New toys: iPhone 8
Wednesday, April 25. 2018
Whenever there are new toys, I'm excited! Now that I have new iPhone 8, there is no other way to phrase it: it IS same as 7, which was same as 6. The observation Woz pointed out when X and 8 came out:
I’m happy with my iPhone 8 — which is the same as the iPhone 7, which is the same as the iPhone 6, to me.
Last year around this time, I wasn't especially impressed when I got my 7. See and/or read it at /archives/345-New-toys-iPhone-7.html. This year, I'm kinda hoping to still have my 6. The good part is, that I won't have to pay for these toys myself. If I would, I would be really really disappointed.
An end is also a beginning
Tuesday, April 24. 2018
Today, I had my last day at King. Right now I'm toasting this fine drink to my wonderful ex-colleagues.
Next I'm taking a breather and next week starting something new back in Finland!
RFID Mifare Classic "clone"
Saturday, April 21. 2018
Toying around with RFID, tags has always been something I wanted to do, but never had the time. Contactless payment is gaining traction all around the world. The reason is very simple: it is fast and convenient for both the customer and vendor to just touch'n'go with your credit card or mobile phone on a point-of-sale.
Credit/Debit card payments are based on EMV, or Europay MasterCard and Visa, standard. See generic EMV info at https://en.wikipedia.org/wiki/EMV. Back in 2011 Visa started driving the contactless standard worldwide, and given the situation today, their efforts paid off. However, my understanding is, that at the time of writing this, regardless number of people attempting it, there are no known vulnerabilities in the contactless EMV. Finding one, would be sweet, but finding one would also be extremely hard and time consuming. So, I decided to go for something easier. MIFARE Classic.
What's this RFID, isn't it NFC?
Short answer: yes and no.
This infographic is courtesy of atlasRFIDstore
http://blog.atlasrfidstore.com/rfid-vs-nfc
MIFARE Classic info
Since this topic isn't especially new, I'm just posting some useful sites I found to be very useful when doing RFID-hacks:
- Finding the encryption keys:
- Cloning the tag:
- Information about Mifare Classic encryption key hacking:
- ISO/IEC 14443 Type A generations:
Going to eBay for the hardware
I had a real-world RFID -tag, and wanted to take a peek into it. For that to happen, I needed some hardware.
The choice for reader/writer is obvious, an ACR122. Info is at: https://www.acs.com.hk/en/products/3/acr122u-usb-nfc-reader/. The thing costs almost nothing and is extremely well supported by all kinds of hacking software.
Going to GitHub for the software
All the software needed in this project can be found from GitHub:
- libusb, https://github.com/libusb/libusb
- Some software want libusb 0.1 some 1.0. I had only 0.1 installed so I had to compile the latest also.
- libnfc, https://github.com/nfc-tools/libnfc
- Latest installed
- MiFare Classic Universal toolKit, mfcuk, https://github.com/nfc-tools/mfcuk
- Installed, because it has Mifare Classic DarkSide Key Recovery Tool. This is an advanced approach into cracking the encryption keys.
- mfoc, https://github.com/nfc-tools/mfoc
- offline nested attack by Nethemba
- This is the one, NXP tried to prevent the hack to be publicly released, see info from https://www.secureidnews.com/news-item/nxp-sues-to-prevent-hackers-from-releasing-mifare-flaws/
- Creating an own encryption algorithm and expecting nobody to figure out how it works will work for a very short period of time. Going to a judge to prevent the information from leaking also works... if you're high on something!
 But on real life it works never.
But on real life it works never.
All of the above software was installed with ./configure --prefix=/usr/local/rfid to avoid breaking anything already installed into the system.
Running the tools
Basic information from the tag (the actual tag UID is omitted):
# nfc-list
NFC device: ACS / ACR122U PICC Interface opened
1 ISO14443A passive target(s) found:
ISO/IEC 14443A (106 kbps) target:
ATQA (SENS_RES): 00 04
UID (NFCID1): 11 22 33 44
SAK (SEL_RES): 08
ATQA 00, 04 is listed in ISO/IEC 14443 Type A generations and is identified as MIFARE Classic. Goody! It's weak and hackable.
