De-bricking a B593-s22
Tuesday, May 17. 2016
I finally did it!
The unit has been non-functional for over a year now. See details in my previous post. But I got it back.
First, I'd like to clarify the myth of "equipment mode". Yes, that does exist. You'll know that your box is bricked and the reason for that is because you're in equipment mode, as your RS-232 -console output will say following during boot-up:
now in wifi mfg
g_Equip_Mode_value = 1
What needs to be done, is getting that Equip_Mode flag off. On "normal" mode bootup, two distinct differences appear at the output:
now in wifi release
normal mode, no need to load RF wifi
and
g_Equip_Mode_value = 0
My sincere thanks goes to Mr. Jevgenij for telling me a magical NVRAM-location to look at.
The brick
My bricked B592 s-22 (in equipment mode) looked like this on a boot sequence:

(Sorry about the signal LED glowing, that was my failure when lighting the box for video. I didn't realize that on my footage it looks like being lit, while in reality it isn't. A bricked box won't show any signal there.)
At power-on, the Power-LED gets lit all the others are off. Then the boot-sequence handles lot of hardware and gets a Linux to boot. They call it the "early init". There are no differences between modes at that point.
Next, what happens is the Linux-side taking control and starting to spin up services. One of the first things it does is kicking all the LEDs lit. When enough services are on, and Linux wants to fiddle with LTE-side all the LEDs go off. Now that the device is configured not to offer all hardware services to Linux-side, rest of the boot sequence goes haywire. There is no Wi-Fi, there is no Ethernet-bridge and lot of stuff fail during boot. Your best clue about this dreaded equipment mode is the Tel LED blinking on/off forever. Actually the box is not doing much at that point. It has given up all hope on getting a handle of the LTE-side or the Ethernet bridge.
Luckily, the box is sane enough to allow a SSH-login. In equipment mode, it will bypass the ATP Cli completely and land at the BusyBox-prompt. There your friend is lteat-command. Go back to my older stuff, for details about that.
The fix
The prerequisite for the fix is, that you are logged into your B593 s-22 via SSH and are able to run lteat and get sensible response out of it. Example (the blank lines happen on my SSH, I don't know why):
# lteat
AT>ati
i
Model: B593s-22
Revision: V200R001B180D20SP05C260
IMEI: 860091028600910
+GCAP: +CGSM,+DS,+ES
OK
AT>
Then you're good to go.
First confirm, that you are in the equipment mode:
AT>at ^nvrd=52110
^NVRD: 12,31 00 00 00 00 00 00 00 00 00 00 00
OK
That's a ReaD-command for NVRAM address location 52110. To change the mode back to normal, a WRite needs to be issued:
AT>at ^nvwr=52110,1,0
OK
Confirm the result:
AT>at ^nvrd=52110
^NVRD: 12,00 00 00 00 00 00 00 00 00 00 00 00
OK
Notice how the hex value 0x31 is changed to 0x00. Btw. if you look at the ASCII-table, you may notice, that 0x31 stands for number 1. That's would be similar to the (1) in g_Equip_Mode_value = 1.
Now all you have to do is power-off your box and kick it back on.
Finally
I don't have a clue why/how/when my box went into this "stupidity"-mode. I was fiddling with the LTE-side at lteat-prompt when it happened. I did try dozens of different commands, any of those may have caused that.
Also, if you're unable to SSH into your box, you may need to read my or somebody else's articles. It's all explained there.
Huawei B593 s-22 more RS-232 pins
Tuesday, March 24. 2015
After poking a s-22 around with an oscilloscope I managed to find a serial signal out of it. However, Mr. Asiantuntijakaveri pointed out, that it isn't especially useful. To him that serial stuff looked like the mobile-side baseband. Couple of hours tinkering with VxWorks prompt didn't result much for me. So, back to the scope ...
Another 1,8 volt serial signal. RS-232 parameters are alike the other one 115200 bps 8N1. I couldn't confirm the DCE RX-pin. There is one with suitable electrical characteristics, but it looks like the box doesn't offer any input capabilities, not at least with default configuration.
The data on boot time looks like this:
v?l?space?write magic succsse!%x
24680138%s start addr:0x%x size:0x%x
first step
second step
thred step
DDR exam right !!!!!!!!!!!!!!!!!!!!!!!
press space key to enter bootrom:
Start from: vxWorks Kernel.
>>loading: VxWorks ... success.
>>loading: FastBoot ... success.
hw main id:00000400, sub id:00000001activate_fastboot...0x3CD00000
Starting from entry: 0x30004000
[ 0.000000] Linux version 2.6.35.7 (q81003564@MBB-V7R1-CPE) (gcc version 4.5.1 (ctng-1.8.1-FA) ) #1 PREEMPT Mon Jun 3 13:50:16 CST 2013
[ 0.000000] CPU: ARMv7 Processor [413fc090] revision 0 (ARMv7), cr=18c53c7f
[ 0.000000] CPU: VIPT nonaliasing data cache, VIPT nonaliasing instruction cache
[ 0.000000] Machine: Hisilicon Balong
[ 0.000000] Ignoring unrecognised tag 0x4d534d70
[ 0.000000] Memory policy: ECC disabled, Data cache writeback
[000005940ms] Built 1 zonelists in Zone order, mobility grouping on. Total pages: 36576
[000005941ms] Kernel command line: root=/dev/ram0 rw console=ttyAMA0,115200 console=uw_tty0 rdinit=/init mem=144m
[000005941ms] PID hash table entries: 1024 (order: 0, 4096 bytes)
[000005941ms] Dentry cache hash table entries: 32768 (order: 5, 131072 bytes)
[000005942ms] Inode-cache hash table entries: 16384 (order: 4, 65536 bytes)
[000005957ms] Memory: 144MB = 144MB total
[000005957ms] Memory: 133780k/133780k available, 13676k reserved, 0K highmem
[000005957ms] Virtual kernel memory layout:
[000005957ms] vector : 0xffff0000 - 0xffff1000 ( 4 kB)
[000005957ms] fixmap : 0xfff00000 - 0xfffe0000 ( 896 kB)
[000005957ms] DMA : 0xff600000 - 0xffe00000 ( 8 MB)
[000005957ms] vmalloc : 0xc9800000 - 0xf0000000 ( 616 MB)
[000005957ms] lowmem : 0xc0000000 - 0xc9000000 ( 144 MB)
[000005957ms] modules : 0xbf000000 - 0xc0000000 ( 16 MB)
[000005957ms] .init : 0xc0008000 - 0xc0028000 ( 128 kB)
[000005958ms] .text : 0xc0028000 - 0xc06ca000 (6792 kB)
[000005958ms] .data : 0xc06ca000 - 0xc0701520 ( 222 kB)
[000005958ms] SLUB: Genslabs=11, HWalign=32, Order=0-3, MinObjects=0, CPUs=1, Nodes=1
[000005958ms] Preemptable hierarchical RCU implementation.
[000005958ms] RCU-based detection of stalled CPUs is disabled.
[000005958ms] Verbose stalled-CPUs detection is disabled.
