iPhone Mobile Profile for a new CA root certificate - Case CAcert.org
Friday, April 20. 2018
Year ago, I posted about CAcert root certificate being re-hashed with SHA-256 to comply with modern requirements. The obvious problem with that is, that it is not especially easy to install own certificates (or the new CAcert root) into a phone anymore.
When you try to access your mail server (or any other resource via HTTPS), the result will be something like this:
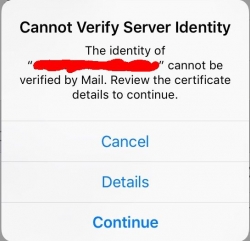
Not very cool. Getting the "Cannot Verify Server Identity" -error. This is especially bad, because in modern iOS you really don't have a clue how to get the new root cert installed and trusted. No worries! I can describe the generic process here.
Apple Configurator 2
Get it from https://itunes.apple.com/us/app/apple-configurator-2/id1037126344. Install it into your Mac. It doesn't cost anything, but will help you a lot!
If you dream on running it on a Windows/Linux/BSD, just briefly visit your nearest Mac-store and with your newly purchased Mac start over from the part "Get it from..."
Root certificate to be installed
Get a root certificate you want to distribute as trusted root CA. With the Apple Configurator 2, create a profile containing only one payload. The certificate in question.
This is what it would look like:
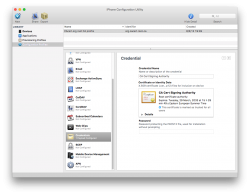
When that mobile profile is exported from Apple Configurator 2, you will get an unsigned .mobileconfig-file. That will work, but just give grievance during install-time about not being unsigned. If you can live with an extra notice, then just go to next step. If you cannot, get a real code-signing -certificate and sign your profile with that.
Publishing your .mobileconfig from a web server
Your precious .mobileconfig-doesn't just automatically fly into your iOS-device, you need to do some heavy lifting first.
On your favorite web-server, which can be accessed from your iOS-device and you can fully control, place the .mobileconfig-file there as a static resource and make it have content-type application/x-apple-aspen-config.
On Apache:
AddType application/x-apple-aspen-config .mobileconfig
On Nginx:
types {
application/x-apple-aspen-config mobileconfig;
}
Testing the content-type setting with curl:
# curl --verbose "https:...."
> User-Agent: curl/7.32.0
>
< HTTP/1.1 200 OK
< Content-Type: application/x-apple-aspen-config
Install the profile into your iOS-gadget
That's simple: just whip up Mobile Safari and surf to the URL. Given the correctly set content-type, it will launch profile installer:

During the process you will need to punch in your PIN-code (if you're using one in your device). There are way too many confirmations, if you really, really, for sure want to install that particular profile. The questions are there for a very good reason. A mobile profile can contain a combination of settings that will eventually either leave you powerless to control your own device, or alternatively allow remote control of your very own device. Or both. So, be very careful when installing those mobile profiles!
Finally
Now you have your new root certificate installed and trusted. Go test it!
For those who are very brave:
My recommendation is not to do this. Do not trust me or my published files!
I have published my own .mobileconfig into the web server of this blog. The address for the profile is:
https://blog.hqcodeshop.fi/CAcert/CAcert.org%20root%20CA%20profile.mobileconfig
I'll repeat: That is there for your reference only. Do not trust me for such a security-sensitive file.

