions. Which is nice! ![]()
I chose to keep the task enabled, but unset the allow wake -setting. So, when my computer is running, the task is ran every hour as expected, but when my computer is sleeping, my computer is sleeping and doesn't wake for nobody.
Microsoft:
Suggestion, eat your own dog food! If anybody at the Windows-team doing power management/task scheduler would run this at home they would know the annoyance instantly.
Com Hem offering IPv6 via DHCPv6 to its customers
Sunday, December 17. 2017
A month ago my ISP sent information that they're upgrading my connection speed without increasing the monthly cost! Nice. Totally unexpected from them.

Couple weeks ago my internet connection had dropped during night and I just flicked the switch on the cable router and it all came back. What I didn't initially realize, that I had an IPv6-address! WHOA!
Given zero public information about this on their public website, customer portal or anywhere, I just saw that on my network interface while investigating an another issue. They are broadcasting router advertisements and allocating a /64 from 2A04:AE00::/26 (SE-COMHEM-20140210). It looks like this on radvdump:
interface enp1s0 {
AdvSendAdvert on;
# Note: (Min,Max)RtrAdvInterval cannot be obtained with radvdump
AdvManagedFlag on;
AdvOtherConfigFlag on;
AdvReachableTime 600000;
AdvRetransTimer 0;
AdvCurHopLimit 64;
AdvDefaultLifetime 9000;
AdvHomeAgentFlag off;
AdvDefaultPreference high;
AdvSourceLLAddress on;
AdvLinkMTU 1500;
}; # End of interface definition
Since the O-bit for "other" (AdvOtherConfigFlag on) is enabled, it means that a DHCPv6-request will get more usable information. A DHCPv6 lease will look like this:
lease6 { interface "enp1s0";
ia-na xx:xx:xx:xx {
starts 1512476381;
renew 302400;
rebind 483840;
iaaddr 2a04:ae07:yyyy:yy::yyyy {
starts 1512476381;
preferred-life 604800;
max-life 2592000;
}
option dhcp6.status-code success;
}
option dhcp6.client-id 0:1:2:3:4:5:6:7:8:9:a:b:c:d:e:f:10:11;
option dhcp6.server-id 0:1:0:1:53:f:97:74:0:50:56:a8:22:a4;
option dhcp6.name-servers 2a04:ae3a:ae3a::1,2a04:ae3a:ae3a::2;
}
It works and is fast and all, but ... (there's always the but part). Given SLAAC, they issue only a /64 prefix. Why is that a problem you ask. Well, to be able to issue an IPv6 address to all devices in my LAN, that's not enough.
I tried sending a Prefix Delegation -request via DHCPv6, but no. They didn't honor that request. Should that worked, I'd be happy. I'd have my own /48 prefix for my LAN-devices.
In the current form Com Hem's IPv6 is mostly useless as none of my actual devices have IPv6 addresses in them. I'm investigating this and if/when I find a solution for this, I'll post something about it. Meanwhile, if you know how to get a prefix out of them, please inform!
100-year-old Finland
Wednesday, December 6. 2017
Today, 6th of December 2017, Finland celebrates its 100 years of independency. That's very convenient, as I'm not there to celebrate with my fellow Finns! ![]()
Since somebody lured lot of other states to celebrate with them, lot of the world-known objects were light Finnish-blue. One location from the list is Globen ("-95 nevö föget!"), which is conveniently a brief tunnelbana ride away from my home. For some reason, there are no published pictures of Globen in it's celebratory lighting. So, here goes:
Ok. In reality, the place is called Ericsson Globe, but nobody calls it that. It's just Globen.