[000005958ms] NR_IRQS:160
[000005958ms] Console: colour dummy device 80x30
[000005958ms] Calibrating delay loop... 897.84 BogoMIPS (lpj=4489216)
[000006218ms] pid_max: default: 4096 minimum: 301
[000006218ms] Mount-cache hash table entries: 512
[000006218ms] CPU: Testing write buffer coherency: ok
[000006219ms] start log trace.
[000006223ms] NET: Registered protocol family 16
[000006224ms] Serial: BalongV7R1 UART driver
[000006224ms] dev:uart0: ttyAMA0 at MMIO 0x90007000 (irq = 102) is a Balong rev0
[000006435ms] console [ttyAMA0] enabled
[000006461ms] bio: create slab at 0
[000006465ms] hi_gpio_probe:gpio sync in acore.
[000006469ms] hi_gpio_probe:gpio sync over.
[000006474ms] SCSI subsystem initialized
[000006478ms] enter Acpu-softtimer-modeule-init!!!
[000006482ms] softtimer_module_start_success-,1-- >>>>>>>>>>>>>>
[000006488ms] start create the softtimer thread!!!
[000006492ms] end the Acpu_softtimer_init() !!!
[000006497ms] usbcore: registered new interface driver usbfs
[000006503ms] usbcore: registered new interface driver hub
[000006508ms] usbcore: registered new device driver usb
[000006513ms] ***************************************************************
[000006520ms] begin to init mutilcore: 0000
[000006524ms] hw id: main,0x400, sub,0x1
[000006528ms] ===== beg mem usr function =====
[000006532ms] begin to init mutilcore: 222
[000006536ms] start BSP_ICC_Init
[000006539ms] g_pstIccCtrlChan = 0xf2fc02c0
[000007098ms] ##### icc init success!, cnt=1971, connet=1
[000007103ms] end BSP_ICC_Init
[000007106ms] begin to init mutilcore: 333
[000007110ms] begin to init mutilcore: 444
[000007113ms] BSP_MODU_IFCP
IFC Process init success!
[000008606ms] A:start icc cshell...
[000008609ms] cshell_icc_open success,cshell_udi_handle is 5898241
[000008615ms] free_ok
[000008617ms] the lcr_reg is 3
[000008620ms] pTemp is 0xc8a90000
[000008623ms] UDI_BUILD_DEV_ID is 0x300
[000008626ms] start NVM_Init
[000008629ms] MSP_IPC udi_open Start
[000009297ms] MSP_IPC udi_open End Handle = 5a0002
[000009715ms] end NVM_Init
[000009718ms] begin to init mutilcore: 555
[000009721ms] BCM43239_WIFI_Release: Entering...
[000009726ms] DRV_HSIC_Release: Entering ...
Actually there is like 1000 lines more log, but it's just Linux loading. Including in the log there are SSH-passwords for 2 users admin and user. They are exactly what sshusers.cfg will have after boot.
It will take couple of seconds for the bootloader to kick on the Android-side. The bootloader serial-data starts flowing in immediately, but this one sleeps a while and starts after that.
Side buttons exaplained
I have previously touched the subject of WiFi / Reset / WPS -buttons. Also I got a comment about un-bricking a s-22, but that didn't help me much. This is related to serial output in a sense, that pressing the buttons will have effect on the serial output.
Now that I have a clear view of what's happening at the box I'd like to take this opportunity of describing the three buttons' behaviour:
- (device running normally) WiFi button pressed for over 1 second: WiFi on/off
- no surprises there, you can do this from Web-GUI too
- (device running normally) Reset button pressed for over 2 seconds: Factory reset
- (device running normally) Reset button pressed for less than 2 seconds: no-operation
- (device running normally) WPS button pressed: on/off
- no surprises there, you can do this from Web-GUI too
- (device running normally) WiFi and WPS buttons pressed: no special functionality, will toggle WiFi and WPS as they would be pressed separately
- (device running normally) WiFi, Reset, WPS buttons pressed: no special functionality
- (device not powered) WiFi button pressed while powering on: baseband (VxWorks) serial console displays Android console briefly and stops
- Linux-side serial console will be completely silent
- (device not powered) WPS button pressed while powering on: no-operation
- (device not powered) Reset button pressed while powering on: no-operation
- (device not powered) WiFi and WPS buttons pressed while powering on: enter bootloader menu
- (device not powered) WiFi, Reset and WPS buttons pressed while powering on: enter bootloader menu
If you have other suggestions about the buttons, please drop me a comment.
Huawei B593 s-22 RS-232 pins
Thursday, March 19. 2015
As I told earlier, I bricked one. It was a loaned one, so I really got burned on that. There was not much to do, but pop the hood of the s-22 and hope to find something interesting there. An interesting thing would be serial console (RS-232) or JTAG.
There are 3 Phillips PH-2 screws holding the unit together. One screw always has a thin paper on top of it. It is a "Huawei-thing". If the paper is broken, it will void your warranty. Remove the 3 screws, and you can pry the box open:

Then the front cover is gone, you have the wrong side of the motherboard in front of you. You need to detach the MoBo from the back cover. There are 4 Phillips PH-2 screws holding it:

Now you're seeing the real thing:

Here is a layout of all the good stuff:

Mr. Asiantuntijakaveri gave me a hint to check couple pins near the CPU for serial signal. I attached an oscilloscope into couple of interesting pins and got following:
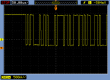

Definitely an RS-232 signal. Based on the timings, looks like 115200 bps. Just as in B593 u-12. The only thing was about the voltage. My scope said 1,792 volts peak-to-peak. That's way too low for my 3,3 volt TTL to RS-232 converter. I put in a purchase order for more capable (expensive) adapter and eventually UPS-guy brought it to me:

The one I have is Future Technology Devices International TTL-232RG, TTL-232RG-VREG1V8-WE to be specific. Their spec says: VREG1V8 = USB to UART cable with +5 to +1.8V TTL level UART signals and WE = wire end. A Linux sees it as a Bus 005 Device 004: ID 0403:6001 Future Technology Devices International, Ltd FT232 USB-Serial (UART) IC. It is fully working after plugging in both on a Linux and Windows 7.
I put this into a PuTTY (115200 N81, no flow control):
And yes, there are results:
onchip
NF_boot!
UnSec_boo
v?l?space?%s start addr:0x%x size:0x%x
first step
second step
thred step
DDR exam right !!!!!!!!!!!!!!!!!!!!!!!
press space key to enter bootrom:
Start from: vxWorks Kernel.
>>loading: VxWorks ... success.
>>loading: FastBoot ... success.
hw main id:00000400, sub id:00000001activate_fastboot...0x3CD00000
Starting from entry: 0x30004000
That's it no more. Not very useful. Then Mr. Asiantuntijakaveri gave me another hint. Try the three-finger-salute, press WiFi, Reset and WPS buttons and then kick on the power. An u-12 will go to some sort of serial-console service mode. And yes, a s-22 does the same. All I have to do is have all three buttons pressed, kick the power on and immediately release all them. Now I have on serial:
first step
second step
thred step
DDR exam right !!!!!!!!!!!!!!!!!!!!!!!
press space key to enter bootrom:
enter load backup
IMAGE_BOOTROM load from:0x00340000>>loading: BootRom ... try inflate.
image length: 000A412A
ram_inflate_addr: 34F4382E
inflating...
return value: 00000000
inflate success! data check OK!
hw main id:00000400, sub id:00000001Starting from entry: 0x300040Target Name: vxTarget
Adding 5472 symbols for standalone.
