Parallels Plesk Panel updated PHP versions 5.4.32, 5.5.16 and 5.6.0
Sunday, September 21. 2014
I updated all Parallels Plesk Panel PHP-versions to latest. Included in my yum-repo, there is a PHP 5.6.0 version with fully working PHP-FPM.
If something doesn't work in PHP 5.6, please drop me a comment.
iOS 8 upgrade on iPhone 4S
Saturday, September 20. 2014
Being an old geezer, I typically upgrade my iPhone firmware via USB-cable. Wireless users need to wait for the upgrade to happen, USB-people simply plug the cable and go. Also it is a very robust method and less things will go wrong than doing it wireless. Yeah, right!
So I plugged my phone in. Made sure, that I had latest iTunes version running and that a recent backup was made. Then, DÄNG!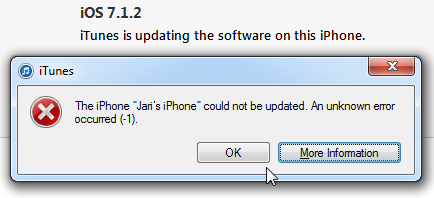
Yeah. Crap! The iPhone could not be updated. An unknown error occurred. Really? Is it possible to be more vague? Next to frustration, the next thought that goes through my mind is: "Did I brick it!!! Is it still salvageable?".
Quite soon I had a positive signal:![]()
Phew! iTunes announced, that the device is in recovery mode. Somewhere before it actually started the process, there was a question "Do you want to upgrade software and restore backup?" In reality it was a non-question, pretty much the only choice was "Ok". Looks like I didn't manage to get a screenshot of that.
The actual recovery process took a very long time. At the time I didn't realize, that it wasn't a "recovery" by definition. It was a simple iOS install. The next iTunes said was:![]()
I'm not sure if this is part of the iOS 8 kill-switch -procedure or is that a regular thing to gain Internet access via 3G, but the installation refused to continue before I had successfully entered the PIN-code for my SIM-card. Then iTunes was ready to start restoring my precious data to the device:![]()
At Apple there is a known reality distortion field, making a nice guestimate of 3 minutes for the restore time. After 15 minutes, the best guestimate was less than 1 minute. Nevertheless, I really had nothing else to but to wait for the restore to complete. Finally it said: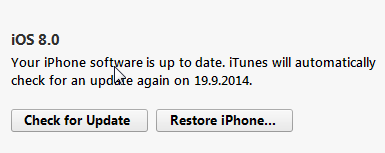
Oh yes!! I didn't brick it after all. I simply took the long route to the end.
It really wasn't worth the update. The only really noticeable thing is the voice button in messaging and the fact, that it drains my battery much faster than my previous iOS 7 did. But who would have guessed that would happen, or ... iOS 7.1 makes everything faster — including your battery drain @ 9to5mac.com. So, does that really happen every time they release an upgraded iOS-version? ![]()
Introducing curcfg_tool: Utility to make changes to your configuration
Tuesday, September 16. 2014
As I have promised a number of times to number of people. Here it finally is! The first version of my tool to alter your B593 configuration. With this tool you can change admin passwords for web GUI and SSH to something of your liking. It does not (yet) convert plaintext passwords into encrypted ones, but it successfully writes the changes to flash, thus making them permanent.
Prerequisites
- Huawei B593 u-12
- Access to your box for running commands, telnet/SSH are really good options for this
- While at Busybox sh prompt, internet connectivity via the mobile interface (4G/3G/2G)
Getting the tool
The MIPS32 binary version suitable for running at your B593 is at http://opensource.hqcodeshop.com/Huawei%20B593/curcfg/latest. The C source code is also available at: http://opensource.hqcodeshop.com/Huawei%20B593/curcfg/
- Log into your box
- (recommended) Change into directory /upgflash/
- Download the binary into your box:
wget -g -v -l curcfg_tool -r "/Huawei%20B593/curcfg/latest" opensource.hqcodeshop.com - As you can see, Busybox has a mighty quirky wget!
- Anyway, that command will download the tool from the above URL and place it to the current directory with local name curcfg_tool.