Just running mfoc to see if a slow attack can proceed:
# mfoc -O card.dmp
Found Mifare Classic 1k tag
ISO/IEC 14443A (106 kbps) target:
ATQA (SENS_RES): 00 04
UID size: single
bit frame anticollision supported
UID (NFCID1): 11 22 33 44
SAK (SEL_RES): 08
Not compliant with ISO/IEC 14443-4
Not compliant with ISO/IEC 18092
Fingerprinting based on MIFARE type Identification Procedure:
MIFARE Classic 1K
MIFARE Plus (4 Byte UID or 4 Byte RID) 2K, Security level 1
* SmartMX with MIFARE 1K emulation
And very soon, it results:
We have all sectors encrypted with the default keys..
Auth with all sectors succeeded, dumping keys to a file!
WHAAT! The card wasn't encrypted at all! ![]()
A closer look into card.dmp reveals, that there was no payload in the 1024 bytes this particular MIFARE Classic stored.
Since, the card doesn't have any payload, the application has to work based on childish assumption, that the UID of a RFID-tag cannot be changed. Nice! Because it can be set to whatever I want it to be! Like this:
# nfc-mfsetuid 11223344
NFC reader: ACS / ACR122U PICC Interface opened
Found tag with
UID: 01234567
ATQA: 0004
SAK: 08
My blank UID-writable tag had UID of 01 02 03 04, but I changed it into something else. Note: This is not allowed by the specs, but using very cheap eBay-hardware, obviously it can be done! Nice. ![]()
To verify my hack:
I walked into the appliation and used my clone successfully. Also, I informed the owners, that their security is ... well ... not secure. ![]() They shouldn't use UIDs as the only authentication mechanism. It's only 4 bytes and anybody in the world can use that 4-byte password. Using encrypted payload would make more sense, if MIFARE Classic wouldn't have a major security flaw in it's key generation algorithm.
They shouldn't use UIDs as the only authentication mechanism. It's only 4 bytes and anybody in the world can use that 4-byte password. Using encrypted payload would make more sense, if MIFARE Classic wouldn't have a major security flaw in it's key generation algorithm.
This was one of the easiest hacks I've completed for years.
iPhone Mobile Profile for a new CA root certificate - Case CAcert.org
Friday, April 20. 2018
Year ago, I posted about CAcert root certificate being re-hashed with SHA-256 to comply with modern requirements. The obvious problem with that is, that it is not especially easy to install own certificates (or the new CAcert root) into a phone anymore.
When you try to access your mail server (or any other resource via HTTPS), the result will be something like this:
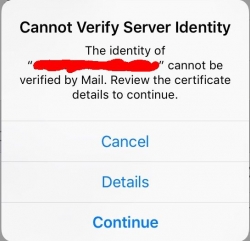
Not very cool. Getting the "Cannot Verify Server Identity" -error. This is especially bad, because in modern iOS you really don't have a clue how to get the new root cert installed and trusted. No worries! I can describe the generic process here.
Apple Configurator 2
Get it from https://itunes.apple.com/us/app/apple-configurator-2/id1037126344. Install it into your Mac. It doesn't cost anything, but will help you a lot!
If you dream on running it on a Windows/Linux/BSD, just briefly visit your nearest Mac-store and with your newly purchased Mac start over from the part "Get it from..."
Root certificate to be installed
Get a root certificate you want to distribute as trusted root CA. With the Apple Configurator 2, create a profile containing only one payload. The certificate in question.
This is what it would look like:
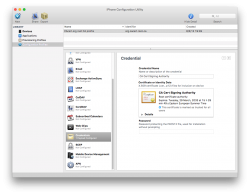
When that mobile profile is exported from Apple Configurator 2, you will get an unsigned .mobileconfig-file. That will work, but just give grievance during install-time about not being unsigned. If you can live with an extra notice, then just go to next step. If you cannot, get a real code-signing -certificate and sign your profile with that.
Publishing your .mobileconfig from a web server
Your precious .mobileconfig-doesn't just automatically fly into your iOS-device, you need to do some heavy lifting first.
On your favorite web-server, which can be accessed from your iOS-device and you can fully control, place the .mobileconfig-file there as a static resource and make it have content-type application/x-apple-aspen-config.