]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]
]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]
]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]
]]]]]]]]]]] ]]]] ]]]]]]]]]] ]] ]]]] (R)
] ]]]]]]]]] ]]]]]] ]]]]]]]] ]] ]]]]
]] ]]]]]]] ]]]]]]]] ]]]]]] ] ]] ]]]]
]]] ]]]]] ] ]]] ] ]]]] ]]] ]]]]]]]]] ]]]] ]] ]]]] ]] ]]]]]
]]]] ]]] ]] ] ]]] ]] ]]]]] ]]]]]] ]] ]]]]]]] ]]]] ]] ]]]]
]]]]] ] ]]]] ]]]]] ]]]]]]]] ]]]] ]] ]]]] ]]]]]]] ]]]]
]]]]]] ]]]]] ]]]]]] ] ]]]]] ]]]] ]] ]]]] ]]]]]]]] ]]]]
]]]]]]] ]]]]] ] ]]]]]] ] ]]] ]]]] ]] ]]]] ]]]] ]]]] ]]]]
]]]]]]]] ]]]]] ]]] ]]]]]]] ] ]]]]]]] ]]]] ]]]] ]]]] ]]]]]
]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]
]]]]]]]]]]]]]]]]]]]]]]]]]]]]] Development System
]]]]]]]]]]]]]]]]]]]]]]]]]]]]
]]]]]]]]]]]]]]]]]]]]]]]]]]] VxWorks 6.8
]]]]]]]]]]]]]]]]]]]]]]]]]] KERNEL: WIND version 2.13
]]]]]]]]]]]]]]]]]]]]]]]]] Copyright Wind River Systems, Inc., 1984-2009
CPU: ARM RealView PBX-A9. Processor #0.
Memory Size: 0x4efa000. BSP version 2.0/0.
Created: Jun 03 2013, 13:52:34
ED&R Policy Mode: Deployed
-> GU base addr: 0x3e200000
HIFI base addr: 0x3f800000
===== beg mem usr function =====
Hisilicon NANDC_V4.00 initialize...
NAND device: Manufacturer ID: 0xad, Chip ID: 0xbc (Hynix NAND 512MiB 1,8V 16-bit)
ptable_yaffs_mount: /yaffs0 ...yaffs: Mounting /yaffs0
yaffs: yaffs_GutsInitialise()
yaffs: yaffs_GutsInitialise() done.
OK.
ptable_yaffs_mount: /yaffs1 ...yaffs: Mounting /yaffs1
yaffs: yaffs_GutsInitialise()
yaffs: yaffs_GutsInitialise() done.
OK.
ptable_yaffs_mount: /yaffs2 ...yaffs: Mounting /yaffs2
yaffs: yaffs_GutsInitialise()
Collecting block 1136, in use 39, shrink 0, wholeBlock 0
Collecting block 1136, in use 34, shrink 0, wholeBlock 0
Collecting block 1136, in use 29, shrink 0, wholeBlock 0
Collecting block 1136, in use 24, shrink 0, wholeBlock 0
Collecting block 1136, in use 19, shrink 0, wholeBlock 0
Collecting block 1136, in use 14, shrink 0, wholeBlock 0
Collecting block 1136, in use 9, shrink 0, wholeBlock 0
Collecting block 1136, in use 4, shrink 0, wholeBlock 0
yaffs: yaffs_GutsInitialise() done.
OK.
ptable_yaffs_mount: /yaffs5 ...yaffs: Mounting /yaffs5
yaffs: yaffs_GutsInitialise()
yaffs: yaffs_GutsInitialise() done.
OK.
Collecting block 301, in use 34, shrink 0, wholeBlock 0
Collecting block 301, in use 29, shrink 0, wholeBlock 1
0x34ef9d7c (tRootTask): PMU PWR IRQ1 : 0x0
0x34ef9d7c (tRootTask): PMU PWR IRQ2 : 0x20
0x34ef9d7c (tRootTask): PMU PWR IRQ3 : 0x0
0x34ef9d7c (tRootTask): PMU REG IRQ1 : 0x0
0x34ef9d7c (tRootTask): PMU REG IRQ2 : 0x20
0x34ef9d7c (tRootTask): PMU REG IRQ3 : 0x0
0x34ef9d7c (tRootTask): PMU REG H_N_STATUS(0x43) : 0x0
0x34ef9d7c (tRootTask): PMU REG H_N_STATUS(0x44) : 0x0
0x34ef9d7c (tRootTask): PMU FLAG REG 0x4 : 0x0
0x34ef9d7c (tRootTask): PMU FLAG REG 0x5 : 0x0
0x34ef9d7c (tRootTask): PMU FLAG REG 0x6 : 0x0
0x34ef9d7c (tRootTask): PMU FLAG REG 0x7 : 0x5
0x34ef9d7c (tRootTask): PMU FLAG REG 0x8 : 0x0
0x34ef9d7c (tRootTask): hw main id:0x400, sub id:0x1
0x34ef9d7c (tRootTask): PMU NVM_Read ERROR.
0x34ef9d7c (tRootTask): getFactoryMode:not in factory mode!
0x34ef9d7c (tRootTask): BootRom update_getWebUIUpdateFlag: 0x8B6A7024
0x34ef9d7c (tRootTask): dloadIsDoBackupUpdate: need to do the backup update!
0x34ef9d7c (tRootTask): getBackupBinState: open file failed!
0x34ef9d7c (): task deadexcutePreBackupUpdate: the backup bin is invalid!
0x34ef9d7c (): task deadclearBkupUpdateFlag: succeed to clear the backup update flag!
0x303c32f0 (tUSBTask): BSP_USB_GetDevDescIdx: MDM+PCUI+DIAG in Bootrom image
0x303c32f0 (tUSBTask): Starting USBware stack, Version 3.4.30.21
Oh yes! I was getting somewhere. On an enter I got a prompt and threw in some commands:
[M]->?
C interp: syntax error.
[M]->help
help Print this list
dbgHelp Print debugger help info
edrHelp Print ED&R help info
ioHelp Print I/O utilities help info
nfsHelp Print nfs help info
netHelp Print network help info
rtpHelp Print process help info
spyHelp Print task histogrammer help info
timexHelp Print execution timer help info
h [n] Print (or set) shell history
i [task] Summary of tasks' TCBs
ti task Complete info on TCB for task
sp adr,args... Spawn a task, pri=100, opt=0x19, stk=20000
taskSpawn name,pri,opt,stk,adr,args... Spawn a task
tip "dev=device1#tag=tagStr1", "dev=device2#tag=tagStr2", ...