- Also note, that your box must have a functioning Internet access for download. The only other viable option is via FTP-hack. The environment is very limited and file transfers are restricted heavily.
- Make sure, that the file is executable:
chmod a+x curcfg_tool
Running the tool
Now that you have the thing sitting there, run it:
# ./curcfg_tool
Usage:
-V - Print version information
-cw <base64 encoded web gui password> - set password
-cs <base64 encoded SSH password> - set password
-w - write changes to flash (default: don't write)
-fi <file name> - input file (default: read from flash)
-fo <file name> - write changes (default: /tmp/flashinfo.bin)
An example of resetting the web-GUI password would be:
# ./curcfg_tool -cw f5338SA1kb4= -w
Read data: addr = 0xe00000, len = 0x4 ...
Begin write to file
Export done
Reading 25785 bytes of config
Read data: addr = 0xe00000, len = 0x64bd ...
Begin write to file
Export done
Writing 25785 bytes of config
/tmp/flashinfo.bin size = 25790 Bytes
Read file done
Begin write to flash
Load file done
The magicical Base64 encoded 3-DES encrypted string f5338SA1kb4= is "admin" in plain text. After a reboot (just say reboot at prompt), you can login into your web-GUI and change the password into something of your liking.
What next?
That's pretty much it as of now. If you don't like your operator designated passwords, you can change them.
How do I ...
- ... see what my current password is:
You cannot. Encryption key is not known for pre-SP100 firmware and SP100+ firmware is using double encryption with 3-DES and AES and entire flow of information is not yet known. - ... access the prompt of my box:
See B593_exploit.pl for details. - ... access the prompt of my box, but I have SP100+ firmware and don't know any of my passwords:
You cannot. Yet. Currently known exploits have been fixed preventing access.
However, in this case the real question seems to be: "How did you get your box running in the first place?" - ... run the B593_exploit.pl -tool, my Perl isn't working:
You may want to install all CPAN-modules the script requires. Also skip the Windows and use a proper computer.
u-12 pre-SP100 exploits in a single tool
Monday, September 15. 2014
I created a new tool to obsolete the classic B593cmd.pl ping-exploit tool. I wrote that one almost a year ago to run any commands on your B593. That could be used to lift IPtables restrictions or get your sshusers.cfg contents.
Now that Mr. Ronkainen found out that pre-SP100 firmwares have another flaw, which is much more simpler to exploit, I wrote a tool to combine both of them into a single package.
Neither one of these work in SP100+ firmwares, but not to worry! They have SSH-port open for full access anyway. So ... getting a SP100+ firmware into your box should be your target anyway. This tool can help you gain access to your box.
The B593_exploit.pl tool is at http://opensource.hqcodeshop.com/Huawei%20B593/exploit/latest.pl. In the top of the file there is a list of Perl-modules it requires to run. You will get the complaints, if any are missing. Usage:
./B593_exploit.pl --help
Usage: B593_exploit.pl
--help|-h This help
--run-cmd Run a command: pre SP-100 ping-exploit
to run any command via web-console
--telnet-login Login via telnet: lift IPtables firewall from telnet and login
Ping-exploit -mode
This is the classic. Run example:
./B593_exploit.pl --run-cmd 192.168.1.1 admin "iptables -nL INPUT"
There are couple of bugs fixed, it should be more robust and has --debug -mode in it.
Telnet-exploit -mode
This is the newer one. Run example:
./B593_exploit.pl --telnet-login 192.168.1.1
Attempt 1 telnetting to 192.168.1.1
BusyBox vv1.9.1 (2012-03-01 14:00:34 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# iptables -nL INPUT
Ok. It's not a full telnet-client like you'd a regular telnet to be. This emulates one with Perl's Term::Readline, so your vi won't work or tab-based command-line completion. However, it has enough power in it to allow you to run commands and display contents of the files or fiddle with your IPtables.
In my next post I'm about to release a tool for editing and storing values of your curcfg.xml. This is a prerequisite, getting to the prompt and running stuff on the prompt is a must-have.