Saving the day - Android tethering with Linux
Sunday, December 3. 2017
The fail
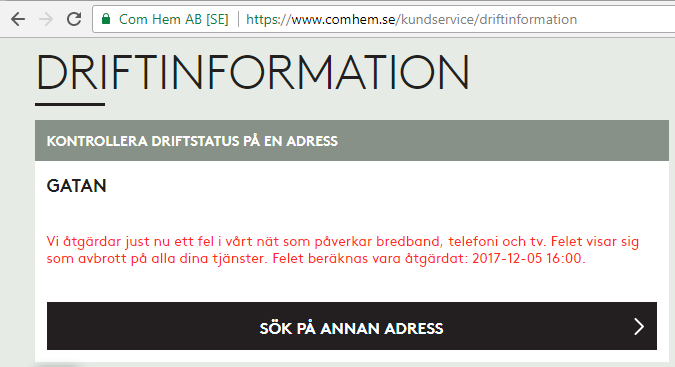
On a peaceful Sunday, I was just minding my own business and BOOM! Internet connection was gone. After a quick debugging session, restarting the router and eyeballing the LEDs, it was evident: something with my ISP Com Hem was down:
Ok, ISP down, what next?
I whipped up the iPhone and went for any possible service announcements. And yes, the above announcement was placed on my user account information. I was stunned by this, it was so cool to have:
- confirmation, that something was down with ISP: Yup, it's broken.
- that information tailored with the geographical location of my subscription: Yup, that fail affects you.
No Finnish ISP or telco has that. I was very impressed with such detail (and still am).
The fix
There is no way I'm sitting on my thumbs on such an event. I was just about to start playing Need for Speed and now Origin wouldn't even log me in, so, no Internet, no gaming.
I have an el-cheapo Huawei Android lying around somewhere, with a Swedish SIM-card in it. My dirt cheap subscription has couple of gigs data transfer per month in it, which I never use. I came up with a plan to temporarily use the cell phone as an Internet connection. The idea would be to hook it up into my Linux router with an USB-cable, make sure the Android pops up as a network interface and then configure the Linux to use that network interface as primary connection.
Thethering
I found tons of information about Android-tethering from Arch Linux wiki. It basically says:
- Make sure your Android is newer than 2.2
- Connect the phone to a Linux
- Enable USB-tethering from the phone's connection sharing -menu
- Confirm the new network interface's existence on the Linux end
On my phone, there was two settings for personal hotspot. Wifi/Bluetooth and USB:
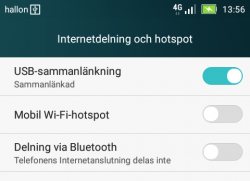
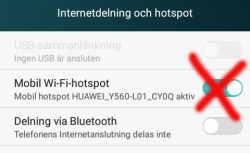
Connection
New phones have USB-C, but its such a new connector type, that anything older than couple years, has most likely micro-USB -connector:

Hooking it up to a Linux will output tons of dmesg and and ultimately result in a brand new network interface:
# ip addr show
5: enp0s20u4u3:
link/ether 82:49:a8:b4:96:c9 brd ff:ff:ff:ff:f
inet 192.168.42.90/24 brd 192.168.42.255 scope
valid_lft 3595sec preferred_lft 3595sec
inet6 fe80::7762:e1a9:9fa:69f5/64 scope link
valid_lft forever preferred_lft forever
Routing configuration
Now that there was a new connection, I tried pinging something in the wild world:
ping -I enp0s20u4u3 193.166.3.2
Nope. Didn't work.
I confirmed, that the default network gateway was still set up into the broken link:
# ip route show
default via 192.168.100.1 dev enp1s0 proto static metric 100
That needs to go to enable some functionality. But what to replace the bad gateway with?
Since the connection had IP-address from Telco DHCP, there is a lease-file with all the necessary information:
# cat /var/lib/NetworkManager/dhclient-*-enp0s20u4u3.lease
lease {
interface "enp0s20u4u3";
fixed-address 192.168.42.90;
option subnet-mask 255.255.255.0;
option routers 192.168.42.129;
The fixed-address in the file matches the above ip addr show -information. Required information was gathered, and the idea was to ditch the original gateway and replace it with a one from the Android phone's telco:
# ip route del default via 192.168.100.1
# ip route add default via 192.168.42.129 dev enp0s20u4u3
# ip route show
default via 192.168.42.129 dev enp0s20u4u3 proto static metric 101
Now it started cooking:
# ping -c 5 ftp.funet.fi
PING ftp.funet.fi (193.166.3.2) 56(84) bytes of data.