Connect to one or multiple serial lines
td task Delete a task
ts task Suspend a task
tr task Resume a task
Type to continue, Q or q to stop:
tw task Print pending task detailed info
w [task] Print pending task info
d [adr[,nunits[,width]]] Display memory
m adr[,width] Modify memory
mRegs [reg[,task]] Modify a task's registers interactively
pc [task] Return task's program counter
iam "user"[,"passwd"] Set user name and passwd
whoami Print user name
devs List devices
ld [syms[,noAbort][,"name"]] Load stdin, or file, into memory
(syms = add symbols to table:
-1 = none, 0 = globals, 1 = all)
lkup ["substr"] List symbols in system symbol table
lkAddr address List symbol table entries near address
checkStack [task] List task stack sizes and usage
printErrno value Print the name of a status value
period secs,adr,args... Spawn task to call function periodically
repeat n,adr,args... Spawn task to call function n times (0=forever)
version Print VxWorks version info, and boot line
shConfig ["config"] Display or set shell configuration variables
Type to continue, Q or q to stop:
strFree [address] Free strings allocated within the shell (-1=all)
NOTE: Arguments specifying 'task' can be either task ID or name.
value = 10 = 0xa
[M]->
I don't yet know what to do with all that, but ... if I do, I'll tell about it. The part "press space key to enter bootrom" sounds interesting. I don't know if I can un-brick this thing from VxWorks-side.
So, about the pins. First a ground is needed. Typically it's available almos everywhere. There are couple of easy points to get the ground from, especially in the PSU-area. Of all the easily available GND-pins I chose this one:

The choice was made by a simple logic, it was just an easy one to solder. Then the RS-232 DCE pins at the CPU-unit:


The metallic thing is simply a cover, the actual CPU is under that hood. I did check that one out, but I didn't find anything interesting under that one. Also understand about serial signals, that transmit and receive are from the point of the router (DCE), not from your computer (that would be DTE). You can think of it like this: when DCE transmits (TX), it will go to receive (RX) of a DTE.
If you do your own hacks, know that the power system on a s-22 is weird one. Input is 12 VDC, majority of the Vcc pins have 5 VDC, but I seriously doubt that the system would run on that voltage. If you need it, there is one easily accessible pin with 3,3 VDC:

At the time of writing, the box is still bricked. But this time I have something to work with.
Update 24th Mar 2015:
There is more information available about this subject in this article.
First B593 s-22 exploit: Setup FTP to get /var/sshusers.cfg
Monday, February 23. 2015
I have a new version of B593_exploit.pl published. See this article about previous info.
This version has s-22 FTP hack added to it. u-12 has the classic FTP USB-share flaw where it is possible to create a FTP share of the /. Unfortunately in this box Huawei guys made the web GUI a bit smarter, you cannot do such a nice share anymore. The fortunate part is, that the guys don't check for that at the save. ![]() If you manage to lure the ../.. past the GUI, you can do it. That's what the exploit is about.
If you manage to lure the ../.. past the GUI, you can do it. That's what the exploit is about.
Example run:
./B593_exploit.pl 192.168.1.1 admin --ftp-setup \ ftpuser ftppassword
That command will share the first USB-device found at the filesystem root of the box. You have to have a physical USB-storage attached. It doesn't have to have anything on it and it won't be affected during the process. But setting a path will fail, if there is no USB-storage.
I had problems with the FTP-client, it kept complaining about FTP passive mode. I switched the client into NcFTP and that solved my problem.
When in the box the SSH passwords are at the classic /var/sshusers.cfg. If configuration is of interest to you, it can be found from /app/curcfg.xml. When the admin user's password is known, it is only a trivial task to SSH into the box and gain a shell access.
While looking around the box, I got carried away with the lteat-command. I managed to brick the box. ![]() But that's an another story.)
But that's an another story.)
New features to curcfg_tool [Failure]
Sunday, October 19. 2014
The original post about curcfg_tool.
So I decided to add couple of new features to my tool. However, neither of of them work. ![]()
Asiantuntijakaveri-blog introduced hack to run commands on boot: Persistent customizations to Huawei B593u with stock firmware. I added a feature to do that:
./curcfg_tool -rc "update-westerneurope.huaweidevice.com ; /upgflash/init.d/rc.local" -w
The flaw is in the httpupg-command startup. It takes the server address from curcfg.xml, but it doesn't escape it properly. This makes it possible to piggy-back any command on it. The thing is, that in my B593, the automatic firmware upgrade does not run automatically. I can go trigger it manually. At that point it runs my script I created at /upgflash/init.d/rc.local. My hope was, that system would run it automatically on bootup, but it doesn't.
Another thing I added was NTP-server change. I don't know where the list comes from, in my case it is completely ridiculous. However, the source for information is not from curcfg.xml. For example:
./curcfg_tool -ntp1 ntp.dnainternet.fi -ntp2 fi.pool.ntp.org -w
... doesn't change anything. The new servers don't appear at the list in GUI, nor the system doesn't update time from them.
Crap! Both attempts failed miserably. Please drop me a comment if you have anything to add to those ones.
Introducing curcfg_tool: Utility to make changes to your configuration
Tuesday, September 16. 2014
As I have promised a number of times to number of people. Here it finally is! The first version of my tool to alter your B593 configuration. With this tool you can change admin passwords for web GUI and SSH to something of your liking. It does not (yet) convert plaintext passwords into encrypted ones, but it successfully writes the changes to flash, thus making them permanent.
Prerequisites
- Huawei B593 u-12
- Access to your box for running commands, telnet/SSH are really good options for this
- While at Busybox sh prompt, internet connectivity via the mobile interface (4G/3G/2G)
Getting the tool
The MIPS32 binary version suitable for running at your B593 is at http://opensource.hqcodeshop.com/Huawei%20B593/curcfg/latest. The C source code is also available at: http://opensource.hqcodeshop.com/Huawei%20B593/curcfg/
- Log into your box
- (recommended) Change into directory /upgflash/
- Download the binary into your box:
wget -g -v -l curcfg_tool -r "/Huawei%20B593/curcfg/latest" opensource.hqcodeshop.com - As you can see, Busybox has a mighty quirky wget!
- Anyway, that command will download the tool from the above URL and place it to the current directory with local name curcfg_tool.
- Also note, that your box must have a functioning Internet access for download. The only other viable option is via FTP-hack. The environment is very limited and file transfers are restricted heavily.
- Make sure, that the file is executable:
chmod a+x curcfg_tool
Running the tool
Now that you have the thing sitting there, run it:
# ./curcfg_tool
Usage:
-V - Print version information
-cw <base64 encoded web gui password> - set password
-cs <base64 encoded SSH password> - set password
-w - write changes to flash (default: don't write)
-fi <file name> - input file (default: read from flash)
-fo <file name> - write changes (default: /tmp/flashinfo.bin)
An example of resetting the web-GUI password would be:
# ./curcfg_tool -cw f5338SA1kb4= -w
Read data: addr = 0xe00000, len = 0x4 ...
Begin write to file
Export done
Reading 25785 bytes of config
Read data: addr = 0xe00000, len = 0x64bd ...
Begin write to file
Export done
Writing 25785 bytes of config
/tmp/flashinfo.bin size = 25790 Bytes
Read file done
Begin write to flash
Load file done
The magicical Base64 encoded 3-DES encrypted string f5338SA1kb4= is "admin" in plain text. After a reboot (just say reboot at prompt), you can login into your web-GUI and change the password into something of your liking.
What next?
That's pretty much it as of now. If you don't like your operator designated passwords, you can change them.
How do I ...