On Apache:
AddType application/x-apple-aspen-config .mobileconfig
On Nginx:
types {
application/x-apple-aspen-config mobileconfig;
}
Testing the content-type setting with curl:
# curl --verbose "https:...."
> User-Agent: curl/7.32.0
>
< HTTP/1.1 200 OK
< Content-Type: application/x-apple-aspen-config
Install the profile into your iOS-gadget
That's simple: just whip up Mobile Safari and surf to the URL. Given the correctly set content-type, it will launch profile installer:

During the process you will need to punch in your PIN-code (if you're using one in your device). There are way too many confirmations, if you really, really, for sure want to install that particular profile. The questions are there for a very good reason. A mobile profile can contain a combination of settings that will eventually either leave you powerless to control your own device, or alternatively allow remote control of your very own device. Or both. So, be very careful when installing those mobile profiles!
Finally
Now you have your new root certificate installed and trusted. Go test it!
For those who are very brave:
My recommendation is not to do this. Do not trust me or my published files!
I have published my own .mobileconfig into the web server of this blog. The address for the profile is:
https://blog.hqcodeshop.fi/CAcert/CAcert.org%20root%20CA%20profile.mobileconfig
I'll repeat: That is there for your reference only. Do not trust me for such a security-sensitive file.
DynDNS updates to your Cloud DNS
Sunday, April 15. 2018
People running servers at home always get dynamic IP-addresses. Most ISPs have a no-servers -clause in their terms of contract, but they really don't enforce the rule. If you play a multiplayer on-line game and have voice chat enabled, you're kinda server already, so what's a server is very difficult to define.
Sometimes the dynamic IP-address does what dynamic things do, they change. To defeat this, people have had number of different approaches to solve the problem. For example, I've ran a DHIS-server (for details, see: https://www.dhis.org/) and appropriate client counterpart to make sure my IP-address is properly updated if/when it changes. Then there are services like Dyn.com or No-IP to do exactly the same I did with a free software.
The other day I started thinking:
I'm already using Rackspace Cloud DNS as it's free-of-charge -service. It's heavily cloud-based, robust and has amazing API to do any maintenance or updates to it. Why would I need to run a server to send obscure UDP-packets to to keep my DNS up-to-date. Why cannot I simply update the DNS-record to contain the IP-address my server has?
To my surprise nobody else thought of that. Or at least I couldn't find such solutions available.
A new project was born: Cloud DynDNS!
The Python 3 source code is freely available at https://github.com/HQJaTu/cloud-dyndns, go see it, go fork it!
At this point the project is past prototyping and proof-of-concept. It's kinda alpha-level and it's running on two of my boxes with great success. It needs more tooling around deployment and installation, but all the basic parts are there:
- a command-line -utility to manage your DNS
- an expandable library to include any cloud DNS-provider, current version has Rackspace implemented
- systemd service descriptions to update the IP-address(es) at server boot, it really supports multiple network interfaces/hostnames on a same server
Any comments/feedback is appreciated. Please, file the bug reports directly to GitHub-project.
Book club: The Stupidity Paradox - The Power and Pitfalls of Functional Stupidity at Work
Saturday, April 7. 2018
Human stupidity has always intrigued me. It is, after all, the driving force of this world. Most people will disagree with me and say, the driving force being money or sex or ... whatever. But take my word for it, it is stupidity! All you have to to is look around and realize, that stupid clowns get elected to powerful positions in democratic systems, idiots are disputing easily proven scientific facts and as an example are claiming that world is flat. Also in our everyday life we do stupid things just because "we always have done so". So, it is stupidity that drives you! People in general are not designed to make critical observations, instead we wired to crowd-behave in a socially acceptable manner. Being stupid.
When taken the context of any regular place of work, two gentlemen Mr. Alvesson and Mr. Spicer took a very close look on this phenomenon. And their book The Stupidity Paradox investigates these.

Stupidity: Entire book is written around a concept of functional stupidity. Authors define functional stupidity as:
Functional stupidity is the inclination to reduce one's scope of thinking and focus only on the narrow, technical aspects of the job.
Paradox: For an organization, just focusing on a narrow scope is often beneficial. Cutting corners makes everybody's life easier and consumes less resources, it is simply thoughtless and useful. There comes the paradox, your useful thing might be very destructive without you knowing it.
Nobody is safe from functional stupidity, especially smart people are able to wrap themselves in a "comfort zone" or a bubble, where everything they do and say appear smart. Outside the bubble, things may look a bit different.
The book describes functional stupidity inducing from five different sources:
- Leadership:
- Often leaders are deluded. They really don't have a grasp what's going on. It doesn't stop them making decisions, though.
- Structure:
- Add bureucracy. If there isn't enough information to do one's job, just add more forms to be filled and couple guidelines to get that information. What harm could dozens of contradicting guidlines and mandatory forms cause, right?