64 bytes from ftp.funet.fi (193.166.3.2): icmp_seq=1 ttl=242 time=35.6 ms
64 bytes from ftp.funet.fi (193.166.3.2): icmp_seq=2 ttl=242 time=31.7 ms
To finalize the access from my LAN, I ran following firewall-cmd --direct commands:
--remove-rule ipv4 nat POSTROUTING 0 -o enp1s0 -j MASQUERADE
--add-rule ipv4 nat POSTROUTING 0 -o enp0s20u4u3 -j MASQUERADE
--add-rule ipv4 filter FORWARD 0 -i enp3s0 -o enp0s20u4u3 -j ACCEPT
--add-rule ipv4 filter FORWARD 0 -i enp0s20u4u3 -o enp3s0 \
-m state --state RELATED,ESTABLISHED -j ACCEPT
There is no firewall-cmd --permanent on purpose. I don't intend those to stick too long. I just wanted to play the darn game!
Done!
Now my gaming PC would connect to The Big Net. I could suft the web, read mail and even Origin logged me in.
That's it! Day saved! ![]()
EBN European Business Number scam - Part 2 - Do not pay!
Saturday, December 2. 2017
Update 25th June 2019: EBN scammers bankrupt
Roughly an year ago I posted about EBN European Business Number scam. Now, an year later, it is one of the most commented article on my blog. At the time of posting, I was just pissed off about that stupid scam and wanted to inform and educate my readers about this and warn them for NOT to agree on their terms, nor pay anybody any money for it.
Then something that I didn't foresee or expect to happen happened: The article took off and thousands of people read it and dozens commented it. Looks like I stumbled into something big. The upcoming months proved, that this scamming corporation was operating all over Europe and doing their less-than-honest "business" of selling nothingness to unwary business owners.
Given the flood of comments, recently I found out that Raivo Laanemets, an Estonian software consultant, wrote about EBN scam back on 2015, over year before I did. Go read his blog post here. For the pointer, I'd like to thank Mr. Vaidas, who copy/pasted the comment from Mr. Laanemets' blog to mine.
This is the comment from June 2017 and contains following by Mr.(?) Gorila:
The critical claims made are:
- Person behind all this is Adrian Wittmer
- My comment: I'm not sure how to confirm this
- Mentioned Adrian Wittmer is actively involved in two companies: Credit Business Resolution s.r.o. and CCF Credit Collection Factoring s.r.o.
- My comment: I have not seen the threatening debt collector's letters, but in my previous EBN post comments, people have said, that the company doing the debt collecting is indeed Credit Collection Factoring s.r.o. from the Czech Republic
- Czech Republic legislation is more tolerant towards fraudsters
- My comment: I barely know parts of Finnish law, gaining understanding difference between German or Czech laws is way beyond me.
- Regulation (EC) No 1896/2006 of the European Parliament and of the Council of 12 December 2006 creating a European order for payment procedure
- My comment: The above mentioned regulation directs how payments of "low value" between companies. (16) says: "This would allow the court to examine prima facie the merits of the claim and inter alia to exclude clearly unfounded claims or inadmissible applications."
Article 7 (d) and (e) define, that EBN debt collectors need to establish basis for their claim and appropriate evidence.
Shortly: If EBN-scam can be proven as unfounded claim based on fraud, you don't have to pay.
- My comment: The above mentioned regulation directs how payments of "low value" between companies. (16) says: "This would allow the court to examine prima facie the merits of the claim and inter alia to exclude clearly unfounded claims or inadmissible applications."
- Mr. Wittmer has created a money-making-machine. First he sells a non-existing "service" for European Business Number, then he acts as an enforcer to collect his own debt from customers refusing to pay.
- My comment: Again, I'm not sure how to confirm this, but it sure looks like that!