- ... see what my current password is:
You cannot. Encryption key is not known for pre-SP100 firmware and SP100+ firmware is using double encryption with 3-DES and AES and entire flow of information is not yet known. - ... access the prompt of my box:
See B593_exploit.pl for details. - ... access the prompt of my box, but I have SP100+ firmware and don't know any of my passwords:
You cannot. Yet. Currently known exploits have been fixed preventing access.
However, in this case the real question seems to be: "How did you get your box running in the first place?" - ... run the B593_exploit.pl -tool, my Perl isn't working:
You may want to install all CPAN-modules the script requires. Also skip the Windows and use a proper computer.
u-12 pre-SP100 exploits in a single tool
Monday, September 15. 2014
I created a new tool to obsolete the classic B593cmd.pl ping-exploit tool. I wrote that one almost a year ago to run any commands on your B593. That could be used to lift IPtables restrictions or get your sshusers.cfg contents.
Now that Mr. Ronkainen found out that pre-SP100 firmwares have another flaw, which is much more simpler to exploit, I wrote a tool to combine both of them into a single package.
Neither one of these work in SP100+ firmwares, but not to worry! They have SSH-port open for full access anyway. So ... getting a SP100+ firmware into your box should be your target anyway. This tool can help you gain access to your box.
The B593_exploit.pl tool is at http://opensource.hqcodeshop.com/Huawei%20B593/exploit/latest.pl. In the top of the file there is a list of Perl-modules it requires to run. You will get the complaints, if any are missing. Usage:
./B593_exploit.pl --help
Usage: B593_exploit.pl
--help|-h This help
--run-cmd Run a command: pre SP-100 ping-exploit
to run any command via web-console
--telnet-login Login via telnet: lift IPtables firewall from telnet and login
Ping-exploit -mode
This is the classic. Run example:
./B593_exploit.pl --run-cmd 192.168.1.1 admin "iptables -nL INPUT"
There are couple of bugs fixed, it should be more robust and has --debug -mode in it.
Telnet-exploit -mode
This is the newer one. Run example:
./B593_exploit.pl --telnet-login 192.168.1.1
Attempt 1 telnetting to 192.168.1.1
BusyBox vv1.9.1 (2012-03-01 14:00:34 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# iptables -nL INPUT
Ok. It's not a full telnet-client like you'd a regular telnet to be. This emulates one with Perl's Term::Readline, so your vi won't work or tab-based command-line completion. However, it has enough power in it to allow you to run commands and display contents of the files or fiddle with your IPtables.
In my next post I'm about to release a tool for editing and storing values of your curcfg.xml. This is a prerequisite, getting to the prompt and running stuff on the prompt is a must-have.
B593 u-12 /etc/ PEM-files explained
Monday, August 18. 2014
During the quest of hacking my u-12, Mr. Ronkainen from blog.asiantuntijakaveri.fi insisted, that the certificate files in /etc/ are actually used. My personal belief was, that the purpose of having those would be something not-so-important. It turned out, that I badly misjudged the situation.
My firmware has these files:
# cd /etc/
# ls -l *pem
-rwxrwxrwx 1 0 0 963 privkey.pem
-rwxrwxrwx 1 0 0 963 privkey.b593pem
-rwxrwxrwx 1 0 0 3700 cachain.pem
-rwxrwxrwx 1 0 0 1751 b593cpekey.pem
Please note, that the files are in a Read-Only -partition. They are not unique to my device! Your u-12 should have the exactly same files like I do. Also note, that pre-SP100 firmwares are using different encryptions and may not have those (I didn't bother to check).
The cachain.pem is the trivial one. It contains two CA-certificates issued by Huawei expiring 2040 or so. That is a very common PKI-procedure to have the public certificates in a device to make sure, that the actual certificate being used can be verified to a trusted root-CA. There is very little interesting about that file.
However, the remaining PEM-files are more interesting. The exact purpose of b593cpekey.pem is yet unknown. It is an 3-DES encrypted private key to something. If you want to take a peek into the file, the encryption password is CPE-B593-12 as Mr. Ronkainen dug out of the libraries. A command like this will tell us more:
# openssl rsa -in b593cpekey.pem -noout -text -passin pass:CPE-B593-12
Private-Key: (2048 bit)
...
It is a 2048-bit RSA key. If you know what the key is used for, please tell us.
The remaining files privkey.pem and privkey.b593pem are exactly the same. To me it looks like poor engineering. Libraries seem to be using the latter filename, but my guess is, that somebody is using the first one too. The password for this private key was also recovered by Mr. Ronkainen, it is lteb593. Basic information recovery:
# openssl rsa -in privkey.pem -noout -text -passin pass:lteb593
Private-Key: (1024 bit)
...
Hm. handy, but the really interesting part is where this file is actually used. This information was recovered by Mr. Ronkainen with looking at the GUI admin traffic via Wireshark.
If you go change the admin password at System -> Password change (the frame source would be http://-the-IP-here-/html/management/account.asp), you can see the HTML containing tags for loading a number of JavaScript files, the most interesting ones are /js/account.js and /js/rsa.js. The actual password change code from account.js is:
function AddSubmitParam(SubmitForm,type)
{
var cfgUsername = ADMIN_USER_NAME;
SubmitForm.addParameter('cfgUsername',cfgUsername);
SubmitForm.addParameter('Userpassword',MyRSAEncryptB64(getValue('id_cfmPassword')));
//SubmitForm.addParameter('Username',ADMIN_USER_NAME);
SubmitForm.addParameter('OldPassword',MyRSAEncryptB64(getValue('id_oldPassword')));
SubmitForm.setAction('chgacount.cgi?RequestFile=/html/management/account.asp');
It RSA-encrypts the value from form field with id id_cfmPassword! Wow! They really beefed up their security. The RSA-code is at /js/rsa.js and it contains:
// Return the PKCS#1 RSA encryption of "text" as a Base64-encoded string
function RSAEncryptB64(text) {
var h = this.encrypt(text);
if(h) return hex2b64(h); else return null;
}
...//my encrypt function, using fixed mudulus
var modulus = "BEB90F8AF5D8A7C7DA8CA74AC43E1EE8A48E6860C0D46A5D690BEA082E3A74E1"
+"571F2C58E94EE339862A49A811A31BB4A48F41B3BCDFD054C3443BB610B5418B"
+"3CBAFAE7936E1BE2AFD2E0DF865A6E59C2B8DF1E8D5702567D0A9650CB07A43D"
+"E39020969DF0997FCA587D9A8AE4627CF18477EC06765DF3AA8FB459DD4C9AF3";
var publicExponent = "10001";
function MyRSAEncryptB64(text)
{
var rsa = new RSAKey();
rsa.setPublic(modulus, publicExponent);
return rsa.encrypt_b64(text);
}
It surely is RSA PKCS#1 encryption implemented with JavaScript. That's really cool! A complete PKCS#1 library implemented with a completely wrong language. ![]() I didn't realize, that having a fully functional RSA-library with JavaScript was even possible, but there it is.
I didn't realize, that having a fully functional RSA-library with JavaScript was even possible, but there it is.
Next I took the public key modulo and exponent from the above JavaScript-code and used Per Olesen's tool from https://gist.github.com/polesen/2855098 to re-create an actual PEM-file from those ingredients. Mr. Olesen has a nice article Converting RSA public key Modulus and Exponent into PEM file about that.