- Alternatively, just change the existing organization structure to "improve" it. Throw in couple "promotions" with really cool title and minor pay raise without actual change to the tasks to improve morale. Do this couple times and everybody will be so lost.
- Imitation:
- "Since everybody else is doing it, also we must do it". However, whatever "it" is, they may be doing it on a different context and have some kind of minor tweak in their way of doing it. Also, in reality not "everybody" does it. Such activities include typically just corporate window dressing, with little actual changes.
- Branding:
- Sometimes a consultant approaches corporate execs and tells them, that how others perceive the corporation is somehow wrong or bad. This triggers an instant imago "improvement" -campaign to make changes, which are not based on reality but merely on bullshit. Often, the results are not something you'd really want to be proud of.
- Culture:
- Getting bad news really sucks, right? Getting bad news about from your organization really really sucks, right? Easy fix: let's make a decision to never tell each other bad news! The result is a corporate culture, where you really cannot criticise anything, bring forward potential improvements or just not be able to tell, that corporation is in a downward spiral.
At the end of the book, authors cover the most important part, how to manage functional stupidity. How to detect it and how to make sure, that it doesn't cause more harm. If such a mighty force is left un-wrangled, lots of damage can be done. Ultimately the cure is simple: create a culture where smart people can observe and criticise day-to-day practices and top-level execs to take the feedback seriously. Sometimes the emperor is naked, insted of having new clothes.
Of all the vivid examples of stupidity in the book, my favorite is The Credit Crunch of 2007. Really smart (but greedy) people created a money-making-machine called CDOs. Those smart people made tons of money to themselves and to their employers, but lost the focus on the big picture. We know how that ended up.I read trough this book with a mixed feelings. Sometimes laughing out loud but at the same time felt like crying, when the description of functional stupidity ripped open old wounds.
Long live ReCaptcha v1!
Thursday, April 5. 2018
Ok. It's dead! It won't live long.
That seems to suprise few people. I know it did surprise me. ![]()
Google has had this info in their website for couple years already:
What happens to reCAPTCHA v1?
Any calls to the v1 API will not work after March 31, 2018.
Starting in November 2017, a percentage of reCAPTCHA v1 traffic will begin to
show a notice informing users that the old API will soon be retired.
Yup. This blog showed information like this on comments:
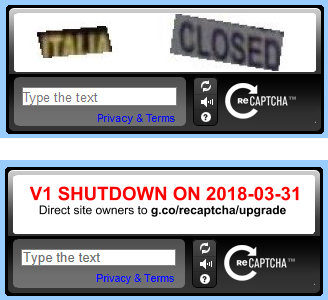
Now that the above deadline is gone, I had to upgrade S9y ReCaptcha plugin from git-repo https://github.com/s9y/additional_plugins/tree/master/serendipity_event_recaptcha. There is no released version having that plugin yet.
Now comments display the v2-style:
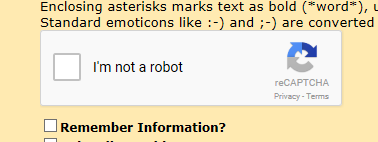
To get that running, I simply got the subdirectory of plugins/serendipity_event_recaptcha with the content from Github and went for settings:
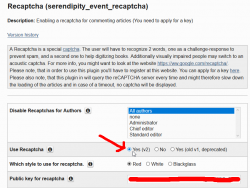
I just filled in the new API-keys from https://www.google.com/recaptcha and done! Working! Easy as pie.
Update 5th April 2018:
Today, I found out that Spartacus has ReCaptcha v2 plugin available to S9y users. No need to go the manual installation path.
Internet in a plane - Really?