What I found out to corroborate Mr.(?) Gorila's claims made is:
- A variation of EBN-scam has been running in Czech Republic since 1998. There is an article about the scam written in 2006.
- Articles about Intercable Verlag AG can be found back in 2003 in Swizerland.
- Intercable Verlag AG was raided by Swiss police in 2006 and placed in liquidation in 2009
- I found a ton of claims, that Mr. Wittmer was the managing director of Intercable Verlag, but was unable to verify that. I guess, I just have to assume, that the claim is true.
- Croatian authorities issued a warning against EBN scam in 2017. That binds Swiss Intercable Verlag AG into Dutch EU Business Register and German DAD Deutscher Adressdienst GmbH. That could be a proof, that same persons operate the scam.
- In September 2014 European Parliament issued a notice about on misleading offers from Deutsche Adressdienst GmbH (DAD). That document clearly states that all petitions against the DAD Gmbh have been "declared admissible".
Shortly: You don't have to pay!
There seems to be a lot of truth in his(?) comment.
Do not pay!
When going gets tough for you, just refer to European Parliament Petition 1176/2013, Petition 1180/2013 and Petition 1556/2013 to the judge. That should make things bouncing your way.



Now, beyond any doubt I know answers to two crucial questions:
1. Who is behind the EBN fraud?
and
2. Why the Debt Recovery business has relocated to Czech Republic?
1. Who is behind the EBN fraud
After short investigation of two debt recovery companies who are sending threatening letters to the victims of EBN fraud I have found out that the man behind the EBN fraud is a notorious fraudster Adrian Wittmer. Wittmer is well known as the CEO of Intercable Verlag AG and was involved internationally in many similar frauds.
He was prosecuted by the Swiss Police and his company in Germany was closed after the Police raid. He has relocated his business into Czech Republic which is more tolerant towards fraudsters.
Adrian Wittmer is a founder of at least five fraudulent companies in Czech Republic; two of them are still active whilst the other three were closed. All companies allegedly have no employees and negligible turnover More information about these companies you may find from public data of the Czech Business Register. (https://www.detail.cz/osoba/adrian-wittmer-varsavska-715-36-praha/Hmp7dwW27XI/).
2. Why the Debt Recovery business has relocated to Czech Republic.
In Germany, as well in the EU, debt recovery is legally regulated and must be carried out according to the law, in accordance to the Regulation (EC) No 1896/2006. This regulation describes payment procedure for claims not contested by the defendant. This regulation simplifies, speeds up and reduces the costs of litigation in cases involving more than one EU country. The problem for DAD/EBN is that procedure procedure applies just to cases where the claim is not contested.
In case of the defendants’ complaint the matter ends up at the court which would judge against DAD in accordance to German Laws and Judgement of the German Supreme court which has rendered EBN fraud impracticable in Germany. Therefore, DAD is keen to settle accounts out of the court, but German legislation opposes any other than the lawful debt recovery.
In the past some attempts have ended by the police investigation and imprisonment for 2,5 years (Mr. Wilk and Mr. Schnell from Rostock, Germany). Therefore, the illegal part of the busies is relocated to Czech Republic which favors fraudsters, or at least, doesn’t persecute them.
Two active companies founded and owned by Adrian Wittmer Credit Business Resolution s.r.o. CCF Credit Collection Factoring s.r.o are now sending threatening letters, representing themselves as acting on behalf of EBN/DAD. In reality, they are doing the second illegal part in the fraud which is punishable by the German laws. Hence DAD/EBN have relocated that part of the busies into Czech Republic.
EBN in Hamburg is just the first stage in the business: harvesting signatures, issuing invoices and is sending payment reminders. They do just the part which is not prosecuted in Germany by the Criminal Police. What they do is bordering on matters punishable by the German laws but remain at the safe side. Therefore, we may conclude that the whole EBN fraud is illegal according to the German laws and presents no treat to those who have returned signed forms to DAD. DO NOT PAY – Just ignore them and enjoy ongoing vacations.