The resulting PEM-file is:
-----BEGIN PUBLIC KEY-----
MIGeMA0GCSqGSIb3DQEBAQUAA4GMADCBiAKBgQC+uQ+K9dinx9qMp0rEPh7opI5o
YMDUal1pC+oILjp04VcfLFjpTuM5hipJqBGjG7Skj0GzvN/QVMNEO7YQtUGLPLr6
55NuG+Kv0uDfhlpuWcK43x6NVwJWfQqWUMsHpD3jkCCWnfCZf8pYfZqK5GJ88YR3
7AZ2XfOqj7RZ3Uya8wICJxE=
-----END PUBLIC KEY-----
and a simple verify run with OpenSSL for both the private and public keys confirm, that we have a pair:
# openssl rsa -pubin -in privkey.pub.pem -noout -modulus | md5sum
92e88d0b38fe93cd41a000b3c0b1928e -
# openssl rsa -in privkey.pem -noout -modulus -passin pass:lteb593 | md5sum
92e88d0b38fe93cd41a000b3c0b1928e -
Both keys have the same modulo in them, thus, they are the private and public parts of the same key. Excellent! ![]()
Credits go (as usual) to Mr. Ronkainen for his hard work in hacking the B593. Also Mr. Olesen deserves thanks for his ready-made tool (which btw. builds in my Linux easily) for putting the PEM-parts back together.
Final credits go to Huawei engineers, this time they took data encryption really seriously. However, when you're in a leaking boat, it really doesn't matter if you have the best motor or not, your boat still leaks. In this case the critical information (like encryption keys) are hard-coded, used in every device they manufacture and recoverable in plain-text format. It looks like Huawei is suffering from the weakest-link-in-your-security -syndrom. If your FTP is flakey, you store your SSH-passwords in plain-text format and let people in as they please, they are likely to find this stuff out!
... More to follow about SSH and web-GUI user password encryption. This was a very critical find in the path of full disclosure.
Password encryption
Sunday, August 17. 2014
A fellow B593 hacker Mr. Ronkainen from blog.asiantuntijakaveri.fi informed me about his findings regarding /var/curcfg.xml password encryption. This is something I did already spit-ball with him in comments, but this time he had something concrete to show.
This is for decrypting an FTP-password. Since you can set your own, you definitely know what the plaintext password is. His findings are:
exe->Data_DbDecrypt(nil, "llxYjYnY:\021\003\2324\275\241\233Wu\353$Vx;\333#", "", "" <unfinished ...>
exe->strncpy(0x7facddd8, "llxYjYnY", 8) = 0x7facddd8 (Data_DbDecrypt)
exe->strcpy(0x7facdaf8, "12345678") = 0x7facdaf8 (Data_getProductInfo)
exe->strncpy(0x7facdb01, "12345678", 9) = 0x7facdb01 (Data_getKey)
exe->strncat("12345678", "llxYjYnY") = "12345678llxYjYnY" (Data_getKey)
<... Data_DbDecrypt resumed> ) = nil
exe->strcpy(0x4ce009, "BBBB") = 0x4ce009
The first call is for the raw input data. It clearly contains 8 characters, a colon (:) and something encrypted after it. Then there is a surprising part, call to a function named Data_getProductInfo() returning hard-coded 12345678 every time. Based on the code, the "product info" is simply concatenated into the Base64-decoded 8 char prefix, forming a 16 byte encryption key.
I've already speculated, that they changed encryption in SP100+ from 3-DES to AES. Based on the function names in firmware libries, combine that with knowledge of block ciphers and give it a go with AES-128 ECB with the above keying. Hey presto! It works! ![]()
I wrote a public tool for doing password encryptions/decryptions: http://blog.hqcodeshop.fi/B593/password_recover.php The sources for my web-thing are also there, if you want to use that by yourself.
As you can see from the form, I cannot work with the previous 3-DES stuff. It's simply because I don't know what the key/IV are. There is also another thing with web-GUI and SSH-passwords. They are not using the above keying mechanism. My speculation is, that they are using AES-256 (possibly in ECB-mode) for those, but I have no details about the key.
If you want to test the password recovery, you'll need your /var/curcfg.xml at hand. Pick an encrypted password from that, for example:
<X_FTPServiceInstance InstanceID="1" Username="test" Password="bU50RkQ1T2o6UNkuA7Bdj40/TiNehA6fDw==" FtpUserEnable="1" Privilege="2" Path="usb2_1/../.."/>
or
<WEPKeyInstance InstanceID="4" WEPKey="bU50RkQ1T2o69goRBo2nWOh00YDVCHLGDw=="/>
Select web-form Target as FTP-user, copy/paste the value from XML Password-field into Base64-encoded and klick decrypt. It should give you "test" as Plain-text value. There is another example for Wi-Fi WPA-key, it says WEP in the XML-file, but we can ignore that.
I'll keep investigating the other passwords too. Mr. Ronkainen suggested, that something in the box could be encrypted with PKCS#1, but the block size is off, at least in passwords. Stay tuned for more updates.
Huawei B593 u-12 firmware spreadsheet
Tuesday, July 15. 2014
Since there has been no updates for Mr. Bjørn Grønli's spreadsheet, I chose to continue his work.
The link is https://docs.google.com/a/hqcodeshop.fi/spreadsheets/d/1ZJsy0q-8tmR8m32d1bCHkSv1neGVtA5v5TU4qVczH0Q
I did try out a number of SP104 and SP105 T-mobile (German Telecom) firmwares and found that they are really poor. 3 Italy was a pretty poor firmware, as I had problems logging in! Polkomtel's SP103 was a solid performer, but after a round trip, I went back to Telia's SP102.
Please drop me a comment if something is wrong or new columns should be added, or if I'm missing a firmware in the list. My idea is to try to keep this up to date with firmware information and I will appreciate any help from you.
Running AT-commands on your B593
Thursday, May 29. 2014
This is something I've wanted to do for a long time. Ever since I got my B593. Jevgenij has been hacking his B593 and dropped me a comment that he found command /bin/lteat from his box. Obviously I had to SSH into mine to confirm this:
# ssh admin@192.168.1.1 /bin/sh
admin@192.168.1.1's password:
-------------------------------
-----Welcome to ATP Cli------
-------------------------------
ATP>shell
BusyBox vv1.9.1 (2013-07-25 14:10:15 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# ls -l /bin/lteat
-rwxrwxrwx 1 0 0 34604 /bin/lteat
... and oh yes! Such a command is there. It is an interactive AT-command shell!
Warning!
Running these AT-commands will mess up with your box. The modem does not like to be messed up and my box didn't connect to internet after doing this. There is a simple fix to just reboot the router.
Let's explore some possibilities.
Manufacturer information
Running the AT-command shell:
# lteat
AT>
This is something that worked already in the 80s modems. The classic modem information:
AT>ati
Manufacturer: Huawei Technologies Co., Ltd.
Model: EM920
Revision: 11.433.61.00.07
IMEI: 868031008680310
+GCAP: +CGSM,+DS,+ES
OK
The 15-digit IMEI is broken into two pieces. First 8 numbers are the Type Allocation Code (or TAC). The second part is the 7 number unique id of my unit. That's why I'm not revealing it here.