Wednesday, April 4. 2018
Last week I was sitting in an aeroplane and while being bored, I flicked the phone on to test the Wi-Fi. Actually, I had never done that before and just ran a Speedtest:
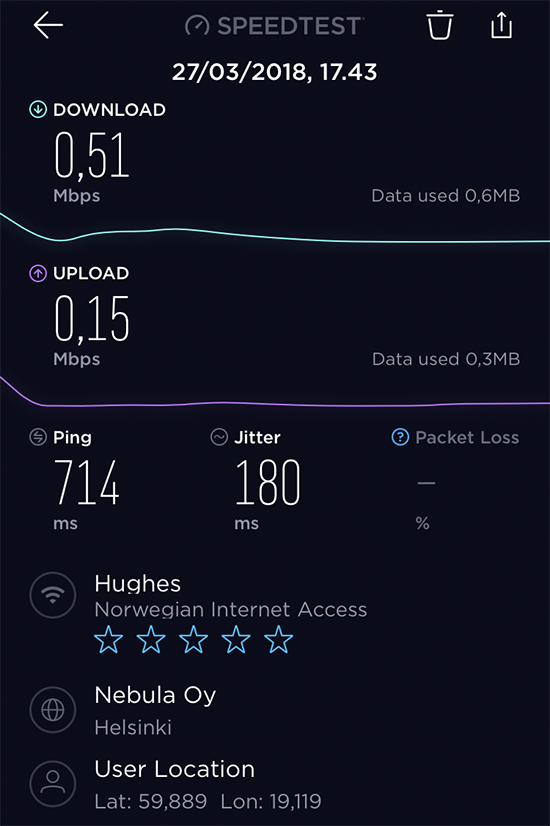
Yup. That's the reason I had never done that before. ![]()
Half a meg down, 150 up. That's like using a 56 kbit/s modem or 2G-data for Internet. Both were initially cool, but the trick ran old very fast given the "speed" or ... to be precise - lack of it.
More investigation:
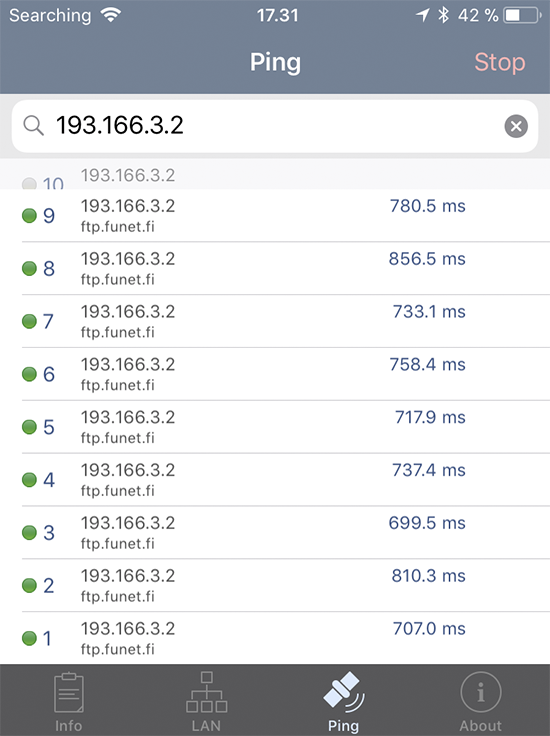
As expected, round-trip time was horrible. Definitely a satellite link. Or ... is it? But the answer to the topic's question is: no. There is no real Internet access mid-flight.
The exit IP-address was in /24 block of 82.214.239.0/24 belonging to Hughes Network Systems GmbH. I took a peek into Hughes Communications Wikipedia page at https://en.wikipedia.org/wiki/Hughes_Communications and yes. They have a German subsidiary with the same name.
After I landed and was in safe hands of a 150 Mbit/s LTE-connection, I did some more googling. Side note: When your internet access gets a 100x boost, it sure feels good! ![]()
There is a Quora article of How does Wi-Fi internet access in an airplane work? It has following diagram:
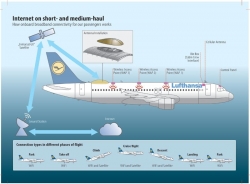
That suggests a satellite connection. Also I found The Science of In-Flight Wi-Fi: How Do We Get Internet At 40,000 Feet? from travelpulse.com, but it had some non-relevant information about a 3G-connection being used. That surely was not the case and I seriously doubt, that in Europe such a thing would be used anywhere.
Ultimately the issue was closed when I found the article Row 44 to begin installing connectivity on Norwegian's 737-800s from flightglobal.com. So, it looks like company called Row 44 does in-flight systems for commercial flights. They lease the existing infrastructure from HughesNet, who can offer Internet connectivity to pretty much everywhere in the world.
Wikipedia article Satellite Internet access mentions, that number of corporations are planning to launch a huge number of satellites for Internet access. Hm. that sounds like Teledesic to me. The obvious difference being, that today building a network of satellites is something you can actually do. Back in IT-bubble of 2001, it was merely a dream.