If we punch the TAC into a http://www.nobbi.com/tacquery.php it will yield a result of:
86803100
Manufacturer = Huawei
Model = B593
Hints = LTE/UMTS Router
Which is not very surprising. That is something we already know.
Telco information
Let's see what we can get from my telco. I found a nice reference List of AT commands to be very helpful. Running command:
AT>AT+COPS=3,2
AT+COPS=3,2
OK
AT>AT+COPS?
AT+COPS?
+COPS: 0,2,"24405",2
OK
The 24405 is my PLMN code (note: this can be found from web GUI's diagnostics wireless status also). According to article Mobile country code, it breaks down to two parts:
Mobile Country Code = MCC = 244
Mobile Network Code = MNC = 05
According to the table:
MCC = 244 = Finland
MNC = 05 = Elisa
Again, something that I already know.
Location information
To dig a bit deeper ... Every cell tower has unique code. I found information about that from a discussion forum with topic Huawei USB LTE Modem, E3276 K5150 E398 (Modems). The forum says that:
AT+CREG?
+CREG: 2,1, YYYY, XXXXX, 2
OK
Y = LAC
X = Cell ID
Added: Note that both are in hex so need to convert it
Let's try that one out:
AT>AT+CREG=2
AT+CREG=2
OK
AT>AT+CREG?
AT+CREG?
+CREG: 2,1, 620C, 123ABC, 2
OK
Now we have:
LAC = 620C (hex) = 25100 (decimal)
Cell ID = 123ABC (hex) = 1194684 (decimal)
Again, I'm not going to reveal my exact location here! ![]() The cell-ID published here is something I made up.
The cell-ID published here is something I made up.
I tested all the gathered information of:
MCC = 244
MNC = 05
LAC = 25100
cell-ID = 1194684
in OpenCellID's search engine, but they don't seem to have my coordinates in it. Maybe I should add them. Your's may very well be there.
According to Wikipedia article, there are a number of databases for cell-IDs, but most of them are commercial and I don't have a license to use them. In general they simply have exact GPS-coordinates of cell towers and they can be used to get a rough estimate of your location.
Signal quality
The last one I did was to get exact signal quality. A B593 has 5 bars in it, which is accurate enough for most users. The hardware has the quality info in much more detailed level. The AT-command list says:
Signal quality
Command: AT+CSQ
Response: +CSQ: <rssi>,<ber>
Let's try that out:
Query for the ranges:
AT>AT+CSQ=?
AT+CSQ=?
+CSQ: (0-31,99),(0-7,99)
OKQuery for the signal quality:
AT>AT+CSQ
AT+CSQ
+CREG: 1, 620C, 123AC1, 2
AT+CSQ
+CSQ: 23,99
OK
Whoa! It also returned a LAC and another cell-ID. The cell-ID is pretty close to the original one, but not exactly the same. Anyway, the Received signal strength indication (RSSI) is 23 and Bit Error Rate (BER) is 99.
By Googling I found out following information about RSSI:
RSSI (dBm) = RSRP + 10*log10(RB) + | RSRQ | + other noice, temperature noice etc.
You may also see the RSSI vs RSRP: A Brief LTE Signal Strength Primer for details about the signal math.
To put all the logarithms and four-letter-acronyms into layman terms. This table was published in the discussion forum in Finnish by user with nickname timtomi. Signal levels are from poor to excellent:
| 0 | <-113 dBm | poor, signal breaks up and all kinds of nasty |
| 1 | -111 dBm | poor, signal breaks up and all kinds of nasty |
| 2 | -109 dBm | works, but signal fluctuates, especially upload |
| 3 | -107 dBm | works, but signal fluctuates, especially upload |
| 4 | -105 dBm | works, but signal fluctuates, especially upload |
| 5 | -103 dBm | works, but signal fluctuates, especially upload |
| 6 | -101 dBm | works, but signal fluctuates, especially upload |
| 7 | -99 dBm | still better than ADSL |
| 8 | -97 dBm | still better than ADSL |
| 9 | -95 dBm | still better than ADSL |
| 10 | -93 dBm | still better than ADSL |
| 11 | -91 dBm | still better than ADSL |
| 12 | -89 dBm | full download, good upload |
| 13 | -87 dBm | full download, good upload |
| 14 | -85 dBm | full download, good upload |
| 15 | -83 dBm | full download, good upload |
| 16 | -81 dBm | full download, good upload |
| 17 | -79 dBm | excellent! good signal and ping |
| 18 | -77 dBm | excellent! good signal and ping |
| 19 | -75 dBm | excellent! good signal and ping |
| 20 | -73 dBm | excellent! good signal and ping |
| 21 | -71 dBm | excellent! good signal and ping |
| 22 | -69 dBm | excellent! good signal and ping |
| 23 | -67 dBm | excellent! good signal and ping |
| 24 | -65 dBm | excellent! good signal and ping |
| 25 | -63 dBm | excellent! good signal and ping |
| 26 | -61 dBm | excellent! good signal and ping |
| 27 | -59 dBm | you're right next to the cell tower! |
| 28 | -57 dBm | you're right next to the cell tower! |
| 29 | -55 dBm | you're right next to the cell tower! |
| 30 | -53 dBm | you're right next to the cell tower! |
| 31 | > -51 dBm | you're right next to the cell tower! |
| 99 | |
not known or not detectable |
The BER is typically 99 which means that none could be measured. In general there shouldn't be any errors in the transmission, so 99 is likely what you'll get also.
Telia Sweden SP102 firmware for u-12
Tuesday, May 27. 2014
Jevgenij dropped me a comment about new firmware. It is from Telia Sweden and you can get it from here http://www.telia.se/privat/support/mobiltbredband/uppdaterausbmodemorouter#huaweib593formac=&tabMenu_0=huaweib593formac The direct download link is https://www.telia.se/dms/mgnl-ext-dms/www-telia-se-ui/installation-files/se_telia_r-m-h-s.tar/se_telia_r-m-h-s.tar.bz2 The firmware seems to have nice features, SMS and even to force for 2G-operation. He highly recommends this one. This looks very promising, perhaps I'll try this myself.
I upgraded my B593 with this one and can confirm that it works well. GUI-languages are: Svenska, Suomi, Pусский, Norsk, Dansk, Eesti, Lietuviu and Latviešu. No setup wizard. Has external antenna support. No VoIP. No DDNS. Mode selector has 5 options: auto, auto 3G/4g, 2G only, 3G only and 4G only. SMS in/out. No DLNA. So it is little bit light on features, but is fully exploitable and SP102!
The file will contain a SP102 for u-12. Altough The Exploit does not work, it seems to have a nice bug in it. When you're FTPing into it, it will open also SSH-port! Whaat! ![]()
Warning:
SSH passwords are reset to something the telco set. However, USB/FTP-hack will work and you can get the /var/sshusers.cfg and look at the plaintext password from there.
Extracting /var/curcfg.xml from NVRAM [Solved!]
Wednesday, May 21. 2014
John do, a reader of this blog made a serious break-trough! Via SSH on B593 prompt, he found the flashtest-command. Before this I had no knowledge about such command, but see what I can do with this new information:
# flashtest
Usage: flashtest {info|read|write|erase|export|load} {addr} {len} [data]
Format:
flashtest help
flashtest info
flashtest read addr len
flashtest write addr len {data}
flashtest erase addr len
flashtest export addr len
Well ... the info sound interesting. Let's see:
# flashtest info
flash block size : 0x40000 (256k Bytes)
flash block num : 0x40 (64 Blocks)
flash total size : 0x1000000 (16M Bytes)
flash partation info :
---------------------------------------------------------------
Name Address Usage
---------------------------------------------------------------
Boot 0x0---0x40000 Bootloader
Image 0x40000---0xA40000 Main image
Image 0xA40000---0xE00000 Subject image
Curcfg 0xE00000---0xE40000 Curcent config
Faccfg 0xE40000---0xE80000 Factury config
Tmpcfg 0xE80000---0xF00000 Temp config
Fixcfg 0xF00000---0xF40000 Fixed config
Logcfg 0xF40000---0xF80000 Log config
TR069 0xF80000---0xFC0000 TR069 cert
Nvram 0xFC0000---0xFFFFFF Nvram
Current config! Really!? (Mis-typed as Curcent config). The run-time -only /var/curcfg.xml's real storage has eluded me this far. Let's explore that further:
# flashtest export 0xE00000 65536
Read data: addr = 0xe00000, len = 0x10000 ...
Begin write to file
Export done
What did it do? Where it wrote to? Some poking around reveals:
# cd /tmp/
# ls -l
---------- 1 0 0 65536 flashinfo.bin
Oh yes! The next thing is to get my hands on to the file. In the B593 firmware's Busybox there is only a limited set of tools.
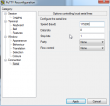
Let's use the USB/FTP-hack for transferring the file. The idea is to plug an USB-stick into B593. Any FAT32-formatted stick will do, it is totally irrelevant if there are files or not. Early firmwares are known to have a flaw in them. You can mount the entire filesystem into FTP-server and transfer file to/from the box. Setup goes like this:![]()
Make sure you have the FTP-server running, add a user to the new mount and set the directory as ../.. It is really important to do that! That effectively breaks out of /mnt/usb2_1 into /. See this pic:![]()
I added user with name test. Now let's see if the FTP-connection works from an external machine:
# ftp 192.168.1.1
Connected to 192.168.1.1 (192.168.1.1).
220 bftpd %v at 192.168.1.1 ready.
Name (192.168.1.1:user): test
331 Password please.
Password:
230 User logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> cd /tmp
250 OK
ftp> dir
227 Entering Passive Mode (192,168,1,1,166,124)
150 BINARY data connection established.
---------- 1 0 0 65536 May 21 19:26 flashinfo.bin
226 Directory list has been submitted.
ftp>
Oh yes! The extracted NVRAM-binary is there. Let's download it:
ftp> get flashinfo.bin
local: flashinfo.bin remote: flashinfo.bin
227 Entering Passive Mode (192,168,1,1,144,190)
150 BINARY data connection established.
226 File transmission successful.
65536 bytes received in 0.06 secs (1092.41 Kbytes/sec)
A brief analysis of the file reveals:
# hexdump -C flashinfo.bin | head -3
00000000 3e 00 64 fe 3c 3f 78 6d 6c 20 76 65 72 73 69 6f |>.d.<?xml versio|
00000010 6e 3d 22 31 2e 30 22 20 3f 3e 0a 3c 49 6e 74 65 |n="1.0" ?>.<Inte|
00000020 72 6e 65 74 47 61 74 65 77 61 79 44 65 76 69 63 |rnetGatewayDevic|# hexdump -C flashinfo.bin | tail -5
000064f0 65 77 61 79 44 65 76 69 63 65 43 6f 6e 66 69 67 |ewayDeviceConfig|
00006500 3e 0a 00 ff ff ff ff ff ff ff ff ff ff ff ff ff |>...............|
00006510 ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff |................|
*
00010000
The first 4 bytes of 3e 00 64 fe are bit of a mystery. I don't know what the 3e 00 is for, but the 64 fe is obvious! It is the length of the XML-file following the header bytes. I can confirm that the entire /var/curcfg.xml is there. Unchanged. Intact!
My next move is to try altering the curcfg.xml and write it back. There is a chance of locking myself out of my own B593, so ... I need to be really careful with this. If everything works as I expect, my next move is to write tools for allowing people to access their devices as they want to.
I'd like to extend my gratitude to Mr. John do. This really is ground-breaking stuff allowing us to new lengths with Huawei B593 hacking. Thank you, sir!
Huawei B593 different models revisited: u-12 vs s-22
Friday, May 16. 2014
This is something that has been bugging me since November. In my post about different models, I stated that I have a u-12 (and still do). Last year I did setup a s-22 to a friend and got to see that it is pretty much the same. However, "pretty much the same" is not exactly the same.
The s-22 is a newer model and it has been well established, that it has a TDD 2600 MHz added into it. All the FDD frequencies are exactly the same than in u-12.
In the comments of my post, a user suggested that s-22 differs from u-12 by having only one USB-connector. At the time I was unable to find proof of that, all the pictures I could found of alleged s-22 units had no difference for a u-12 unit.
Now the situation has changed. In my ventures of the wonderful Internet I found an article What's the difference between HUAWEI B593s-22 and B593u-12? and it has a picture of both units side by side in it. Nice! But which one is which?
Just to make sure that s-22 is in the left and u-12 is in the right, I'll post a fresh picture of my own u-12 unit:![]()
Also to close the case I also found a vendor page with a nice picture of s-22 in it, see HUAWEI B593s-22 4G LTE CPE [B593s-22]. It has a picture of the unit in the page, and their s-22 looks exactly the same than the left unit in the picture, and exactly NOT the same than my u-12. Apparently s-22 does not have a power switch, it lacks the side USB-connector and SIM-card -slot has been changed into a tray. Lot of differences to spot, actually.
So I'm confident that s-22 is very much re-designed both in hardware and firmware. The hardware side is surely changed because of the new(ish) 4G TDD radio interface. And while Huawei engineers were at it, they changed also the firmware in number of ways, one of them being to resist hacking attempts better than their 1st gen version did. This is also a well established fact, s-22 firmware has a completely different structure than u-12 firmware.
Now me and everybody else should be able to identify the units by a simple visual inspection.
German Telekom SP104/SP105 firmware for u-12
Thursday, May 15. 2014
I got a comment from John, he told me that a telco in Germany called Telekom has SP104 firmware out for B593 u-12. They seem to call it Speedport LTE II. The download link to the firmware is http://hilfe.telekom.de/dlp/eki/downloads/Speedport/Speedport%20LTE%20II/Firmware_Speedport_LTE_II_V100R001C748SP104.zip
The UI has English language, so it should be usable for us non-German speaking users too.
As usual, I did download and extract the firmware and all looks ok to me. Also as usual, I didn't test it. If you do, please comment how it went.
Update 21th May 2014:
Today John told me that, Telekom released a security update SP105 firmware. There is little information what the fix is, but you can get the lates from this link http://www.telekom.de/dlp/eki/downloads/Speedport/Speedport%20LTE%20II/Firmware_Speeport_LTE_II_B593u-12_V100R001C748SP105.zip




